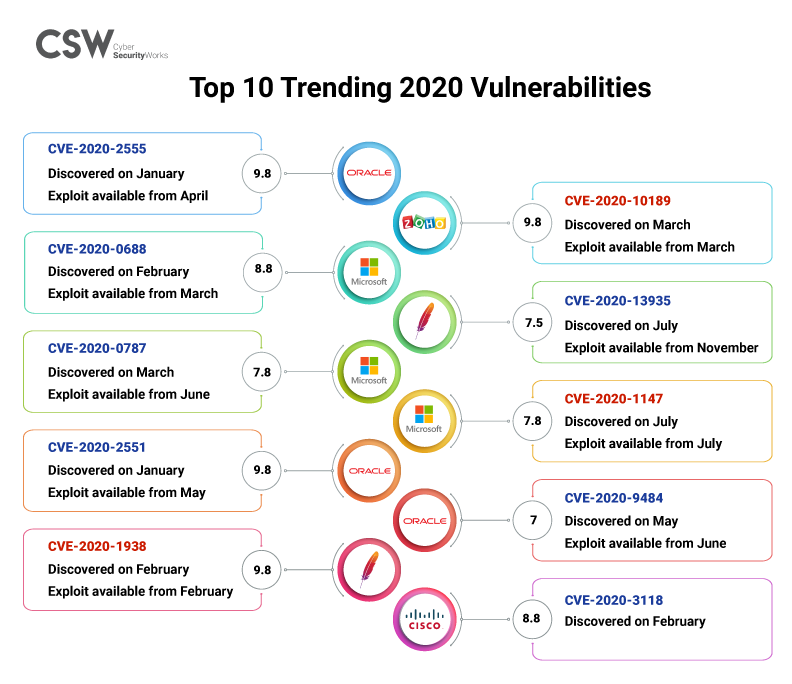
We analyzed ten vulnerabilities (discovered in 2020) that had a high search volume on google and here is what we found –
CVE-2020-10189 – a RCE vulnerability in Zoho’s Manage Engine Desktop Central is being exploited by APT41.
CVE-2020-0688 – a RCE vulnerability in Microsoft Exchange Server was exploited in March by APT group Dark Halo. They used this weakness to bypass multi-factor authentication defenses against unauthorized email access, making it easy for them to log in to SolarWinds’ trojanized update.
2020 was a productive year for threat actors. The world’s workforce is working remotely while dealing with the pandemic and threat actors were busy weaponizing critical vulnerabilities that had a global impact. Many organizations fell prey to ransomware and sophisticated cyber attacks that allowed remote and privileged access to sensitive information.
CSW analysts examined the recent vulnerabilities (discovered in 2020) with high search volume in Google and found ten weaknesses (Click here to view the table).
We sought to find out why these vulnerabilities were searched and here are our insights –
The average weaponization rate
While the average weaponization rate in 2020 is more than 45 days, four CVE’s CVE-2020-10189, CVE-2020-9484, CVE-2020-1147 and CVE-2020-0688 got weaponized under 20 days of their discovery!
While we are happy to share this insight it also begs the question as to how organizations can defend themselves without a sophisticated RBVM that would provide them this kind of dynamic trending analytics.
Two vulnerabilities exploited by APT Groups & Ransomwares
We also found that a vulnerability (CVE-2020-10189) in Zoho’s Cloud Desktop Central is being exploited by APT-41 – a Chinese APT group known for using Maze ransomware as their arsenal. Hackers have been selling access to networks that use this Remote Monitoring Management application for $100,000 in the dark web.
CVE-2020-0688 – a Microsoft Exchange Server vulnerability is being used by two ransomwares (Egregor, and Thanos). *Discovered in February 2020, an exploit became available for this vulnerability in March and within the same month it started trending.
Note: *Based on the trending charts from our RBVM platform (RiskSense) that draws data from hacker forums and advanced vulnerability analytics.
This vulnerability was used by APT Group Dark Halo to bypass multi-factor authentication defenses against unauthorized email access making it easy for them to login to SolarWinds trojanized update. Dark Halo is suspected to have attacked SolarWinds three times between late 2019 and July 2020.
Common Weaknesses that caused these vulnerabilities
The products that are weakened by these vulnerabilities are Microsoft Exchange Server, Windows (10, 8, 7) & Windows server (2019, 2016, 2008, 2012), Oracle’s Fusion Middleware, Weblogic Server, Zoho’s Manage Engine Desktop Central, Apache’s Tomcat and CISCO’s Ios xr.
When we analyzed the CWE (common weakness enumeration) we found the following – CWE-835 (Infinite Loop), CWE-269 (Improper Privilege Management), CWE-20 (Improper Input Validation), CWE-134 (Use of Externally-Controlled Format String), and CWE-502 (Deserialization of Untrusted Data). Out of three vulnerabilities categorized under CWE-502 two are being used by APT groups and ransomware.
This calls to question the secure coding practices that developers need to adopt. They should avoid these weaknesses even while they write the code to avoid shipping products that are vulnerable to serious cyber attacks.
Analysis of Top 3 Vulnerability Scanners
The good news is that popular scanners such as Tenable, Nexpose, and Qualys can detect these vulnerabilities. However, Nexpose doesn’t detect these two vulnerabilities – CVE-2020-2555 and CVE-2020-3118.
Google’s 2020 Top 10 Vulnerabilities
The way forward
The pace at which threat actors seem to weaponize and exploit newly minted vulnerabilities is downright alarming. With seven out of ten vulnerabilities having RCE/PE capability prioritizing these weaknesses for patching becomes a priority.
These trends are a strong indication for organizations to start looking at their attack surface and find ways to defend them from threat actors.
Year after year, we are looking at products with more vulnerabilities that threat actors are more than happy to use. One of the many solutions that could help organizations is accurate dynamic data that provides information about vulnerabilities and their threat context. We need trend watchers based on machine learning that can compute this dynamic data and provide organizations with predictive trends about vulnerabilities that could be exploited — even before it manifests. Working in tandem with this, a Shift Left solution that would help developers test and correct the weaknesses in their products before it goes to market.









