Did you know that the BlackCat ransomware group breached 60+ organizations in a single month?
Healthcare, public health, government, or energy—the group has stopped at nothing, and has made ransom demands ranging from $400,000 to $3 million USD. Our research shows that the BlackCat group exploits vulnerabilities in Windows operating systems and servers, exchange servers, and Secure Mobile Access products. Read on to learn how Securin can help you ward off such attacks.
BlackCat, also known as AlphaV, ALPHV, AlphaVM, ALPHV-ng, or Noberus, is a ransomware group that garnered the tag “Most Sophisticated Ransomware of 2021” within two months of its public footprint. Since being first spotted in November 2021, the BlackCat group has slowly made its way to the top of the charts. Researchers have also suggested that the group might have strong connections with REvil, DarkSide, BlackMatter, and Conti groups.
Recent Updates
The BlackCat group has been constantly adding victims to its dark leak site. Read more about BlackCat ransomware attacks.
BlackCat: A Cheat Sheet
-
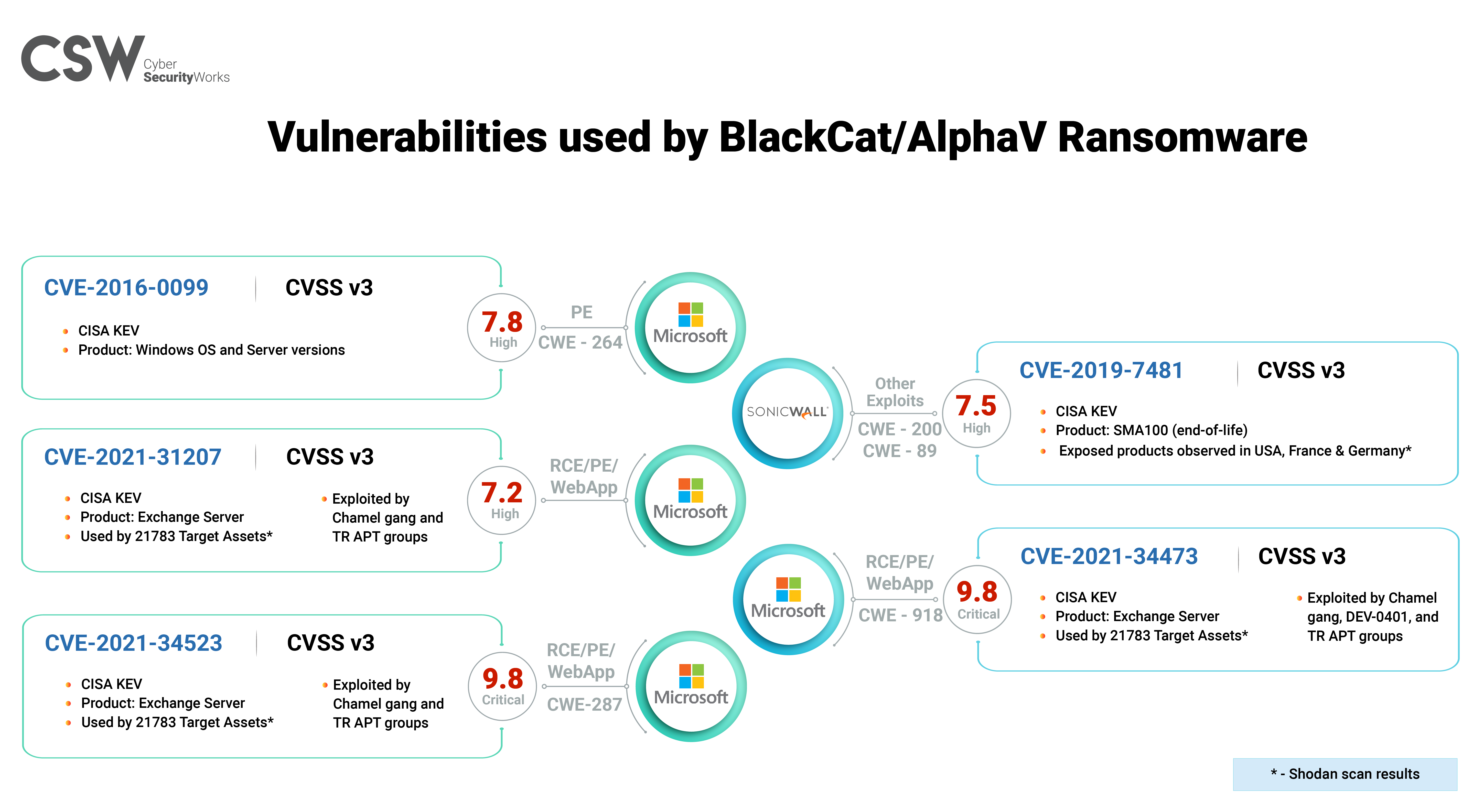
BlackCat has the methods to exploit five vulnerabilities – CVE-2016-0099, CVE-2019-7481, CVE-2021-31207, CVE-2021-34473, and CVE-2021-34523.
-
Interestingly, three vulnerabilities are of high severity. Although not of the critical severity category, they need to take precedence in the patching process owing to the associated threat context.
-
CVE-2021-31207, CVE-2021-34473, and CVE-2021-34523 are ProxyShell vulnerabilities known for their dangerous exploitation in vulnerability chaining attacks and have multiple threat actor associations.
-
CVE-2016-0099 is a six-year-old privilege escalation vulnerability in older versions of Microsoft Windows, which are still widely used.
-
CVE-2019-7481 is an SQL injection vulnerability in SonicWall Secure Remote Access devices that have reached their end of life. With no active support from the vendor, this vulnerability needs extra attention or a complete version overhaul.
-
The ransomware is deployed by APT groups: FIN7, FIN12, DEV-0504, and DEV-0237, to intensify their attacks.
How Does BlackCat Attack?
Below, we outline the group’s attack techniques and tactics.
Reconnaissance: TA0043
-
T1595: Active Scanning
-
T1589.001: Gather Victim Identity Information (Credentials)
Initial Access: TA0001
-
T1078: Valid Accounts
-
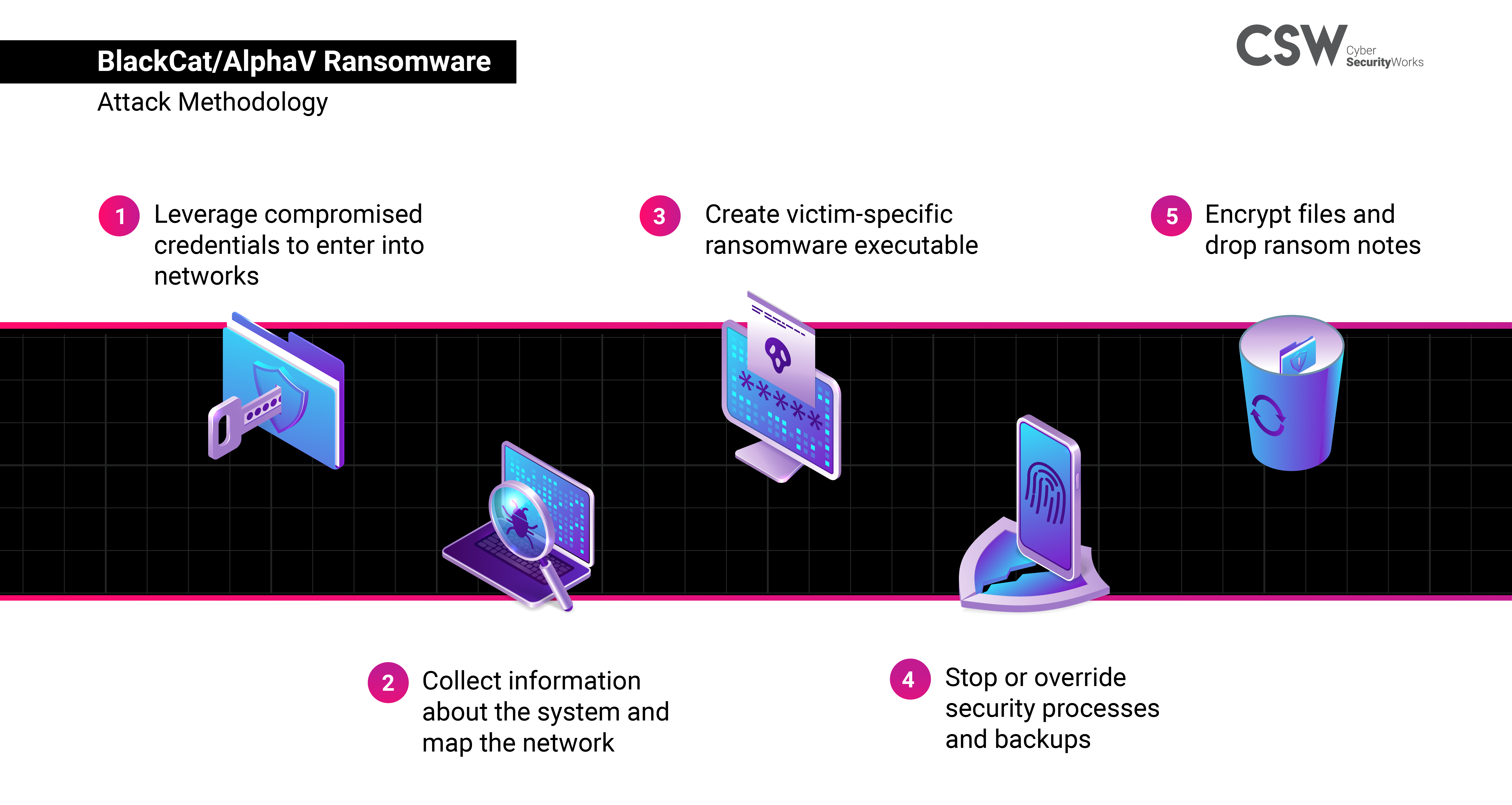
Leverages compromised credentials to enter networks
-
-
T1190: Exploit Public-Facing Application
-
Exploits unpatched Microsoft Exchange Servers (ProxyShell CVEs)
-
Persistence: TA0003
-
T1098: Account Manipulation
-
Creates new users and adds them to the local administrator group
-
Privilege Escalation: TA0004
-
TA1548.002: Abuse Elevation Control Mechanism: Bypass User Account Control
-
Uses built-in privilege escalation (UAC bypass, Masquerade_PEB, CVE-2016-0099)
-
Defense Evasion: TA0005
-
T1564: Hide Artifacts
-
Employs evasive tactics such as masking a tampered DLL to make it seem legitimate
-
Credential Access: TA0006
-
T1003.001: OS Credential Dumping: LSASS Memory, T1003.004: OS Credential Dumping: LSA Secrets
-
Creates dump file of LSASS process to steal credentials via malware or task manager
-
Discovery: TA0007
-
T1082: System Information Discovery, T1135: Network Share Discovery
-
Executes cmd.exe and net.exe to collect system and network information
-
-
T1018: Remote System Discovery
-
Uses WMIC and mounting network shares to enumerate remote systems
-
-
T1087.002: Account Discovery: Domain Account, T1487: Domain Trust Discovery
-
Uses ADFind (S0552) and ADRecon to gather Active Directory environment information
-
-
T1057: Process Discovery, T1083: File & Directory Discovery
Lateral Movement: TA0008
-
T1563.002: Remote Service Hijacking: RDP Hijacking
-
Utilizes remote desktop client to sign into target devices
-
-
T1570: Lateral Tool Transfer
-
Uses SMB to copy and launch the Total Deployment Software administrative tool, allowing remote automated software deployment
-
Collection: TA0009
-
T1005: Data from Local System
-
To steal intellectual property, attackers target and collect data from SQL databases
-
Command & Control: TA0011
-
T1090.003: Multi-hop Proxy
-
Disguises the source of malicious traffic by chaining together multiple proxies
-
Exfiltration: TA0010
-
T1567.002: Exfiltration Over Web Service: Exfiltration to Cloud Storage
-
Uses both MEGAsync and Rclone, which were renamed as legitimate Windows processes (for example, winlogon.exe, mstsc.exe) to exfiltrate sensitive data
-
Impact: TA0040
-
T1486: Data Encrypted for Impact
-
Uses PSExec to distribute ransomware and encrypt files
-
Employs the Double Extortion technique
-
-
T1489: Service Stop, T1490: Inhibit System Recovery
-
Stops operational services and obstructs recovery attempts
-
The Ransom Tactic
The BlackCat group demands ransom payments in Monero or Bitcoins (for an additional fee). Ransom demands ranging from $400,000 to $3 million USD are typical of the group. Interestingly, the ransom notes used are customized for every victim, sometimes with a unique data leak site, ensuring complete privacy for negotiations. In addition, the gang’s payment site is controlled by an access key, ensuring negotiation sites cannot be accessed even in the event of a ransomware code leak.
Interesting Features
The backbone of the ransomware group is a set of highly-customizable features that allow for sophisticated attacks across a range of environments.
-
Usage of the Rust framework, a new trend that is picking up in the threat circle, brings additional stability and integration possibilities.
-
The malware code is entirely command-line driven and human-operated, introducing a high degree of configurability.
-
Ransomware is capable of using four different encryption methods on victim data.
-
The code is built for cross-platform deployment, with support for Linux and Windows operating systems, and VMWare’s ESXi environment.
BlackCat is yet another affiliate of the Ransomware-as-a-Service (RaaS) practice, relying on compromised or privileged credentials and weaknesses in code to launch their attacks. This is the first ransomware with its code completely written in the Rust programming language, allegedly having in-built safety measures. The group is known to use methods enabling data encryption at alarming speeds, giving victims lesser chances of preventing extended damage. Its data leak site allows data searches by the victim’s name, passwords, and even confidential documents.
How Dangerous is BlackCat Ransomware?
While not all cyberattacks of the BlackCat group have come to light, the FBI released a warning in April 2022, declaring that the group was involved in successful attacks against 60 organizations in the previous month. The group has been observed targeting institutions regardless of sector—including healthcare, public health, government, and energy—across the US, Australia, Germany, and India.
Exploits Overlooked Exposures: From our research into the BlackCat group’s arsenal, we observe that it has not shied away from using exposures in many organizational networks, which are typically categorized as “low risk” vulnerabilities.
-
Local sockets: A socket, or a combination of ports and IP addresses, was leveraged to execute multiple instances of the ransomware simultaneously, speeding up the encryption process.
-
Open ports: Dynamic ports that are not commonly used, and are likely to be easily available, are targets. In one instance, the group is known to have established a server via the port to listen in on the machine’s activities.
-
Old vulnerabilities: The group targets old vulnerabilities (a 2016 CVE in Microsoft Windows) that organizations might not prioritize amidst the influx of more recent threats.
-
End-of-life software: BlackCat uses unpatched vulnerabilities in end-of-life software (a 2019 SQL injection flaw in SonicWall Secure Remote Access) to enter into vulnerable networks. Devices that are no longer supported by their vendors offer permanent attack vectors for hackers with malicious motives.
Has APT Group/Threat Associations: Threat actors that favor ransomware groups like Ryuk or REvil are now deploying the BlackCat ransomware payload in their attacks. APT groups like DEV-0504, DEV-0237, and FIN12 have been observed using the payload. Researchers have also observed FIN7 intrusions right before BlackCat ransomware incidents, leading us to believe that the threat actor could also be using the ransomware as a tool.
Adopts the Triple Extortion Method: The BlackCat ransomware group has adopted the latest threat in the ransomware scene: the new and emerging triple extortion method. Attackers steal data from the local machine and cloud servers and then execute ransomware. Then, they introduce additional pressure on the victim via DDoS attacks or data leaks. The group is also known to put up extorted data for sale in dark web forums.
The BlackCat ransomware group was called out in Securin’s Q1 2022 Ransomware Index Report as one of the new additions to our ransomware database, along with some noteworthy trends.
Recent BlackMatter/AlphaV attacks: Here is a look into some of the publicly disclosed attacks by BlackCat.
|
Organization |
Industry |
Region |
Timeline |
Impact |
| Gestore dei Servizi Energetici SpA (GSE) | Energy | Italy | September 2022 | Dark web data leak site claims to have stolen roughly 700GB of files |
| Accelya | Airline Technology | – | August 2022 | Emails, worker contracts, and other data stolen |
| Automotive supplier | Automotive | – | August 2022 | Three ransomware gang attacks within 2 weeks leading to data encryption and erasure of traces |
| Creos Luxembourg S.A. | Energy | Europe | July 2022 | Customer portals of Encevo and Creos became unavailable |
|
Bandai Namco |
Gaming |
Japan |
Not disclosed |
|
|
Hydra-Electric |
Aerospace Sensor Manufacturing |
Burbank, California |
Not disclosed |
|
|
Adler Display |
Marketing & Advertising |
Baltimore, Maryland |
Not disclosed |
|
|
Sinclair Wilson |
Accounting & Wealth Management |
Australia |
Not disclosed |
|
|
dusitD2 Kenz Hotel |
Hospitality |
Dubai |
Not disclosed |
|
|
COUNT+CARE Gmbh |
Information Technology |
Germany |
Not disclosed |
|
|
Florida International University |
Education |
US |
Not disclosed |
|
|
University of North Carolina A&T |
Education |
US |
Not disclosed |
|
|
University of Pisa |
Education |
Italy |
Not disclosed |
|
|
Federal State of Carinthia |
Government |
Austria |
3000 systems taken offline; $5 million ransom demanded |
|
|
Swissport |
Aviation |
Switzerland |
1.6TB data extorted with a portion leaked |
|
|
Oiltanking GmbH and another oil company |
Energy |
Germany |
233 gas stations across Germany affected |
|
|
Moncler Group |
Fashion |
Italy |
Temporary outage; data leak |
|
|
Enterprise Resource Planning (ERP) services provider |
Consumer |
Middle East |
Not disclosed |
|
|
Oil, gas, mining, and construction company |
Energy |
South America |
Not disclosed |
How to Detect BlackCat in Your Environment
Here are the indicators of compromise that can help you detect a BlackCat ransomware attack.
| SHA256 Hashes: | C2 IPs: |
|
731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161 f837f1cd60e9941aa60f7be50a8f2aaaac380f560db8ee001408f35c1b7a97cb 731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161 80dd44226f60ba5403745ba9d18490eb8ca12dbc9be0a317dd2b692ec041da28 |
89.44.9.243 37.120.238.58 45.153.160.140 94.232.41.155 142.234.157.246 152.89.247.207 23.106.223.97 51.83.57.149 45.134.20.66 198.144.121.93 139.60.161.161 5.255.100.242 185.220.102.253 89.163.252.230 146.0.77.15 |
What Can Organizations Do to Prevent a BlackCat Attack?
The BlackCat ransomware group is soon becoming one of the favorite payloads of many threat actors. With this in mind, here are some measures that organizations can adopt to stay safe from a ransomware attack.
-
Patch the vulnerabilities used by the group, and ensure no unused ports/instances are left hanging.
-
Set up multi-factor authentication, implement session timeouts, and practice good password hygiene.
-
Perform a regular Attack Surface Management scan to discover exposures in your assets, domain controllers, active directories, servers, and all cloud-connected deployments.
-
Perform a penetration test on your systems to identify if they are vulnerable via unidentified exposures.
-
Regularly back up data in secure storage devices.
How Can Securin’s Ransomware Assessment Help?
Securin has been researching ransomware groups and the methods they use to invade networks since 2019. Our comprehensive database of more than 310 vulnerabilities (and counting) used by ransomware groups is the most extensive compilation in the industry today. Securin’s expertise in ransomware research translates into our Ransomware Assessment service that can help organizations understand the following facets of their cybersecurity environment:
-
Exposure to ransomware
-
Known and unknown internet exposures
-
Critical exposures and what needs to be fixed first
Sign up for Securin’s ransomware assessment today. Ensure you are not the next victim on a dark leak site.









