The SolarWinds Orion Platform Software is a Network Management tool that is widely used by over 300,000 customers worldwide. Entities like defense, government agencies, software companies, and Fortune 500 organizations use this platform to monitor IT stack from infrastructure to application. SolarWinds confirmed in its security advisory that Orion update versions 2019.4 through 2020.2.1, released between March 2020 and June 2020, have been infected with malware known as SUNBURST/Solorigate.
Security agencies in the US are in a panic because SolarWinds is a widely used and popular product. Here are a few details that would help you understand the gravity of this breach.
Orion is used by the following:
- 425+ US Fortune 500 companies
- Top ten US telecommunication companies
- All five branches of the US military
- The US Pentagon, State Department, NASA, NSA, Postal Service, NOAA, Department of Justice, and the Office of the President of the United States
- Top five US accounting firms
- Hundreds of universities and colleges worldwide
Securin’s Insights and Key findings
A breach of this magnitude calls for a closer look. Here are a few key points from Securin’s Attack Surface analysis on known vulnerabilities and what has been weaponized to date.
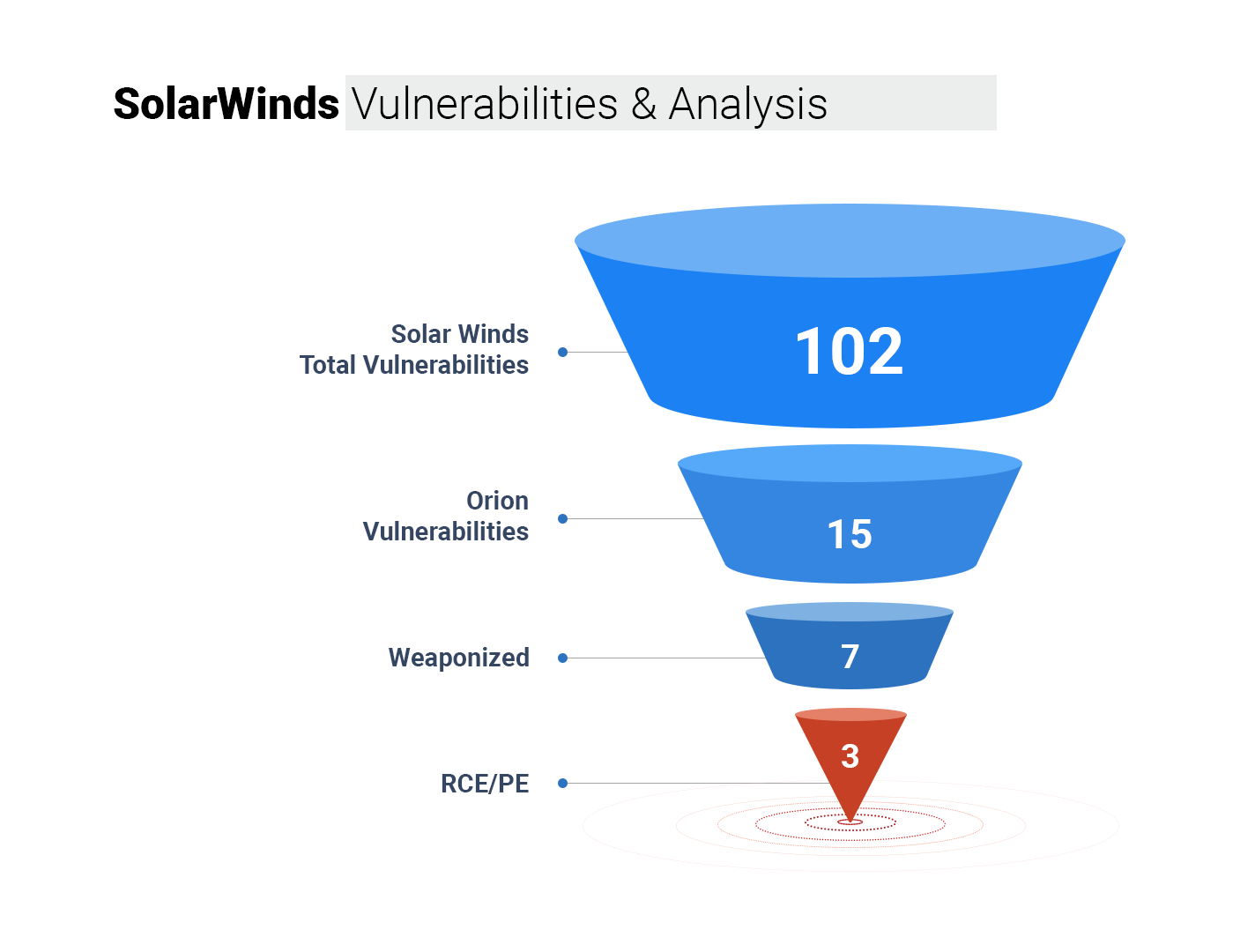
There are 102 vulnerabilities that exist in SolarWinds, out of which 15 are present in the Orion Platform Software.
- 4 CVEs are rated as critical, 1 as high, and 9 as medium.
- 11 are old vulnerabilities ranging from years 2010 to 2019.
- CVE-2019-9546, a critical Privilege Execution vulnerability, is suspected to be the culprit that allowed this breach. There are well-known exploits for this vulnerability.
- Analysis of Common Weakness Enumeration reveals that CWE-79 (Improper Neutralization of Input during Web Page Generation) is popularly used to exploit Orion’s vulnerabilities.
- We found no publicly associated APT groups and ransomware with these 15 vulnerabilities at the time of writing this analysis.
How Did the Attack Unfold?
SolarWinds’ security advisory revealed that it was compromised early in 2020, but there is reasonable doubt to surmise that it might have been attacked as early as 2019 when the FTP credentials of SolarWinds were leaked onto GitHub.
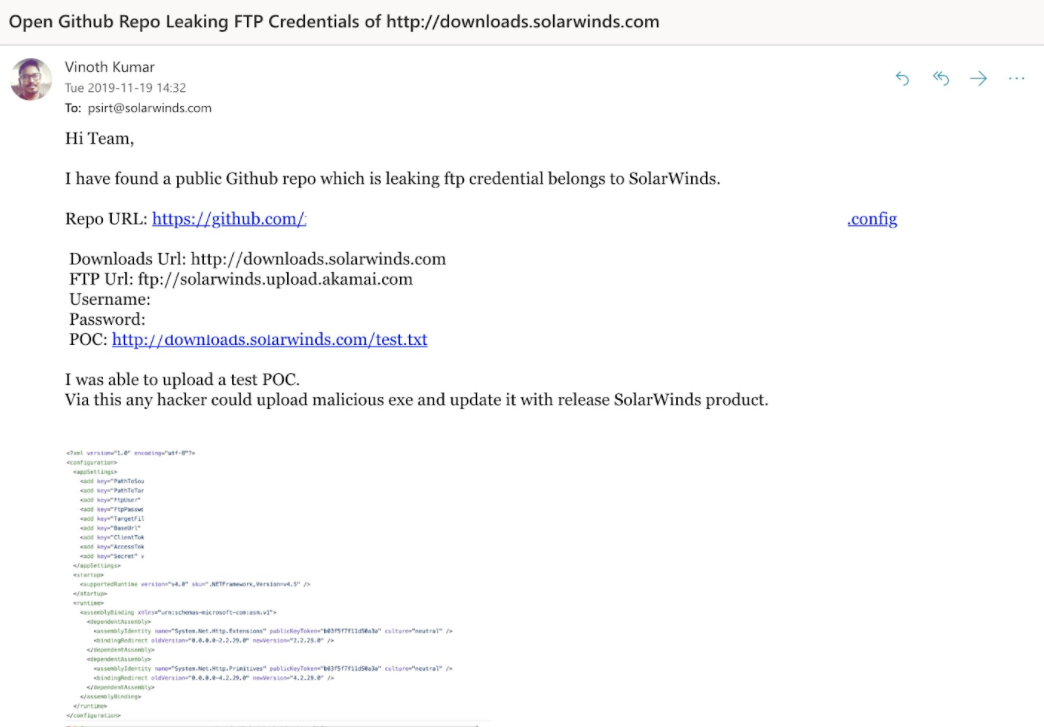
SolarWinds, however, maintains that the threat actors installed a backdoor to a key library in early 2020. This library was then delivered to select customers through their normal updating process. This led to SolarWinds Orion versions 2019.4 through 2020.2.1 HF1 being potentially affected. As an IT management platform, this backdoor provides a perfect getaway to an attacker who can enable or disable security tools and configurations or prevent patch applications that would mitigate the risk of these vulnerabilities.
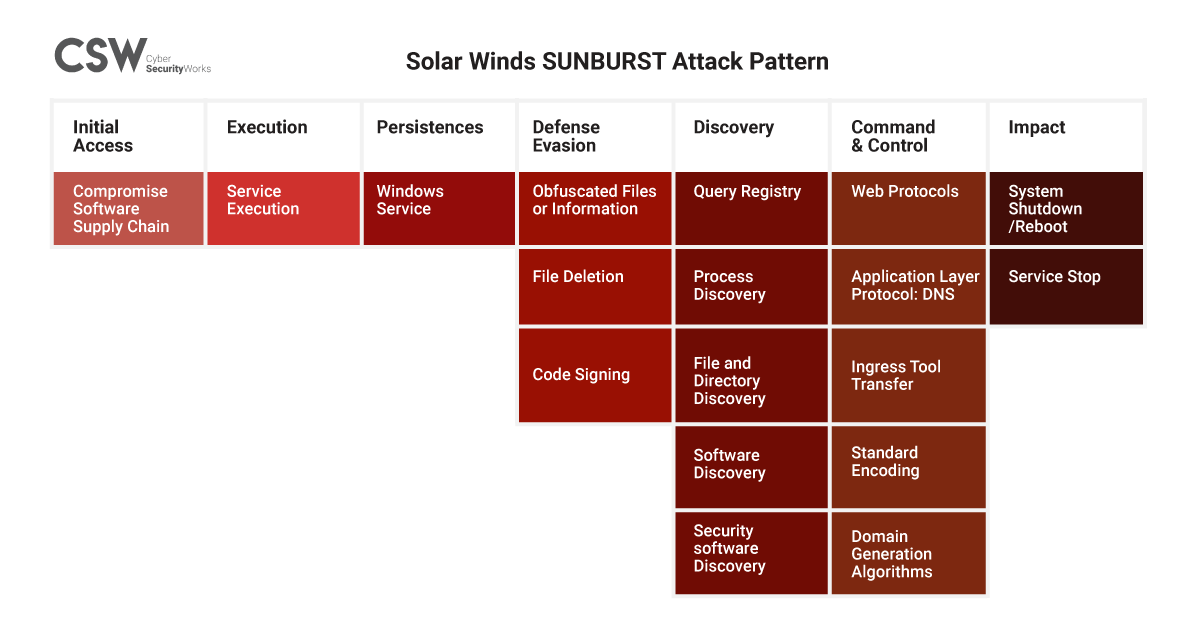
Here is a MITRE map of how this attack might have unfolded:
 Our exposure analysis identified 1,687 internet-facing SolarWinds’ products; 699 are from the US, and 56 are from India. Network Management Tools should never be exposed to the internet. Incidentally, Securin warned about six CVEs (CVE-2019-9017, CVE-2019-3980, CVE-2019-3957, CVE-2015-8220, CVE-2013-3249, and CVE-2018-12897) in our Cyber Risk series when we researched on potentially vulnerable products that could be breached during the COVID-19 lockdown.
Our exposure analysis identified 1,687 internet-facing SolarWinds’ products; 699 are from the US, and 56 are from India. Network Management Tools should never be exposed to the internet. Incidentally, Securin warned about six CVEs (CVE-2019-9017, CVE-2019-3980, CVE-2019-3957, CVE-2015-8220, CVE-2013-3249, and CVE-2018-12897) in our Cyber Risk series when we researched on potentially vulnerable products that could be breached during the COVID-19 lockdown.
This is a massive attack launched simultaneously at sensitive government agencies with the intent to cripple the country. The attackers have surreptitiously monitored the email communication of several federal agencies and have launched this attack. Here are a few recommendations to keep your organization safe:
- Patch all vulnerabilities related to SolarWinds.
- It is recommended to upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible.
- Isolate your network from SolarWinds’ servers and restrict the scope of connectivity until further investigation is done.
- Consider changing passwords to ensure the security of your environment.









