Cyber threat actors have been working hard during these pandemic times. The lockdown that came at the wake of this virus attack was sudden and unplanned. Systems, infrastructure, and sensitive information that was hitherto viewed within the secure walls of one’s office is now being accessed through insecure connections and unsafe laptops from one’s home.
The year 2020 will probably go down in history as the worst year for database breaches and we are only halfway through it.
We recently released a report series called ‘Cyber Risk in Working Remotely’ where we examined popular database solutions for vulnerabilities.
Key Findings
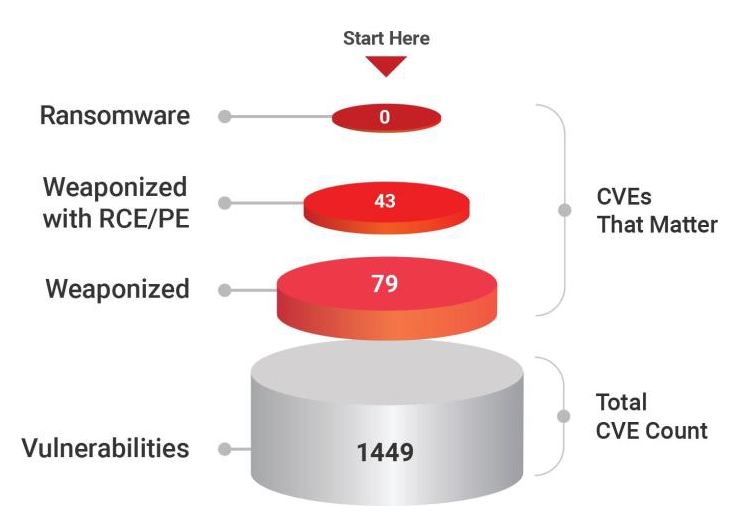
- 79 CVEs are weaponized
- 43 CVEs have RCE and Privilege Execution
- Scanners such as Nessus, Nexpose, Qualys have missed 5, 9, and 5 vulnerabilities, respectively.
Weaponization and Critical vulnerabilities
- We investigated a total of 1449 vulnerabilities in database technologies. Out of these, 79 are weaponized and 43 have RCE & PE capabilities.
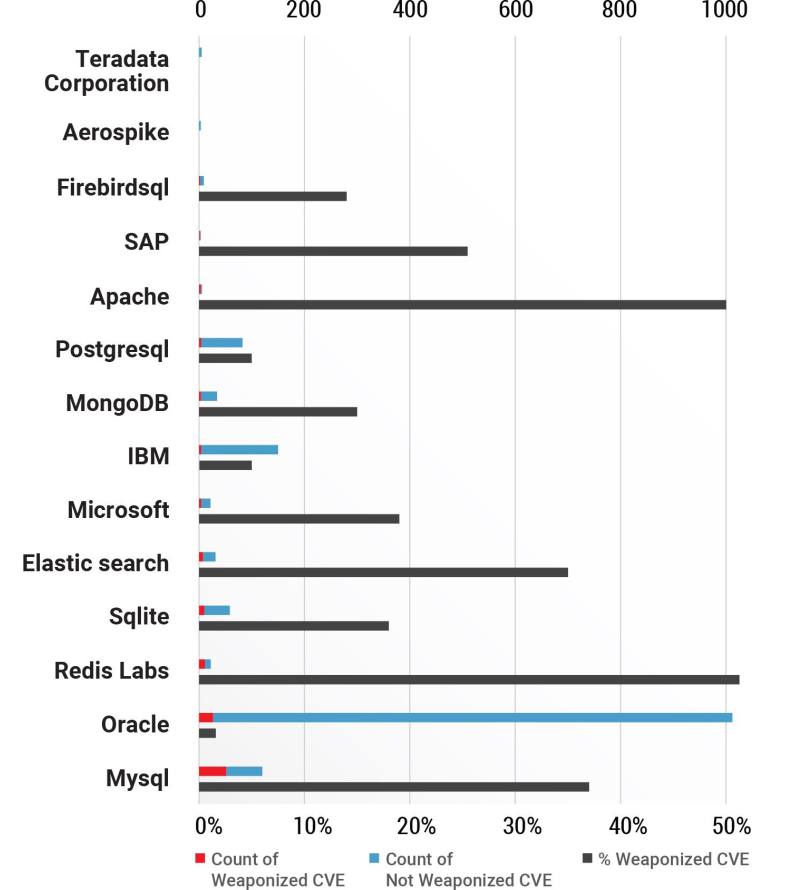
- Oracle has the maximum number vulnerabilities (1286) that are yet to weaponized. It also ranks first among the applications with highest number of weaponized vulnerabilities (78) and 29 CVEs can be executed remotely (RCE) while 27 CVEs have privilege execution.
- Mysql stands second with 40 weaponized vulnerabilities 76 CVEs that are yet to weaponized.
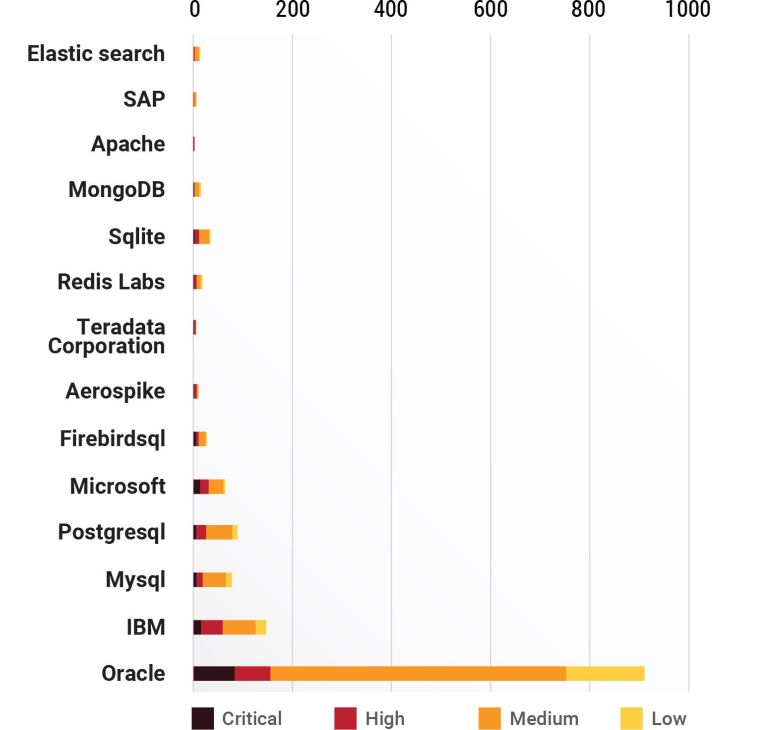
- Where criticality of vulnerabilities are concerned, Oracle unsurprisingly leads the charge with 123 critical and 109 high priority vulnerabilities. They are followed by IBM with 21 critical and 65 high priority vulnerabilities.
Critical vulnerability that allowed the ransomware attack on MongoDB still exists today. This vulnerability was well exploited by Harak1r1 group in 2017 and data was auctioned for millions of dollars.
- CVE-2019-9193 in Postgresql allows arbitrary code in the context of the database’s operating system user and it can be used to run system commands on Windows, Linux and macOS.
- CVE-2014-1466 is a SQL injection vulnerability in CSP MySQL User Manager 2.3 that allows remote attackers to execute arbitrary SQL commands through the login field.
Alarmingly, none of these critical vulnerabilities are showing up in popular scan systems that we use to alert us of these threats.
Count of vulnerabilities missed by popular scanners
| Nessus | Nexpose | Qualys | |
| IBM | 0 | 1 | 0 |
| Mysql | 4 | 4 | 4 |
| Postgresql | 1 | 1 | 1 |
| Microsoft | 0 | 1 | 0 |
| Elastic search | 0 | 1 | 0 |
| Apache | 0 | 1 | 0 |
| Total | 5 | 9 | 5 |
There is a huge number of vulnerabilities that are yet to weaponized and unless they are fixed immediately database breaches, leaking of private information, auctioning financial data by threat actors will become a daily occurrence.
Download the whitepaper Cyber Risk in Database










