Conti has been in the news consistently since August 2021, warranting a joint warning from the Cybersecurity Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and National Security Agency (NSA). The warning alerted organizations of the threat posed by the Conti ransomware group and the vulnerabilities exploited.
A risk-based approach is the requirement of the moment if organizations want to stay ahead of dangerous sophisticated ransomware groups, such as Conti.
Timeline | Conti Develops Log4J Exploitation Chain
Conti’s Playbook and Tools | Conti Attack Methodology |
IOCs and MITRE Map | Interesting Trends | Conti Vulnerabilities
Recent Development
Conti Shuts Down: According to threat intel analyst, Ido Cohen, Conti’s servers were shut down. Conti ransomware shut down its last public-facing infrastructure: a pair of Tor servers used to leak data and negotiate with victims, concluding the last chapter of this notorious cybercrime brand.
Intel Management Engine Attack: The Conti ransomware gang has been working on a series of firmware attack tactics that might allow users to access privileged code on compromised machines, according to Conti’s leaked messages. This includes attacks against embedded microcontrollers, such as the Intel Management Engine (ME), which is a privileged component included in Intel’s CPU chipsets that may totally bypass the operating system.
Rust Developers Targeted: On May 20, 2022, security researchers alerted the public to an attack targeting Rust developers with malware aimed directly at infecting GitLab Continuous Integration pipelines. A campaign dubbed CrateDepression combines typosquatting and impersonating a prominent Rust developer to push a malicious ‘crate’ to a Rust dependency community repository.
Costa Rica Declares National Emergency: Costa Rican President, Rodrigo Chaves, declared a national emergency following cyberattacks from the Conti ransomware group on multiple government bodies. Conti ransomware revealed 672 GB of sensitive data on Costa Rican government entities. In addition, Conti threat actor “UNC1756,” along with their affiliate, has claimed sole responsibility for this cyberattack.
ContiLeaks: A new Twitter account named ContiLeaks posted links to an archive of Conti’s internal chat messages on February 27, shortly after the ransomware group offered support to Russia in its war against Ukraine. The leaked data also included domains used for compromises with BazarBackdoor, which is malware used to access targeted networks. In addition, DHS CISA updated the Conti ransomware advisory with Indicators of Compromise (IoCs) containing over 100 domain names utilized in criminal operations.
The ContiLeaks account revealed over 30 vulnerabilities associated with the Conti ransomware, bringing the total of Conti ransomware-associated CVEs to 44.
Internal chats leaked from the Conti ransomware group revealed the inner workings of the group, including details on 30 vulnerabilities exploited by the group and affiliates and specific insights into its processes after gaining entry, such as how it targets Active Directory.
Securin’s data researchers and security analysts discuss the latest developments, the tools, techniques, and procedures used, as well as the vulnerabilities explored by Conti in 2021-22 in this blog.
Who is Conti?
Conti ransomware is a Ransomware-as-a-Service (RaaS) operation believed to be controlled by the Russian cybercrime group, Wizard Spider. The ransomware shares some of its code with the infamous Ryuk ransomware, which went out of the news in July 2020.
Conti-nuous Attacks Through January 2022
Conti’s prolific track record continued into 2022, with four attacks being reported within the first two months of the new year. Let us take a look at the different recent incidents involving the Conti group.
|
Ransomware Attack Incident |
Time Period |
Sector |
Demand/Ransom |
| Costa Rica | April 22, 2022 | Finance | – |
| Panasonic Canada | April 15, 2022 | HR and accounting | – |
| Wind Turbine | March 21, 2022 | IT | – |
| TrustFord | April 8, 2022 | Manufacturing | – |
|
October 25, 2021 – February 18, 2022 |
Distribution |
– |
|
|
February 02, 2022 |
Foods and Beverages |
– |
|
|
January 21, 2022 |
Manufacturing |
$15 million ransom |
|
|
January 15, 2022 |
Marketing Agency |
2.5 GB data stolen |
|
|
December 2021 – January 2022 |
Banking |
13.88 GB data stolen; ransom amount unknown |
|
|
December 2021 |
Government |
300 GB data stolen |
|
|
December 12, 2021 |
Foods and Beverages |
– |
|
|
December 2, 2021 |
Hospitality |
– |
|
|
December 2021 |
E-commerce |
Few million dollars in ransom |
|
|
November 27, 2021 |
Energy |
– |
|
|
November 2021 – present |
Government |
– |
|
|
October 2021 |
Jewelry |
69000 files leaked |
|
|
September – October 2021 |
Manufacturing |
1.7 TB data stolen, $7 million ransom |
|
|
September 18, 2021 |
Communications Industry |
– |
|
|
September 3, 2021 |
Software |
1 TB data stolen |
|
|
June – August 2021 |
Manufacturing |
250 GB data stolen |
|
|
June 2, 2021 – Present |
Engineering and Technology |
– |
|
|
Till June 2021 |
Insurance |
– |
|
|
Till June 2021 |
Engineering & Technology |
– |
|
|
Till June 2021 |
Internet services |
– |
|
|
May 21, 2021 – Present |
Healthcare |
– |
|
|
May 18 – Present |
Healthcare |
Attempt unsuccessful |
|
|
May 17 – Present |
Healthcare |
$20 million |
|
|
May 6 – Present |
Government |
– |
|
|
May 4, 2021 |
IT |
$2.6 million |
|
|
March – April 2021 |
Education |
$40 million |
Conti’s ‘Playbook’ Leak
In August 2021, a disgruntled Conti affiliate released the threat actor’s ‘playbook’ which listed out the techniques, tactics, and procedures as well as commonly exploited vulnerabilities.
Some vulnerabilities mentioned in the technical manual were the 2017 Microsoft Windows SMB 1.0 server vulnerabilities, CVE-2021-34527 in Windows Print Spooler Service, and CVE-2020-1472 in Microsoft’s Active Directory Domain Controller systems, better known as the ZeroLogon exploit.
The playbook also identified four Cobalt Strike server IP addresses used by Conti actors to communicate with their command and control (C2) server. The FBI and CISA also observed that Conti actors use different Cobalt Strike server IP addresses for different victims.
-
162.244.80[.]235
-
85.93.88[.]165
-
185.141.63[.]120
-
82.118.21[.]1
Here are some tools and command-line utilities routinely used by the Conti gang. This data was leaked by one of Conti’s disgruntled affiliates.
|
Tools and Command-line Utilities |
Purpose Served |
|
Cobalt Strike Beacon |
Gives backdoor access to compromised systems |
|
ATERA Agent |
Used for persistence in an infected network |
|
Ngrok |
Helps identify local server ports to establish a virtual tunnel to the local host for smoother data exfiltration |
|
Rclone |
Used to exfiltrate data from infected systems and backups |
|
Armitage |
Used to identify targets, exploits, and advanced post-exploitation features |
|
SharpView |
.NET port from PowerView tool of a PowerShell-based PowerSploit offensive toolkit |
|
SharpChrome |
Used for decrypting logins and cookies on Google Chrome |
|
SeatBelt |
Used to collect system data like OS version, UAC policy, and user folders |
|
ADFind |
Active Directory query tool |
|
PowerShell |
Used to disable Windows Defender |
|
SMBAutoBrute |
Used in brute-force attacks on current domain |
|
Kerberoasting |
Used in brute force attack to crack the hash of a Kerberos password |
|
Mimikatz |
Used for dumping passwords from memory |
|
GMER |
Used for identifying and disabling security solutions |
|
RouterScan |
Used for discovering network devices and extracting passwords using an exploit or brute force |
|
AnyDesk |
Used for persistence attacks |
Conti Leverages Log4Shell
After the discovery of the critical Log4Shell vulnerability in the Apache framework in December 2021, many threat actors, including Conti, began exploiting the new vulnerability, as organizations scurried to fix their unpatched systems.
Not long after our researchers observed Conti exploiting the Log4J vulnerability, VMware vCenter Servers were hacked. Approximately 40 VMware products were found vulnerable to the Log4j bug, and without the proprietary fixes to avoid an attack, Conti was able to use the vulnerability to move laterally through unpatched servers. The attack on VMware led Shutterfly, a photography giant, to be subsumed in a ransomware attack that affected 4000 devices and 120 VMware ESXi servers.
In due course, Conti also became the first ransomware group to have a complete exploit chain for the Log4JShell vulnerability, thereby raising concerns among cybersecurity professionals worldwide about a spate of supply-chain Conti attacks leveraging the critical Apache bug.
Interesting Trends
These interesting trends pertaining to the Conti ransomware group were observed over the last year.
1. Conti swears allegiance to the Russian Government
As the Russian invasion of Ukraine commenced, the Conti ransomware gang issued a statement to its adversaries in the West, not only pledging allegiance to the war efforts carried out by the Russian government, but also warning of retaliatory attacks on critical infrastructure if any nation were to oppose the war or plan cyberattacks against Russia.
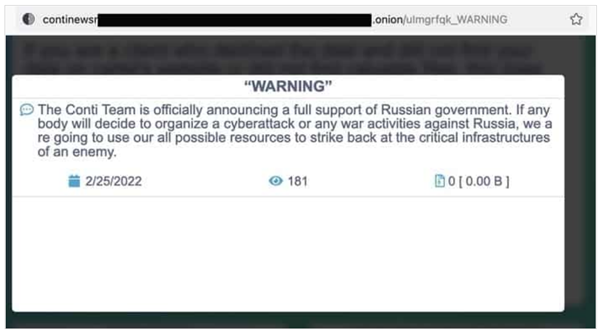
A screenshot of Conti’s warning message posted by gang members
Shortly after the release of the message, Conti revised it to soften the tone and extend support for the Russian government. The updated warning mentions that Conti ‘does not ally with any governments’ and that they ‘condemn the ongoing war’.
.png)
A screenshot of the revised Conti warning message
2. Conti takes over TrickBot malware operations
The Conti ransomware syndicate took over the failing TrickBot malware operations in mid-February 2022. As TrickBot malware is detectable by antivirus vendors, the Conti gang aims to replace it with the stealthier BazarBackdoor malware, which is already being used to compromise high-value targets.
3. Hackers conduct SEO poisoning attacks
On February 07, 2022, hackers conducting an SEO poisoning campaign were spotted using tools like ATERA agent, BATLOADER malware, Ursnif, and techniques very similar to those executed by the Conti Group. The hackers were attempting to infiltrate organizations through Microsoft Visual Studio 2015, Zoom, and TeamViewer, among others.
4. Conti takes novel approach to destroy backups
Soon after the Ireland Health Service attacks in June 2021, Conti focussed their attention on developing new ways to compromise Veeam’s backup software used for disaster recovery. The Conti gang uses three tools–Cobalt Strike, Atera, and Ngrok–during their infection routines and subsequently impersonate a privileged backup user to grant themselves Veeam backup privileges to help them destroy all backups.
5. Conti apologises for attack
The Conti ransomware gang leaked thousands of records stolen from UK-based jewelry store, Graff, during their October 2021 attacks. However, in November 2021, the hackers issued a surprising apology for their decision to leak data that included files on powerful world personalities, like the crown prince of Saudi Arabia.
6. Wizard Spider partners with Shatak APT
The threat group ITG23 (TrickBot Gang, Wizard Spider) has been partnering with another threat group, TA551 (Shatak), to distribute TrickBot and BazarBackdoor malware, which are then used to deploy Conti ransomware on compromised systems.
Shatak APT distributes email-based malware through phishing techniques. Researchers predict that the Conti gang may be using Shatak as an initial access vector.
7. Conti sells access to victims
The Conti ransomware affiliate program seemed to have altered its tactics by offering organizations that had refused to pay or negotiate a ransom, a way to retrieve their encrypted files by selling them access to the stolen data, before selling confidential files on victim shaming blogs.
8. Conti helps revive Emotet botnet
After law enforcement took down Emotet Botnet in early 2021, the Conti gang seem to have convinced some members of the Emotet team to revive it. Being the most widespread malware, Emotet can wreak havoc as it has done in the past, deploying Ryuk, Conti, ProLock, Egregor, DoppelPaymer, and other ransomware on exposed systems.
We analyzed the CVEs being exploited by the Conti group. Here is our detailed analysis:
-
Of the 44 vulnerabilities, three have CVSS v3 scores of 10.
-
23 of 44 vulnerabilities have remote code execution and privilege escalation capabilities.
-
Seven of the 44 vulnerabilities have denial-of-service capabilities.
-
Eight vulnerabilities are categorized as web app exploits; others are uncategorized.
-
12 vulnerabilities have critical-severity ratings (9.8 to 10), 30 CVEs have high-severity ratings (7.2 to 8.1), and one has a medium-severity rating (5.9).
-
Six vulnerabilities are categorized as Improper Input Validation issues (CWE-20), while eight have the weakness enumeration, CWE-269 (Improper Privilege Management).
Conti Attack Methodology
Looking at multiple attacks involving Conti ransomware, we have pinpointed the following to be their overall attack vector:
-
Initial Attack Vectors
-
Social engineering (phishing)
-
Vulnerable firewalls
-
Internet-facing RDP servers
-
Privilege Escalation
-
Gaining domain administrator privileges or equivalent
-
Disabling security measures
-
Execution
-
Targeting servers, endpoints, backups, sensitive data
-
Gathering live IP addresses and ports
-
Dumping credentials
-
Installing backdoors and deploying C2C (for example, Cobalt Strike beacon)
-
Exfiltrating as much data as possible
-
Launching ransomware; using RCE vulnerabilities to distribute ransomware to all servers identified
-
Injecting Logon scripts in GPO whenever the computer starts up and joins the domain
Conti Attack MITRE Map
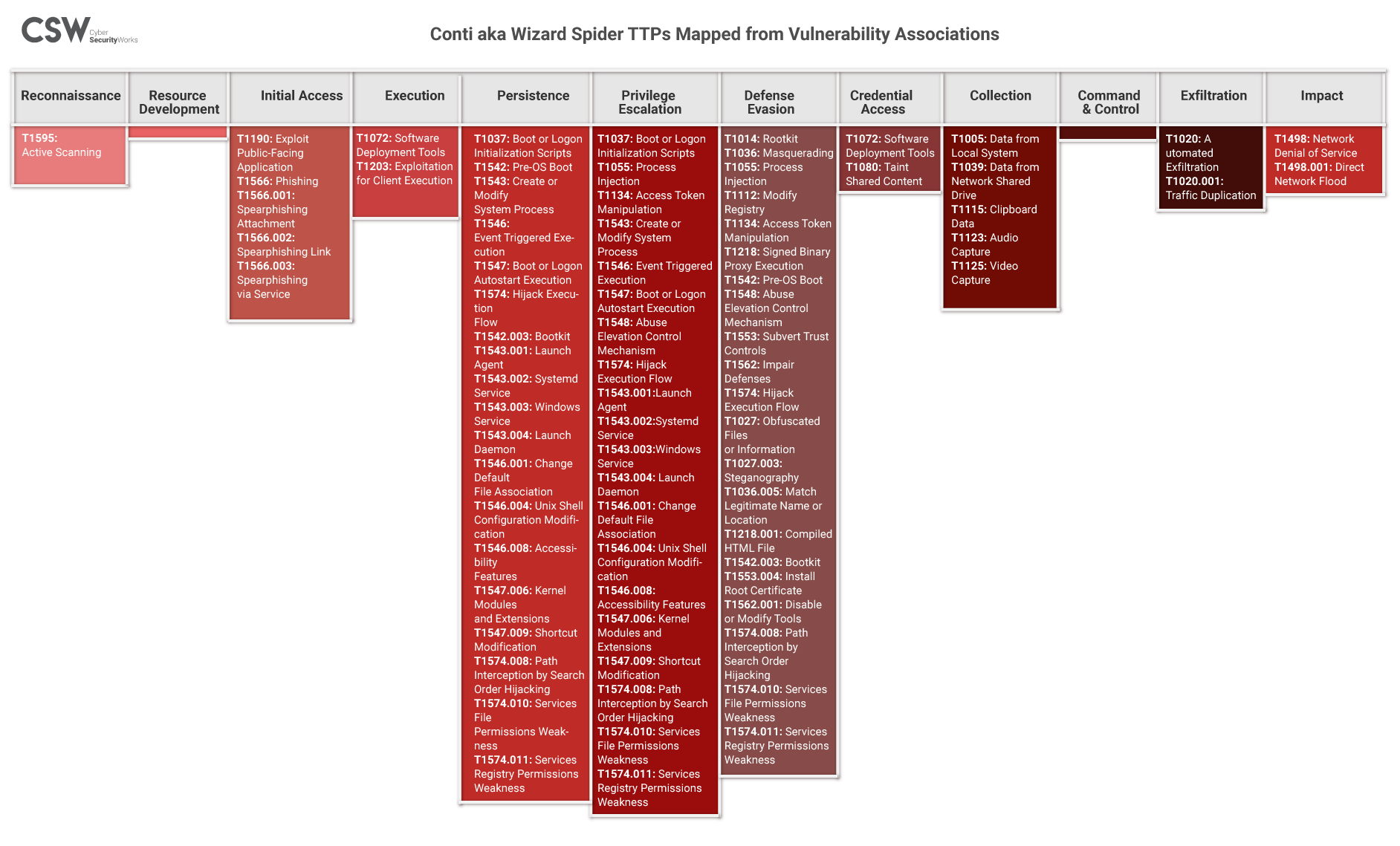
Indicators of Compromise (IoCs)
What Does The Future Hold?
In November 2021, the Department of Homeland Security CISA released a list of known exploited vulnerabilities (KEVs), containing 383 vulnerabilities as of February 2022. Of these 383 vulnerabilities, seventeen vulnerabilities have been associated with the Conti gang.
Of the seventeen vulnerabilities exploited by Conti ransomware, eleven are part of the Department of Homeland Security CISA’s KEV list and should be patched immediately.
As highlighted in Securin’s Ransomware Spotlight Report 2022, vulnerabilities that were discovered in 2020 and earlier accounted for 91% of the total vulnerability count (288) as of December 2021. This emphasizes the need for periodic vulnerability management and patching to maintain good cyber hygiene.
Companies ought to seek out more effective approaches towards vulnerability management by adopting vulnerability assessment platforms that can present threat data in real-time, as well as identify, investigate and categorize vulnerabilities based on their weaponization.
Aaron Sandeen, CEO of Securin
Worried about how susceptible your organization is to a ransomware attack? Adopting a risk-based approach and prioritizing critical vulnerabilities according to threat context is the need of the hour.
Get a Ransomware Exposure Assessment done today!
Click here to talk to us.









