Cyber Security Works has discovered a new zero-day vulnerability, CVE-2020-24601 in Ignite Realtime Openfire 4.5.1. Openfire (formerly Wildfire) is a cross-platform real-time collaboration server based on the XMPP protocol. The vulnerability was discovered by CSW Security Researcher on Feb 5 2020.
Vulnerability Detection
CVE-2020-24601 was detected manually using a Burp Suite tool. A stored cross-site scripting attack allows an attacker to execute an arbitrary malicious URL via the vulnerable POST parameter searchName”, “alias” in the import certificate trusted page.
Disclosure
The vulnerability was disclosed to Openfire on Feb 5, 2020. The vendor responded and released a patch on March 6, 2020, to mitigate this vulnerability.
Timeline
| Date | Description |
| February 4, 2020 | Vulnerability discovered by CSW Security Researcher |
| February 5, 2020 | Vulnerability Reported to Vendor |
| February 6, 2020 | Vendor responded with bug tracker Links |
| February 13, 2020 | Follow up with vendor for fix release |
| March 1, 2020 | Follow up with Vendor for Fix Release |
| March 6, 2020 | Vendor responded with a released fix |
| August 20, 2020 | Request for CVE |
| August 24, 2020 | CVE Assigned |
| September 1, 2020 | CVE Published in NVD |
Vulnerability Analysis
CVE-2020-24601 is a Stored cross-site scripting vulnerability in Openfire Product (Openfire version 4.5.1). Whenever an authenticated user visits the trust store page, the script will be executed as part of the current user’s browser context.
Proof of Concept
Product: Openfire
Vendor: Ignite Realtime
Product version: Version 4.5.1
Privilege: admin
Vulnerable URL: POST request “alias” is a vulnerable parameter in the URL
http://localhost:9090/import-truststore-certificate.jsp?connectionType=SOCKET_S2S
Steps to Reproduce:
Issue: Stored Cross-Site Scripting
Step 1: Log in to the application (admin) through this URL in Firefox.
Step 2: Navigate to this URL to visit the ‘Import CA Certificate’ page.
Step 3: Add the payload “><script>alert(‘VULXSS’) </script> in ‘Alias’, enter a valid Content of Certificate file and click on Save
Step 4: Every time the user visit’s this URL, Malicious JavaScript is executed on the victim’s browser
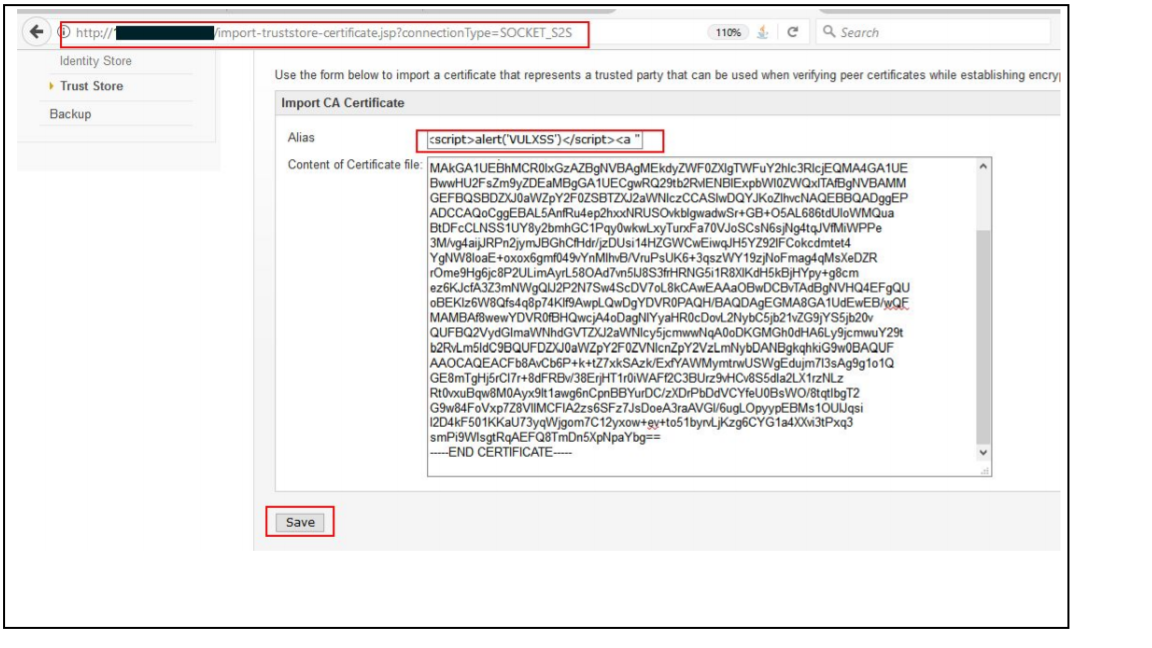
Figure 1: Import CA Certificate page with malicious Payload “><script>alert(‘VULXSS’)</script> in alias parameter
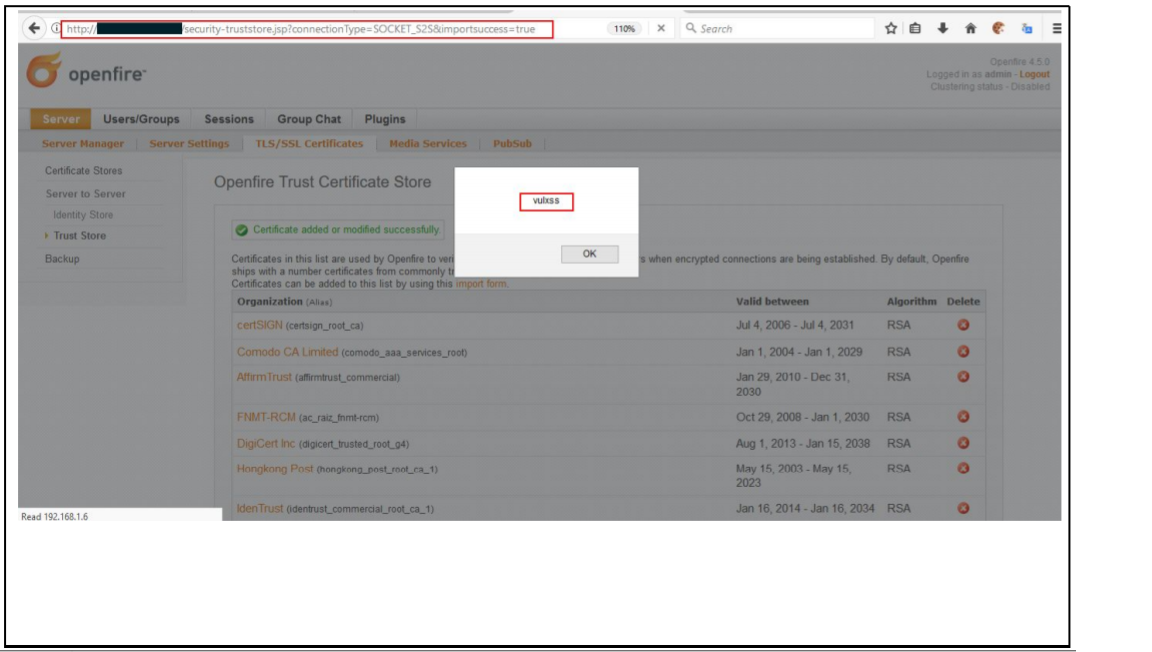
Figure 2: Malicious JavaScript Payload is executed on the victim’s browser every time this page is visited
Mitigation
We recommend the following fixes to this vulnerability
-
Perform context-sensitive encoding of untrusted input before it is echoed back to a browser by using an encoding library
-
Implement input validation for special characters on all the variables reflecting the browser and storing it in the database
-
Implement client-side validation
Impact
If this vulnerability is exploited successfully, it may result in the stealing of cookies, disclosure of end-user files, and redirection of the user to another page or site.
Recommendation
Based on the CSW team’s recommendations, Ignite Realtime Openfire executed a validation on their end and released a fix to mitigate this vulnerability.









