Investigations on the Sri Lankan Domain attack reveal that threat actors could have used exposed credentials and vulnerabilities to breach and redirect the websites. These credentials have been exposed on the dark web for the past eight years!
On Feb 6, 2021 Sri Lanka, several .lk domains (under LK Domains) crashed and were redirected to web pages that highlighted social issues that impact the people of the island. While many local business websites were impacted by this attack, two high profile domains Google.lk and Oracle.lk were affected and their visitors redirected to other pages. Incidentally, on Feb 4, 2021, Sri Lanka celebrated its official National Independence day. The fact that this attack happened two days after this landmark celebration is very telling.
CSW’s R & D team investigated this attack and found many interesting and surprising findings –
NIC.LK Domain credentials Exposed
NIC.LK domain user names and their passwords have been exposed in the dark web. These username and password combinations have been used in multiple sites (www.gonitro.com, www.netlog.com, www.sharethis.com, www.exactis.com, www.linkedin.com, www.apollo.io, www.000webhost.com) since 2012. The password for all credentials seems to have remained the same for almost eight years and has been used in all these domains over the years!
Redirected URL Investigation
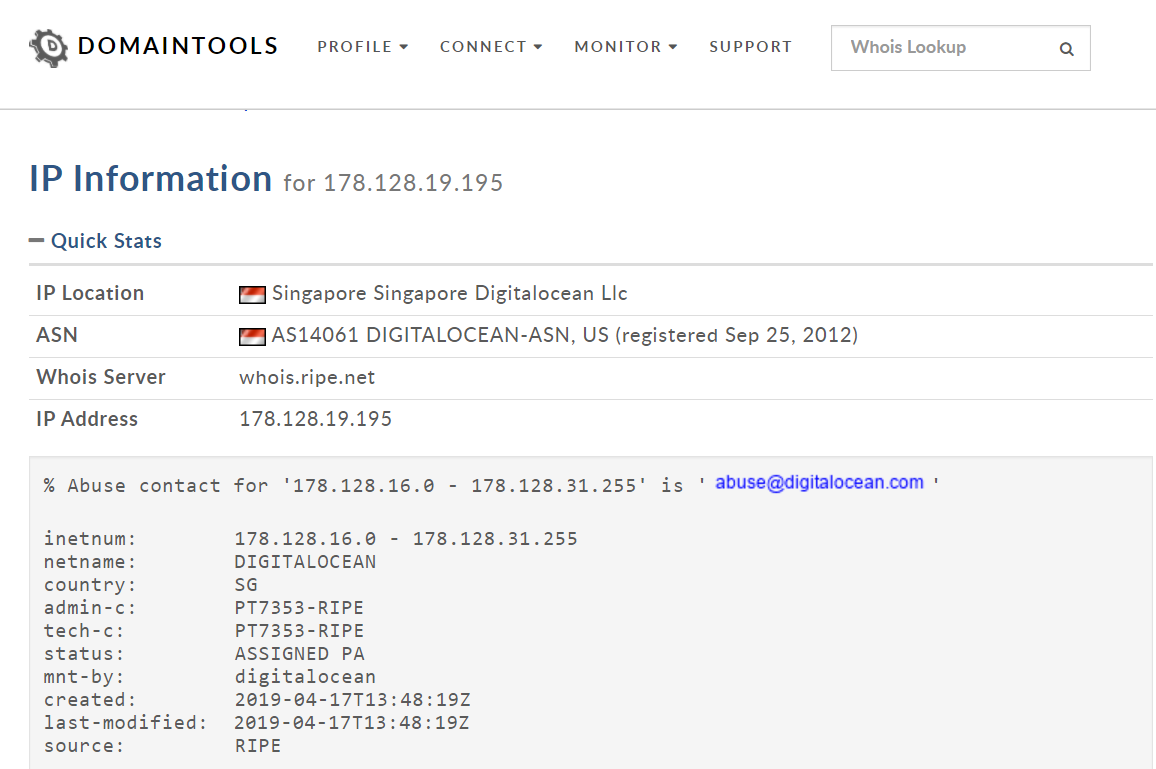
We investigated one of the URLs where the domain was redirected and found that it belonged to DigitalOcean, a cloud provider in Singapore.
Internet facing assets
We found over 90 internet facing assets identified in one network range which also had 39 vulnerabilities. We researched these weaknesses and following are our findings –
- 10 out of 39 vulnerabilities are RCE exploit type – which is most dangerous.
- All ten vulnerabilities have public exploits available which means these vulnerabilities should be prioritized for patches. Notably, four of these vulnerabilities exist in PHP (PHP < 5.6.6,5.4/5.5/5.6).
- CVE-2019-6110, CVE-2019-6111, CVE-2018-20685 and CVE-2019-6109 are vulnerabilities available in OpenSSH and they are being targeted by Ryuk to mount ransomware attacks. Our investigations reveal that APT groups such as Wizard Spider and FIN6 use these CVEs to launch deadly attacks.
- These four CVEs have been categorized under Common Weakness Enumeration (CWE) such as CWE-20, CWE-451, CWE-838, CWE-22, CWE-863, CWE-116.
Non-existent Domain
The following IP address 178.128.19.195 was used to mount the attack. When our team investigated this address it was found to be a non-existent domain.
Five CVEs weakened the Sri Lankan Domain
Our investigations further revealed that these five CVEs CVE-2002-0454, CVE-2002-0799, CVE-2000-0091, CVE-2008-1447, CVE-1999-0822 were found in the products (Qualcomm QPopper 4.0, Youngzsoft CMailServer 3.30/4.0, Inter7 vpopmail (vchkpw) 3.4.11, BIND 9.4.1-9.4.2, Qualcomm qpopper 3.0/3.0 b20) used by the Domain.
Here is a small analysis of these products –
- Three out of five CVEs are RCE type exploits (CVE-2002-0799, CVE-2000-0091, CVE-1999-0822).
- Public exploits for all five CVEs already exist.
- CVEs with RCE exploit were found in products such as Youngzsoft CMailServer 3.30/4.0, Inter7 vpopmail (vchkpw) 3.4.11 and Qualcomm qpopper 3.0/3.0 b20
Many Sri Lankan media outlets have described the threat actors as hacktivists but the exposed credentials on the dark web can be used by any malicious agent. The fact that these credentials have remained the same for almost eight years highlights the lack of security awareness among the organizations that host critical and essential data and services.
The need of the hour for all organizations is a proactive Attack Surface Management and Exposure management, especially for those entities that host sensitive information and data that are critical to the nation and its people.
About CSW
CSW is a US Department of Homeland Security Sponsored Common Vulnerability Exposure (CVE) Certified Numbering Authority (CNA). A leader in Attack Surface Management, exposure management and vulnerability research, CSW has helped organizations across the globe to improve their security posture and reduce their attack surface. Write to us at info@cybersecurityworks.com for more details.
Worried about a cyber breach?
Get a complete Attack Surface Management Service. Talk to us.









