A data breach resulting in the loss of their jobs is one of the worst nightmares for a CISO. Research says that companies that have experienced a breach underperform the market by more than 15% three years later. That brings you to the question – “Is your data safe?”
Securin analyzed more than 290 database products and identified 4352 vulnerabilities, of which 24% have high predictive risk ratings, and 12% are trending in the wild! What should be your course of action? Read on to know…
Data breaches exposing millions of personal data, bank information, credentials, social security numbers, and healthcare records have become commonplace in the past few years. These organizations suffer not just reputational loss but significant financial reparations that need to be made to their clients and customers.
Many organizations have gone bankrupt following cyber attacks that exposed their customer data. In fact, 60 percent of small companies go out of business within six months of falling victim to a data breach or cyber attack. One of the major contributors to these are the vulnerabilities in database products.
Our research dives deep into database vendors and products to help you understand which are vulnerable to attackers and what you can do to safeguard them. We identified weakness enumerations, vulnerabilities, weaponization statistics, exploit types, ransomware associations, and ties with APT groups that plague these database offerings.
In 2020, we identified 1449 vulnerabilities across 18 vendors. Our latest 2022 research has grown to include 128 unique vendors and 291 products and identified 4352 vulnerabilities overall. This analysis includes a broad umbrella of database products with data capabilities including storage, management, analytics, and visualization
Our analysis is two-fold: Definitive Analysis, which deals with known vulnerabilities and associated threats, and Predictive Analysis which leverages Securin’s proven AI/ML capabilities that provides a risk rating of a vulnerability being exploited in the wild.
Definitive Analysis
In this section, we deal with definitive intelligence, like the vulnerabilities in databases, their exploitation by threat actors, and publicly available exploits linked to these vulnerabilities.
Vulnerability Prioritization
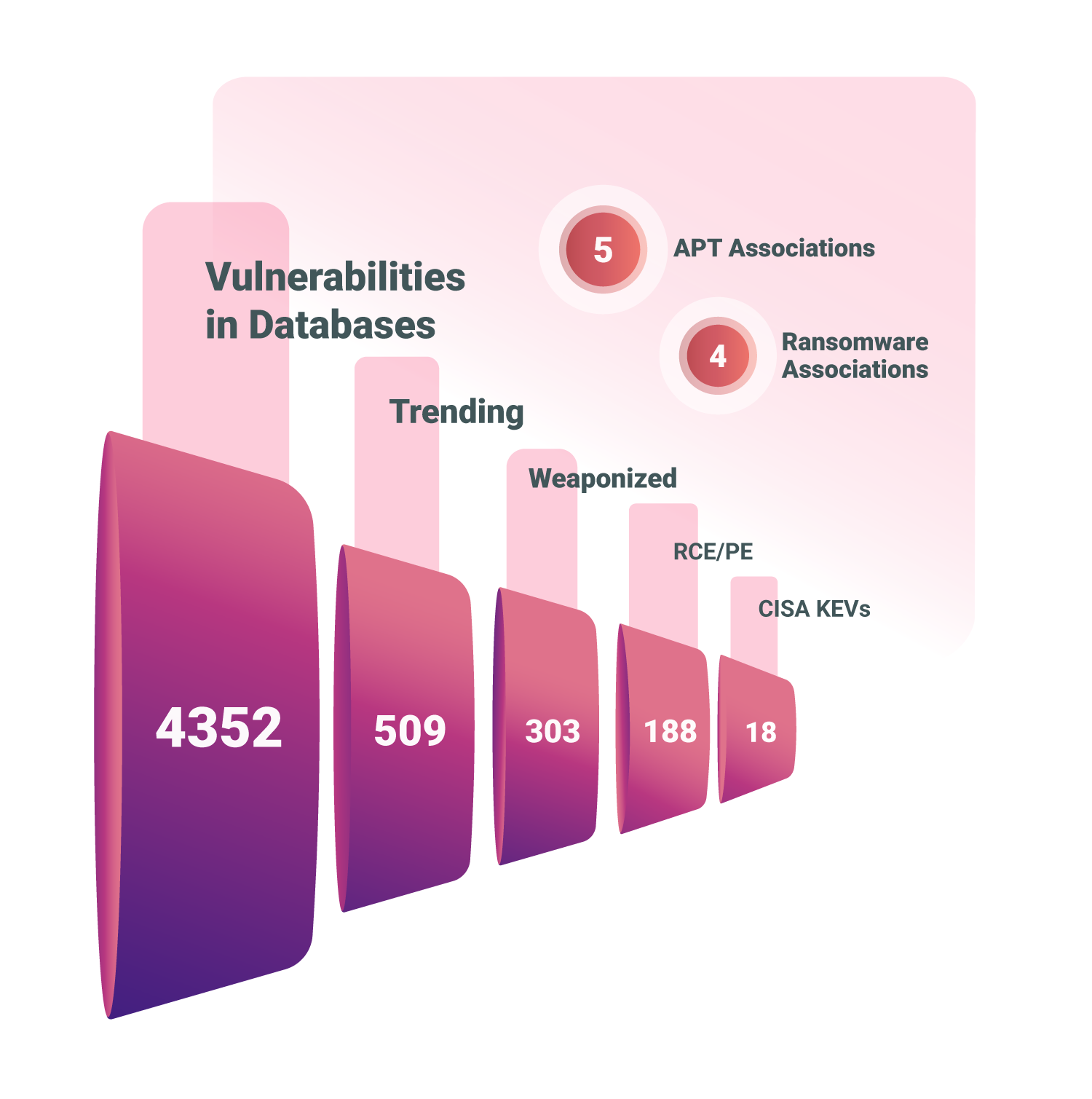
Our research into database products identified 4352 vulnerabilities that expose them to attackers. Of these, 509 CVEs (12%) are being actively searched by attackers. These vulnerabilities, if left unchecked, can serve as low-hanging fruit for attackers to feast on.
As we delve deep into this research, our experts provide the threat context of these vulnerabilities to understand which of these could pose the greatest danger to organizations. Threat actors have already weaponized 303 vulnerabilities, an indication that threat actors have ready methods to exploit these vulnerabilities and thus warrant immediate attention from organizations.
Below, we further look into some of the key vulnerability findings from our research.
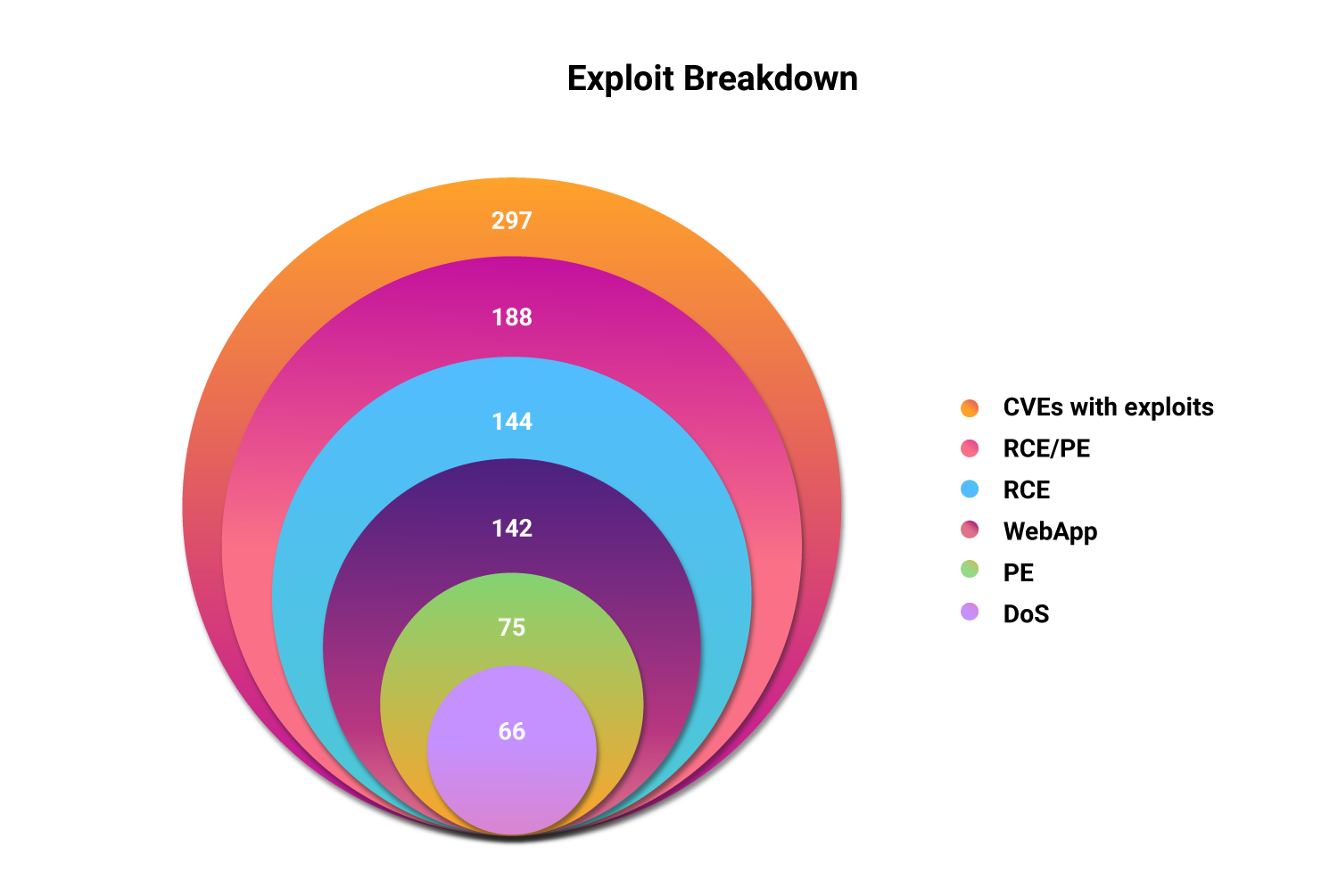
Dangerous Vulnerabilities: The most worrisome fact here is that, of the vulnerabilities with exploits available in the public domain, 63% can allow attackers to execute custom code remotely or even escalate privileges once they gain entry into vulnerable networks. This gives attackers the upper hand, allowing them to enter into networks, crawl through deeper, or even chain multiple vulnerabilities together to cause maximum disruption on affected networks.
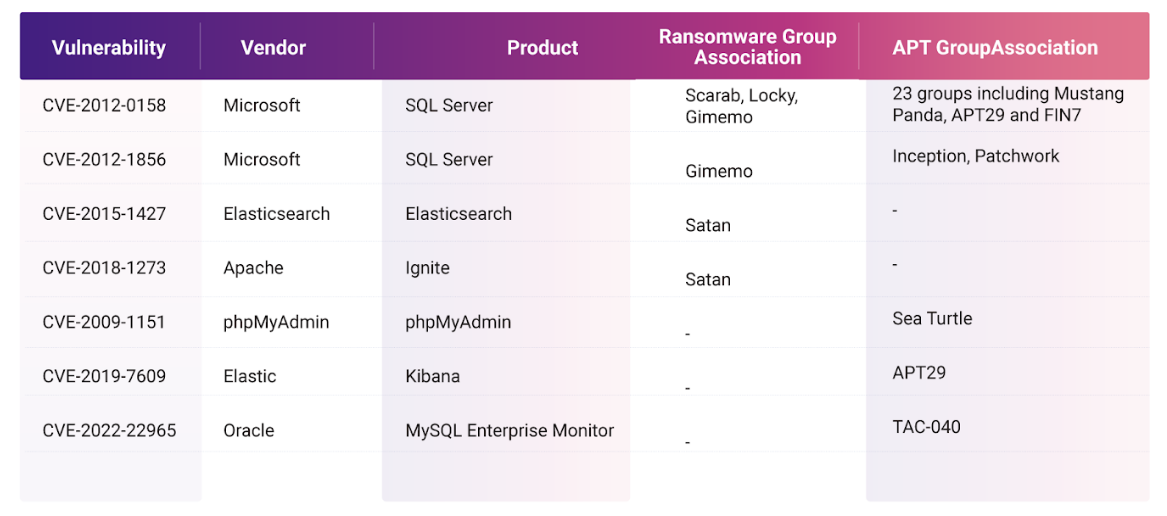
Ransomware and APT Group Associations: Vulnerabilities with known instances of exploitation by ransomware and Advanced Persistent Threat (APT) groups are of the highest order of threat to organizations as unpatched instances of these vulnerabilities offer a permanent attack window to threat actors on the lookout. Further, with instances of threat groups increasingly sharing techniques and tactics among them, the danger is all the more enhanced.
Four ransomware groups—Scarab, Locky, Satan, and Gimemo, and 24 APT groups- have previously exploited seven database vulnerabilities thus far.
Known Exploited Vulnerabilities (KEVs) catalog by Cybersecurity and Infrastructure Security Agency (CISA ): As a measure to warn organizations against threat actor-favored vulnerabilities, CISA maintains a repository of Known Exploited Vulnerabilities (KEVs) that is regularly updated. At the time of this investigation (September 2022), 18 of the vulnerabilities we identified in databases were part of the CISA KEVs.
Of the vulnerabilities in database products, 28 of them have been explicitly called out in our blogs that focus on trending threats to provide organizations with timely warnings against significant exposures.
Severity Analysis
We looked at the database vulnerabilities from a severity perspective to understand how many critical and high-severity vulnerabilities organizations might have in their networks. By NVD’s CVSS standards, 32.6% of all database vulnerabilities fall into this category.
We further scored the vulnerabilities using our proprietary Vulnerability Risk Score (VRS) that attributes severities considering additional threat context and trending factors. The result was that, by VRS standards, 6.7% of the vulnerabilities belonged to the critical-high category. This is in close agreement with the percentage of weaponized vulnerabilities overall (6.96%).
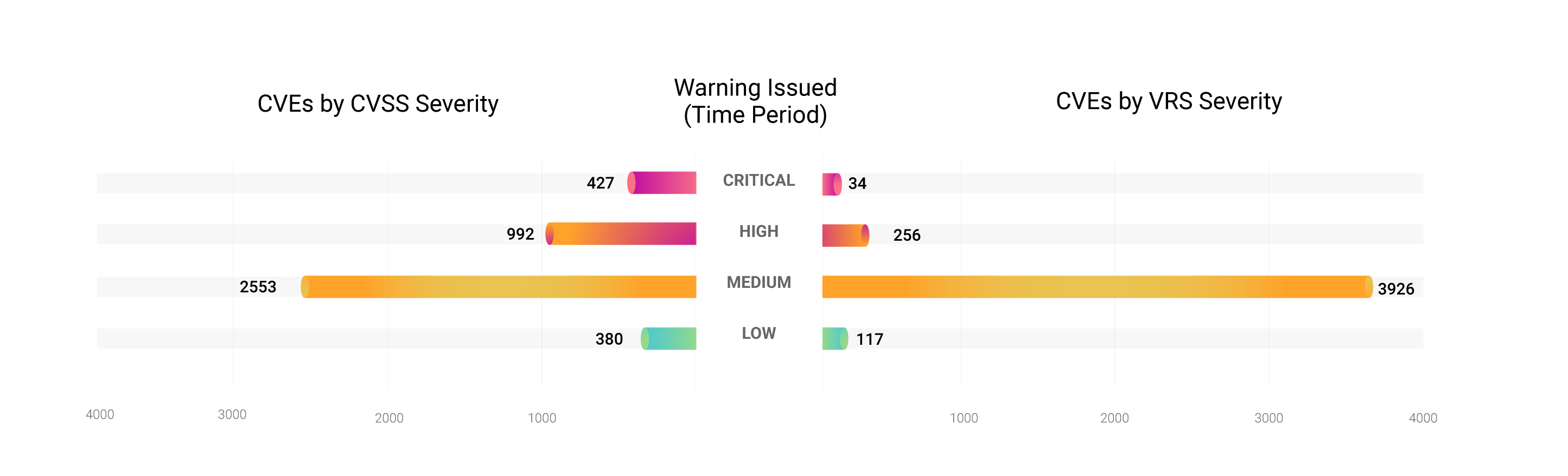
The Securin Vulnerability Intelligence (VI) platform continuously tracks and assesses a vulnerability’s real risk to an organization based on past and current events, and interest in the vulnerability from hackers. To quantify this risk, VI attributes a Vulnerability Risk Score (VRS) to every vulnerability that reflects its threat context and the likelihood of the vulnerability being exploited in the wild.
Vulnerabilities with a critical or high severity rating need to be prioritized for patching sooner rather than later. Given this, organizations need to adopt a threat-based perspective to classify the vulnerabilities to be considered and not simply depend on NVD ratings that might overwhelm security researchers with the sheer volume of vulnerabilities.
Latency Analysis
For a long time now, one of the major aspects of our research has been to focus on the latencies along a CVE’s timeline, from being published to being associated with threat actors. One constant factor that has stood out is how quickly attackers are weaponizing vulnerabilities today, within days of NVD disclosure and sometimes even before the vendor publishes a vulnerability.
In this context, we also studied the vulnerabilities in databases from a latency lens. On comparing the gaps between when the NVD disclosed a vulnerability and when public exploits for the same were released, here is what we found:
More than 51% of the vulnerabilities with known exploits were exploited before the NVD could disclose the vulnerability. An organization relying solely on the NVD to patch vulnerabilities would be caught unawares in such a scenario.
Attackers were quick to exploit 13.26% of the vulnerabilities and even released codes in the public domain on the same day as they were added to the NVD. This gives organizations very minimal response time and calls for a proactive approach to prioritizing and mitigating vulnerabilities.
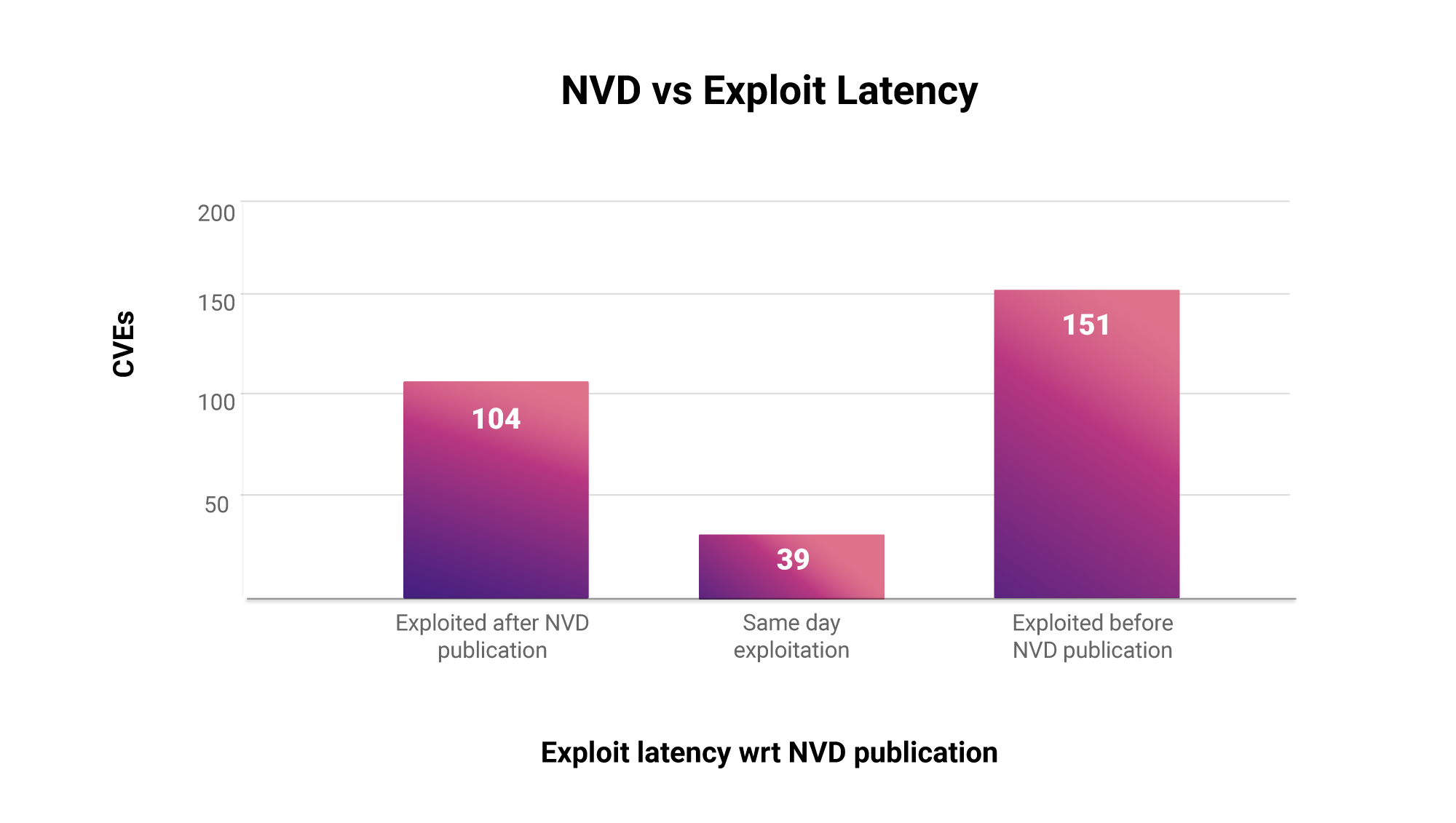
CVE-2012-1856, CVE-2019-7609, CVE-2022-22965, and CVE-2022-24706 are CISA KEVs that were exploited before NVD Publication.
| Predictive VRS Score trends from the Securin VI platform |
|---|
|
CVE-2012-1856 (Microsoft SQL Server) |
|
CVE-2019-7609 (Elastic Kibana) |
|
CVE-2022-22965 (Oracle MySQL Enterprise Monitor) |
|
CVE-2022-24706 (Apache CouchDB) |
From the above, it is clear that all these vulnerabilities have the maximum threat rating in our platform and are vulnerabilities highly sought out by threat actors, corroborating their place on the CISA KEV catalog.
Top Vendors and Products
We analyzed the vendor products that give rise to these exposures. Going by the count of vulnerabilities affecting their database offerings, here is a look into the top 5 vendors and products affected.
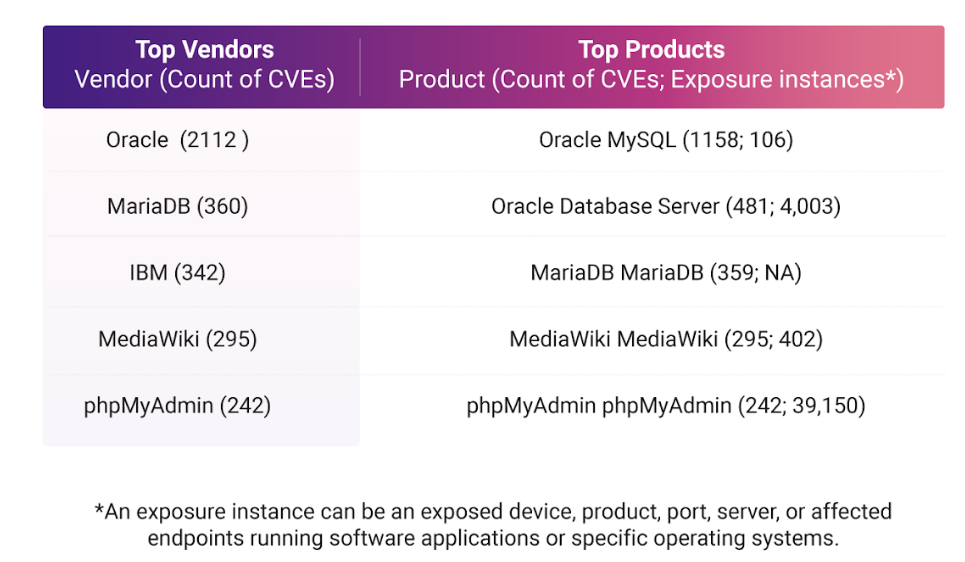
Oracle database offerings stand out from the rest owing to the huge chunk of vulnerabilities in its products. In all, there are 50 affected database products from Oracle, of which five have more than 50 vulnerabilities in them.
We also identified the database products with high-impact vulnerabilities owing to their threat associations.
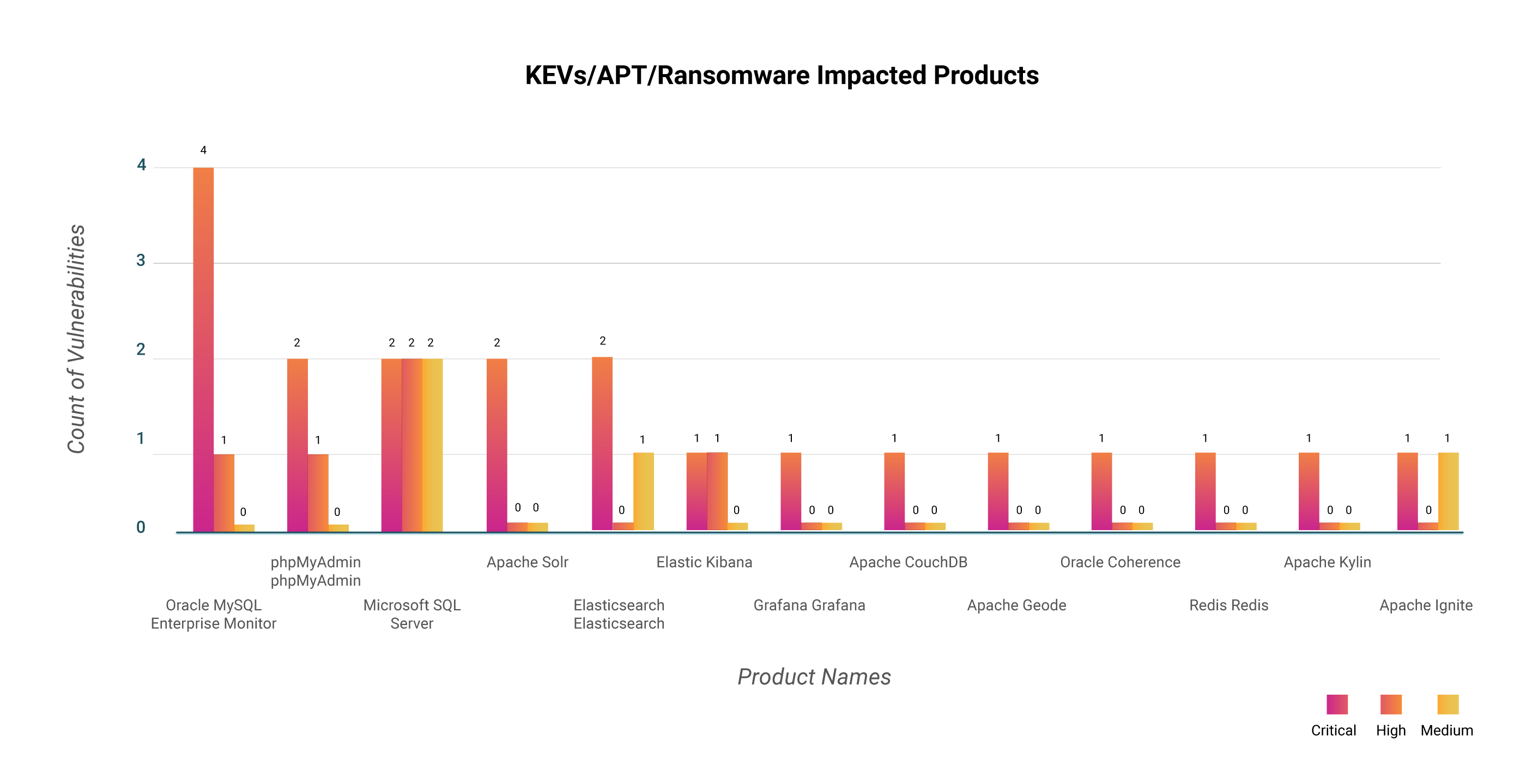
Users of database products are recommended to stay updated on database versions released by their vendors and upgrade without delay.
What are the weaknesses causing vulnerabilities in databases?
Vulnerabilities are manifestations of weaknesses in code that attackers can exploit. We traced back the weaknesses powering the 4352 vulnerabilities in database products and identified 197 weaknesses overall.
We extended MITRE’s weakness scoring methodology to database vulnerabilities and scored each of the weaknesses based on the CVSS v3 scores of the vulnerabilities falling in each CWE bracket. From this analysis, here is a look into the top weaknesses in databases.
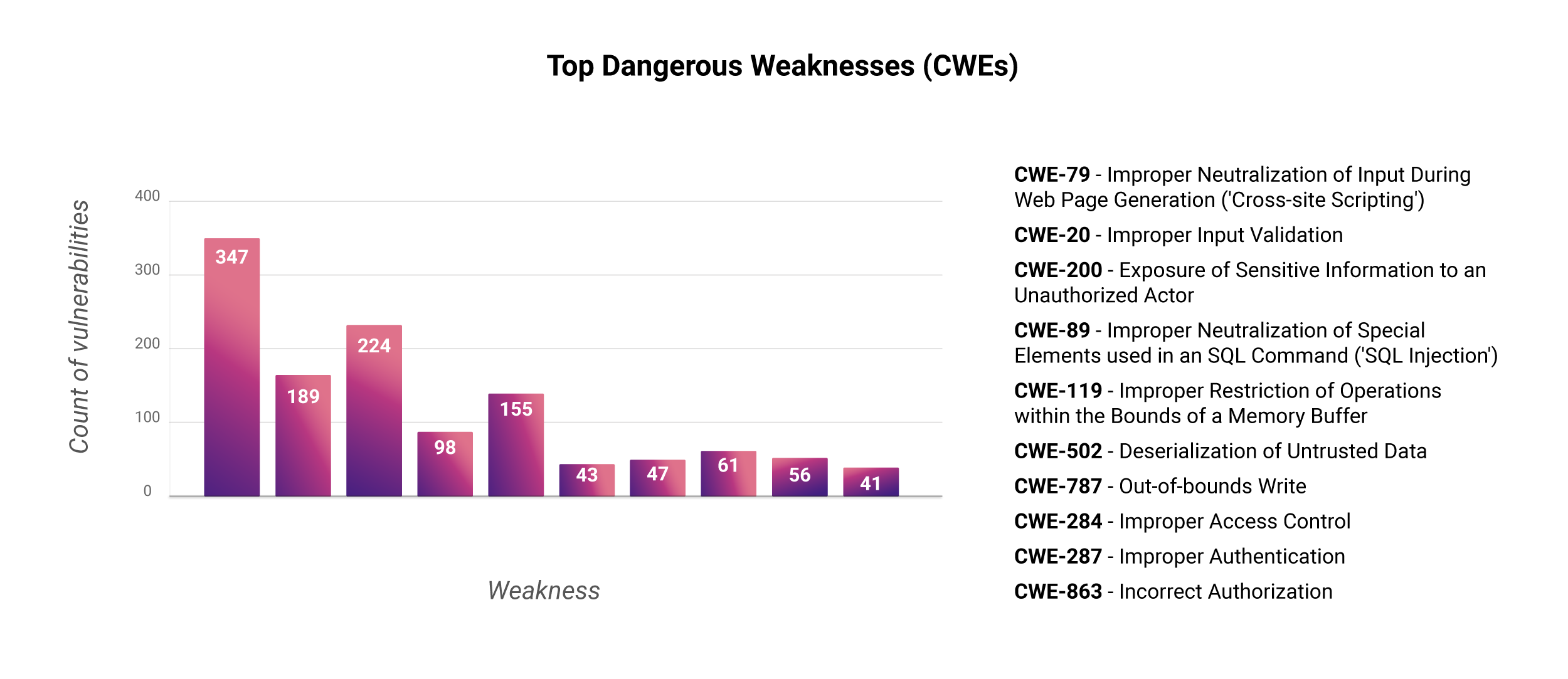
Our analysis of these weaknesses also brought up some interesting findings.
The weakness with maximum database vulnerabilities is the second most dangerous software weakness, according to MITRE’s top CWE ranking.
CWE-787, which ranks 1st on MITRE’s list, drops down to rank 7 for database weaknesses. This goes to show that the true impact of a weakness needs to be considered in accordance with the application category and not just the insufficiency alone.
CWE-284, the 8th most impactful database weakness, is obsolete. There are also 10 other obsolete weaknesses that database vulnerabilities are mapped to. This leads to inadequacy in understanding the real risk of these vulnerabilities; the solution is to map these vulnerabilities to more appropriate weaknesses that bring out their true impact.
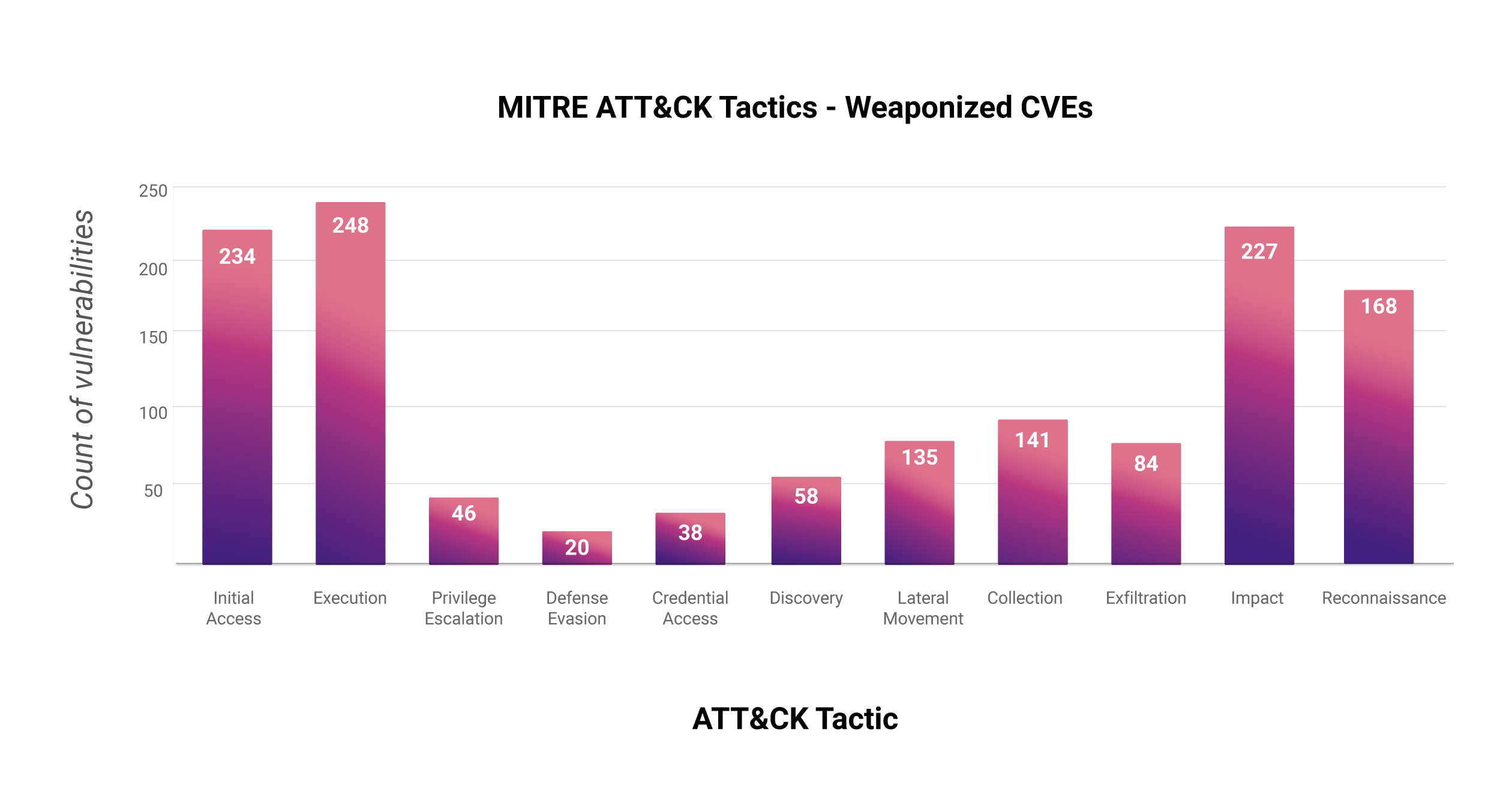
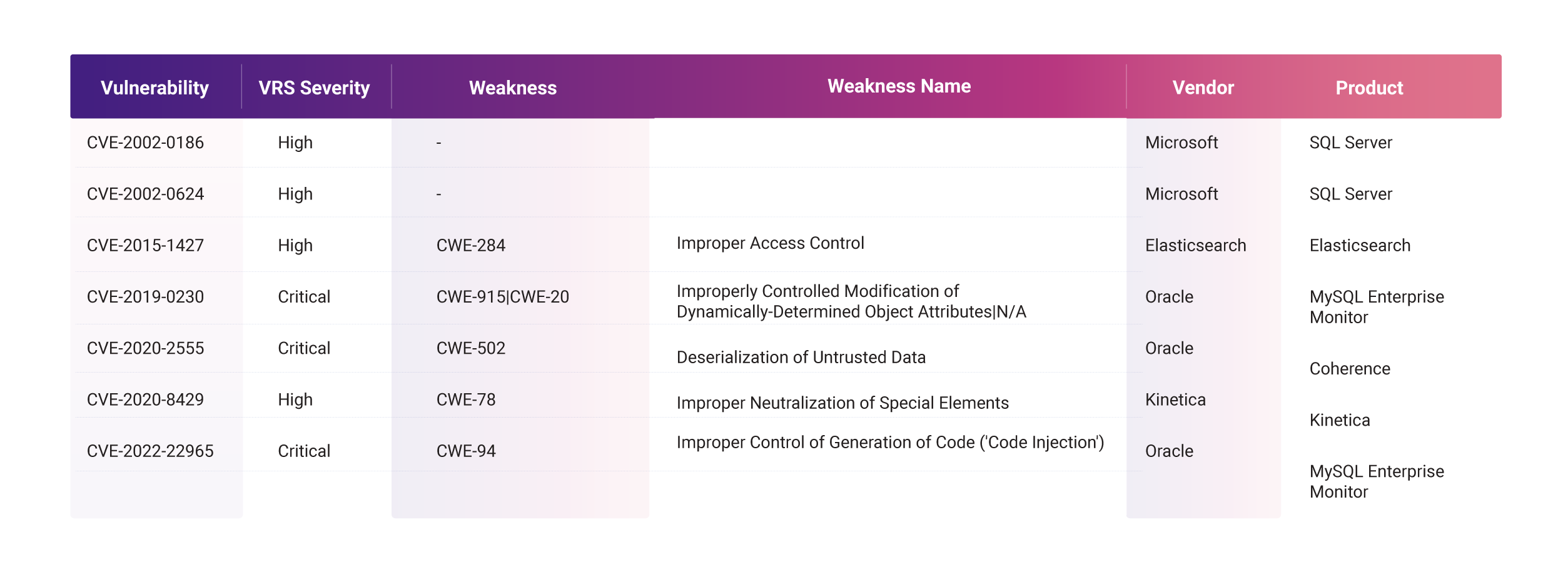
We also mapped the database vulnerabilities to the MITRE ATT&CK kill chain to understand how these vulnerabilities can be used in a real-world attack.
The vulnerabilities in databases cumulatively allow an attacker to go from launching an attack all the way to reconnaissance, allowing for completely compromising the victim’s network.
Of note, 227 vulnerabilities translate to ‘Impact,’ meaning attackers can use them to manipulate the data in the affected database. Further, 84 vulnerabilities allow for data exfiltration providing attackers a means to extract sensitive data from vulnerable databases.
There are seven weaponized vulnerabilities in databases that can individually be mapped to all stages of the MITRE ATT&CK kill chain. If compromised, each of these seven vulnerabilities can allow attackers to easily go from penetrating vulnerable networks to reconnaissance without additional effort.
Are scanners finding it all?
Organizations fall back on scanners to identify exposures in their network. However, many of the vulnerabilities in databases are not identified by scanners. Popular scanners like Nessus, Nexpose, and Qualys fail to detect 743 vulnerabilities in databases, which amounts to almost 17% of the vulnerabilities overall. 62 of these vulnerabilities are weaponized, indicating that attackers have readily available methods to exploit the instances left unpatched.
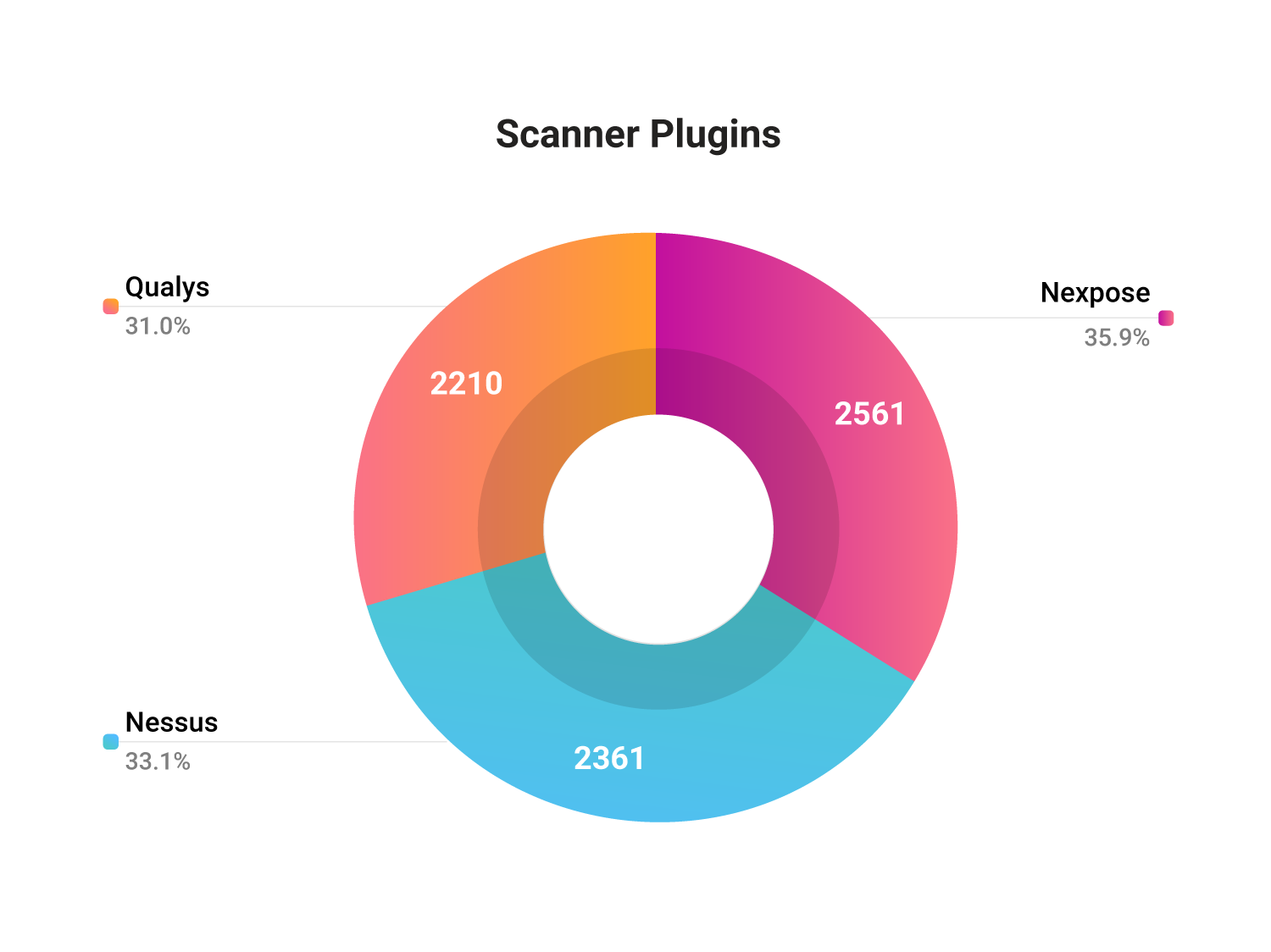
The fact that there could be exposures in your network that might not show up on scanners is not to be taken lightly. Organizations must opt for a holistic attack surface management solution that can discover all exposures in their network that could endanger them.
Predictive Analysis
In this section, we look into predictive insights from our threat intelligence platform that tracks the surface web, deep web, and dark web trends, hacker chatter, vulnerability exploitation, and in general, captures the interest of attackers.
Vulnerabilities on Attackers' Radar
Our threat intelligence platform constantly monitors vulnerabilities, tracking their dynamic attack trends and related hacker chatter. Combined with instances of exploitation and the additional definitive intelligence from the platform, our analysts predict evolving vulnerabilities that are most likely to be exploited in the immediate future.
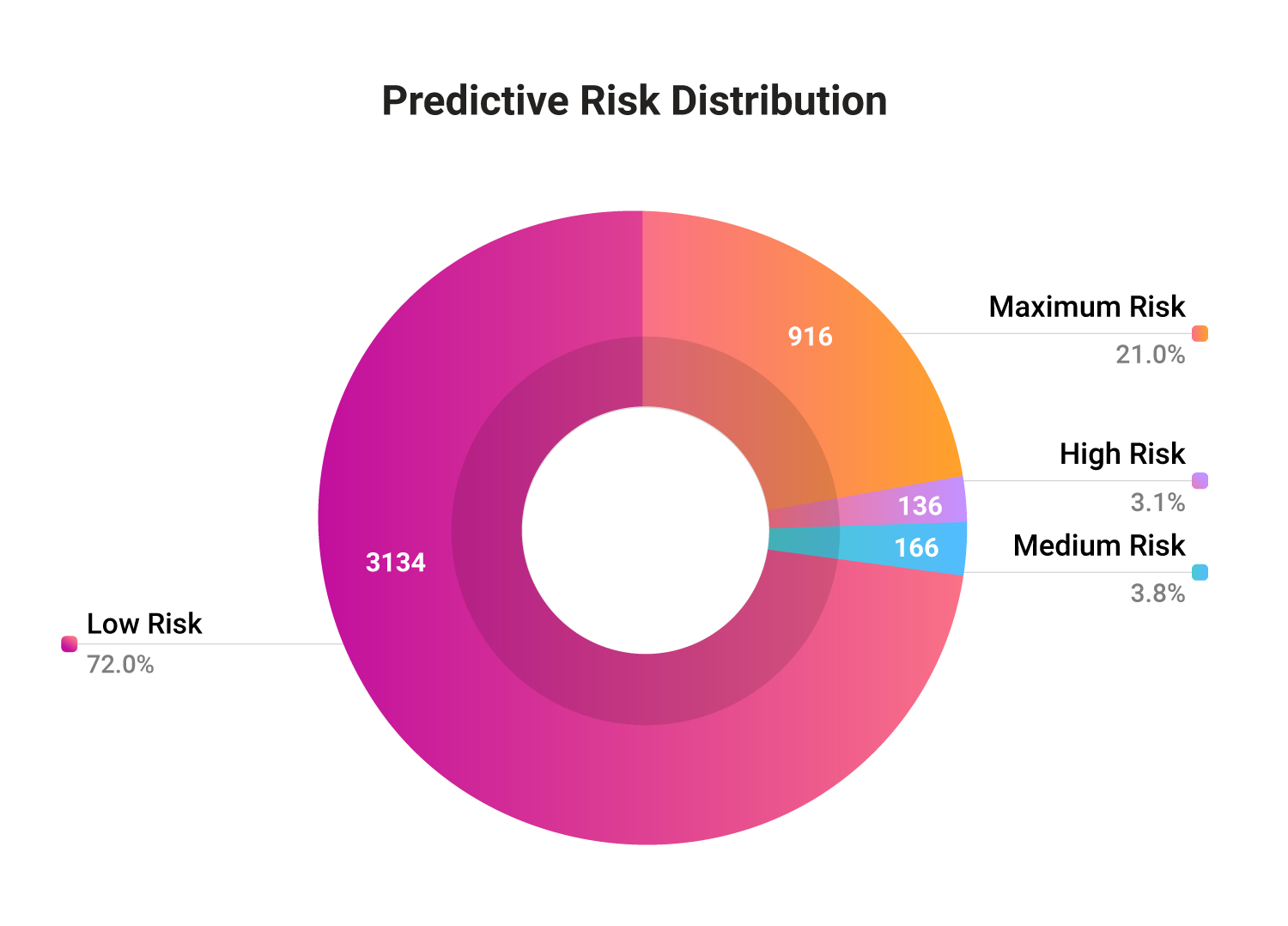
Of the 4352 database vulnerabilities, our platform predicts a high/maximum likelihood of exploitation for 24% of them. Interestingly, only 194 of these are weaponized, with only 18 of them being part of CISA’s KEVs.
We highlight the top five vulnerabilities with maximum threat rating. These vulnerabilities have been trending in hacker channels and can be impactful on exploitation as they could lead to remote code execution. Further, they impact widely used products.
| Screens from the Securin VI platform |
|---|
|
Legend: D – Hacker Discussion;
|
|
Oracle MySQL Enterprise Monitor |
|
Oracle MySQL Enterprise Monitor |
|
Apache CouchDB |
|
Redis Redis |
|
Apache Geode & Oracle MySQL Enterprise Monitor |
Interestingly, all the above vulnerabilities are CISA KEVs. Given this fact, it is highly imperative that organizations pay attention to these vulnerabilities.
We also call out vulnerabilities that do not yet qualify to be added to the CISA KEVs, due to the absence of exploitation evidence. However, our threat intelligence platform detects significant hacker interest. The vulnerabilities also have publicly available exploit codes and impact widely used products.
This is a clear indication that we need a vulnerability prioritization approach that considers both the definitive and the predictive nature of vulnerabilities. A vulnerability must be studied in its entirety, complete with threat context, predictive insights, and business importance, in order to prioritize the ones that could affect your organization the most.
Five things organizations can do to safeguard their network
Databases are intended to be a centralized repository of information for all sales transactions, product inventory, customer profiles, and marketing activities. Most organizations cannot afford a breach of their database. As can be seen from our continuous research, threat actors are constantly expanding their attack vectors, looking beyond common critical vulnerabilities, and including weaknesses and easily overlooked vulnerabilities in their arsenal.
Here are 5 steps organizations can adopt to protect their databases from threats.
Create and maintain a detailed asset inventory to help you track updates better.
Regularly follow vendor advisories of the products you use and ensure suggested mitigations are incorporated.
Do not miss out on monitoring third-party products/connections that could indirectly provide access to your personal information.
Prioritize vulnerabilities for patching, considering their threat context, the likelihood of exploitation, and business impact, if exploited.
Regularly back up your data in reliable locations to use in case of emergencies.
How We Can Help
Securin can help organizations scan their assets and identify weak points in their databases. Learn more about our Attack Surface Management platform or how to access our Vulnerability Intelligence data!