The usage of online conferencing applications increased exponentially early this year. Over 100 million new participants started using Zoom (despite its flaws) in March 2020.
Google Meet which was a paid application for G-suite users was made free to cater to the increasing online conferencing needs. LogMeIn Inc. declared ten times increase in their usage since March, this year.
With the recent breaches in Zoom application and increasing instances of ‘zoombombing’ and data theft, a definitive study of popular online video conferencing tools was needed. In our recent white paper series, we examined popular online conferencing applications (Zoom, Logmein, Cisco, Teamviewer, Adobe, Microsoft, Polycom, Lifesize, Pexip) and has thrown the spotlight on the vulnerabilities that exist in it.
Key Findings
The report provides an in-depth study of popular online conference applications and their inherent vulnerabilities.
- A total of 877 vulnerabilities
- 38 CVEs are weaponized
- 10 CVEs are associated with RCE
- 7 CVEs have Privilege Execution
Vulnerabilities in Online Conferencing Applications
The research team of Securin examined over 877 vulnerabilities that have been identified in the past decade (2010 – 2020) out of which 38 vulnerabilities have been weaponized and can be executed remotely. Out of the weaponized vulnerabilities, over 10 are associated with RCE (Remote Code Execution) and 7 with PE (Privilege Execution).
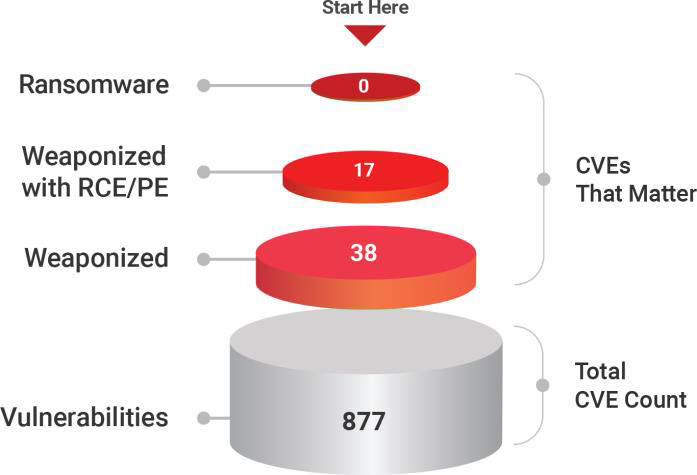
Out of the total vulnerabilities that exist in these applications, 220 are critical, while 55 are high and 521 in the medium level of priority, respectively.
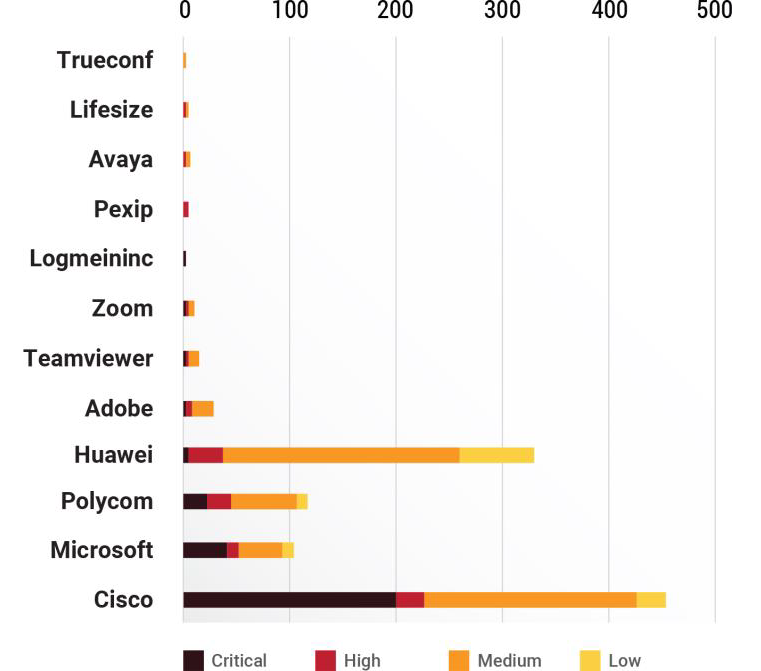
Vendor Vulnerability Count
Among the vendor who came under the lens, we find that Cisco has over 189 critical vulnerabilities.
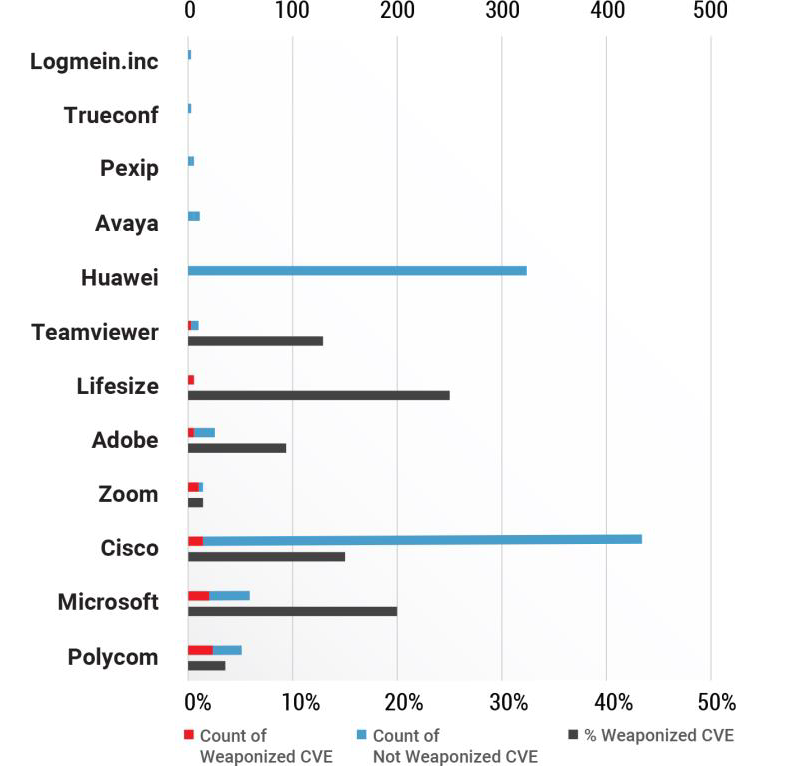
Cisco leads the way with 418 vulnerabilities in total followed by Huawei with 325 vulnerabilities. Among the count of weaponized vulnerabilities, Polycom is high with over 13 vulnerabilities followed by Microsoft with 9 vulnerabilities. Worryingly, 7 vulnerabilities in Polycom are associated with RCE.
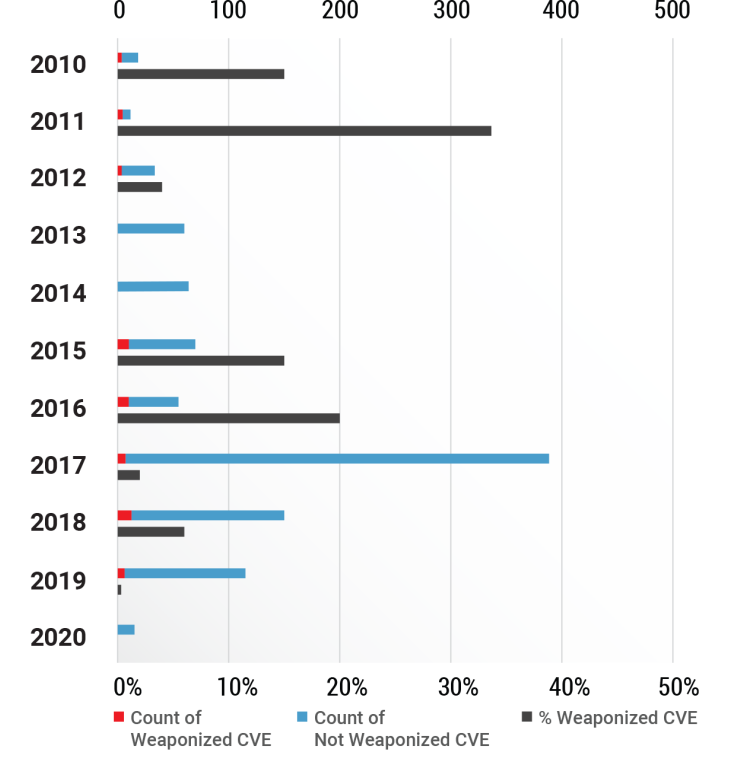
In terms of weaponization trend, over 391 vulnerabilities were discovered in 2017. In general, the rate of weaponization of vulnerabilities has been high since 2015 and peaked during 2016.
The most alarming statistics of this report was that critical vulnerabilities in online conference tools are not being detected by popular scanners.
Count of vulnerabilities missed by Scanners
Nessus |
Nexpose |
Qualys |
|
|---|---|---|---|
Cisco |
2 |
3 |
0 |
Lifesize |
1 |
1 |
1 |
Microsoft |
2 |
6 |
1 |
TeamViewer |
0 |
1 |
1 |
Polycom |
4 |
4 |
4 |
Zoom |
1 |
1 |
1 |
Total |
10 |
16 |
8 |
CVE-2015-4683 in Polycom allows attackers to gain sensitive information and gain privileges over HTTP requests.
Zoom’s CVE-2017-15049 and Lifesize’s CVE-2011-2763 allows remote attackers to execute arbitrary code.
Microsoft’s CVE-2010-3136 allows local users and remote attackers to execute arbitrary code and to mount DLL hijacking attacks via a Trojan horse.
Polycom’s CVE-2015-8300 allows local users to gain privilege, CVE-2012-6611 allows users to gain access without an administrative password while CVE-2015-4681 has a webapp exploit associated with it.
Online conference tools for all its faults is essential to conduct business and to have a semblance of normal life today. Schools, colleges, offices, industries are all dependent on these tools for the foreseeable future. Though the number of weaponized vulnerabilities is less, they have nonetheless helped many threat actors to penetrate and listen to meetings where sensitive information is being discussed or to disrupt conferences with malicious intent.
Until these vulnerabilities are proactively fixed, you will need to exercise the utmost caution while discussing sensitive information in online meetings.
Download the whitepaper Cyber Risk in Online Conference.










