Popular scanners such as Tenable, Qualys and Nexpose are missing 48 vulnerabilities out of 102 SolarWinds vulnerabilities. To help 18000 customers who have been affected, CSW team has come up with a script that would help detect SolarWinds Orion Product running on your network.
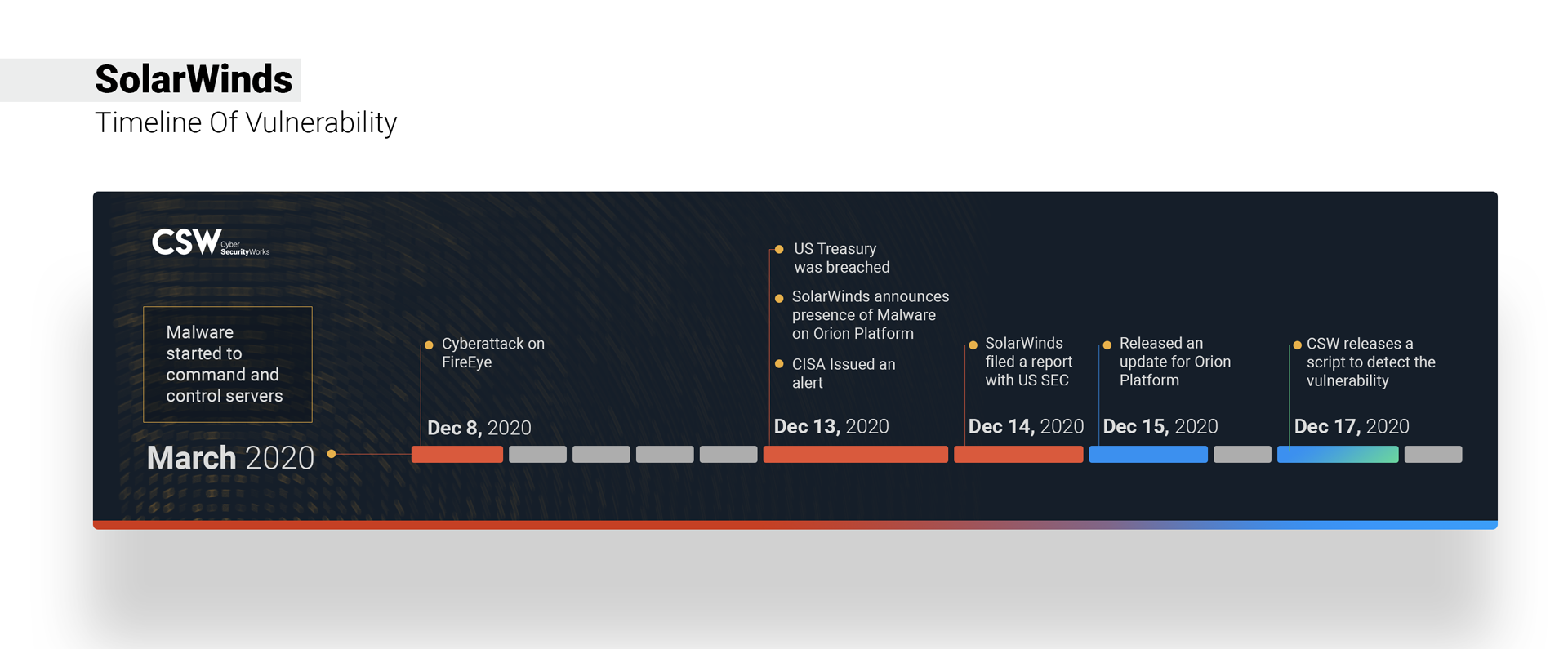
On Dec 13, 2020, it was announced that the SolarWinds Orion Platform got corrupted by the distribution of backdoor SUNBURST – a malware disguised as an update that compromised multiple critical government agencies and more than 18000 customers world-wide.
The attack was perpetrated by an APT group that had patiently mounted this attack since spring 2020. As we write this, the name of the APT group nor its origin country has been confirmed but organizations that have been compromised need to start their incident response process and start remediation plans immediately.
Based on our analysis, we observed 15 CVEs associated with Orion Products and 7 CVE’s are weaponized and 3 CVEs are capable of Remote Code Execution and Privilege Escalation. Click here for more information
We also analyzed the vulnerabilities that exist in numerous SolarWinds products and interestingly 49 vulnerabilities are not detected by all these top 3 vulnerabilities scanner. Click here for more information
With the scanners not detecting 50% of the vulnerabilities, we decided to help SolarWinds customers and have written a script (GitHub) to detect the SolarWinds Orion product running on your network.
Note: The script takes input as a single IP, CIDR or through text file. By default, four ports are added but it can be customized during the run.
The following script can be used to detect the vulnerability.
Script
python3 orionScanner.py –help
usage: orionScanner.py [-h] [-t TARGET] [-T TARGETS] [-c CIDR] [-a ADD]
optional arguments:
-h, –help show this help message and exit
-t TARGET, –target TARGET
Single IP
-T TARGETS, –targets TARGETS
List of IP in text file
-c CIDR, –cidr CIDR CIDR range
-a ADD, –add ADD Addition ports to check for. example: -a 8889,9991
Note: Default web ports are 80, 8080, 443, 8443
- Run the script for single IP to detect SolarWinds Orion Products
python3 orionScanner.py -t 192.168.0.1
- Run the script for Multiple ips by providing a text file with ips to detect SolarWinds Orion Products.
python3 orionScanner.py -T ips.txt
- Run the script for CIDR to detect SolarWinds Orion Products.
python3 orionScanner.py -c 192.168.0.1/24
- Run the script for single ip and additional ports to detect SolarWinds Orion Products.
python3 orionScanner.py -t 192.168.0.1 -a 8889
Reference
As part of the global detection rules that only triggered alerts, we developed automated scripts to detect the vulnerabilities.
There is no doubt that this is one of the biggest cyber attacks mounted in the recent years. 18,000 customers world-wide lie exposed due to the SolarWinds breach and the ripple effect of this incident has caused the company’s stocks to plummet down. And that’s not all.
Moody’s Investors Service said that they would be downgrading the company’s rating citing the “potential for reputational damage, material loss of customers, a slowdown in business performance and high remediation and legal costs”.
Truly it does take one cyber incident to lose years of reputation. Incidents such as these reinforce several lessons to learn. Threat actors need only one gap to breach into your system and once there, they may stay on for many months biding their time to mount their attack or to spy on confidential data. Lastly Supply chain attacks are on the rise and the only viable way to safeguard is to invest more on cybersecurity and adopt a continuous vulnerability management process.
Related Blogs
SolarWinds Vulnerability Analysis
SolarWinds: Top Scanners miss vulnerabilities
FireEye’s Stolen Pentesting Tools