On Aug 11, 2021, Accenture, a multinational IT Consulting and Services company, became the latest victim of LockBit 2.0 Ransomware. Our researchers investigated the vulnerabilities that LockBit exploits to compromise their targets and here is our analysis.
Accenture’s ransomware attack came to light when a senior correspondent from CNBC noticed a post from Lockbit offering to sell their data. LockBit claims to have stolen 6 TB worth of Accenture’s data and has set the ransom amount to $50 Million. While the official sources from Accenture have maintained that they have contained the attack, the data has been restored from backup.
LockBit hit back by posting 2300 files that contained corporate communication data and has hinted that more will follow. Here’s a screengrab of some files that were released by Lockbit.
Recent LockBit Activities
LockBit 3.0: The LockBit ransomware group just released its latest ransomware-as-a-service offering, LockBit 3.0, and along with it a first for the Dark Web: a bug-bounty program. According to screen grabs of messages shared by LockBit actors, the bounty program offers rewards for PII on high-value targets, security vulnerabilities, and more.
Mandiant is aware of LockBit claims: Mandiant is looking into claims made by the LockBit ransomware group claiming they penetrated the company’s network and stole data. The ransomware gang said today that the 356,841 files they purportedly took from Mandiant will be posted online on a new page on their data leak website. LockBit has yet to reveal any files it claims to have stolen from Mandiant’s computers, as the file listing on the leak website is empty.
The LockBit Switch: The Cybercrime group Evil Corp now uses LockBit ransomware on targets’ networks to evade sanctions imposed by OFAC.
Foxconn Hit by LockBit: Yet another victim to the list. Foxconn electronics manufacturer confirmed that one of its Mexico-based production facilities was hit by a ransomware attack in late May. Operators of the LockBit ransomware gang claimed responsibility, but no further information was provided by the company.
French Ministry of Justice Targeted: On January 27, 2022, the French Ministry of Justice reported that cybercriminals had breached their systems, stolen sensitive files, and were threatening to post them on their public-facing victim-shaming site. The threat actor encrypted files using LockBit 2.0 ransomware.
Researchers discovered that the governmental department had not patched their BIG-IP instances. As a result, it is believed that the threat actors exploited CVE-2021-22986 in this attack. CVE-2021-22986 is, a critical unauthenticated remote code execution vulnerability in the iControl REST interface affecting both BIG-IP and BIG-IQ products. F5 had released patches for the vulnerability in March 2021.
We urge organizations to patch any instances of the vulnerability on their F5 products to avoid the possibility of a ransomware attack.
On October 18, 2021, Accenture released its company’s financial report for the fourth quarter and full fiscal year where they finally confirmed that data was encrypted and stolen during the Lockbit 2.0 ransomware attack in August 2021. However, Accenture has not publicly acknowledged any data breach due to the ransomware attack and has therefore not filed any data theft investigation.
LockBit 2.0 ransomware had previously claimed to have stolen 6TB of files from Accenture systems and demanded $50 million in ransom.
Bangkok Airways Attack: On August 23, 2021, Bangkok Airways reported a LockBit 2.0 ransomware attack where 200 GB of files were encrypted. Ethiopian Airlines reported a separate ransomware attack on their network around the same time. The attacks come within a week of the Accenture breach, as a result of which the LockBit ransomware gang also claims to have accessed credentials of both airline companies and that of an airport. Accenture has denied the claims made by LockBit yet again.
“We have completed a thorough forensic review of documents on the attacked Accenture systems. This claim is false.”
Could Accenture have avoided the attack?
Yes. Accenture noticed a Lockbit 2.0 attack on 30 July, when some client files were stolen but chose to ignore it citing that none of the data was sensitive enough to warrant an official warning to partners. It was only after the ransomware attack on 12 August that Accenture issued a warning.
A screenshot of the digital timer on the Lockbit landing page, mentions that it was an insider who helped them compromise Accenture’s systems. Although it is uncertain if this is true or if this was used as a diversion, Accenture was swift to refute the claims and has underplayed the impact created by the ransomware on their systems thereafter.
Significantly, it was reported early this month that the LockBit gang was recruiting corporate insiders for millions of dollars to help them breach and encrypt networks.
What is also alarming is that Accenture, being a cybersecurity services provider, chose to delay warning its partners of an impending ransomware attack.
LockBit Ransomware
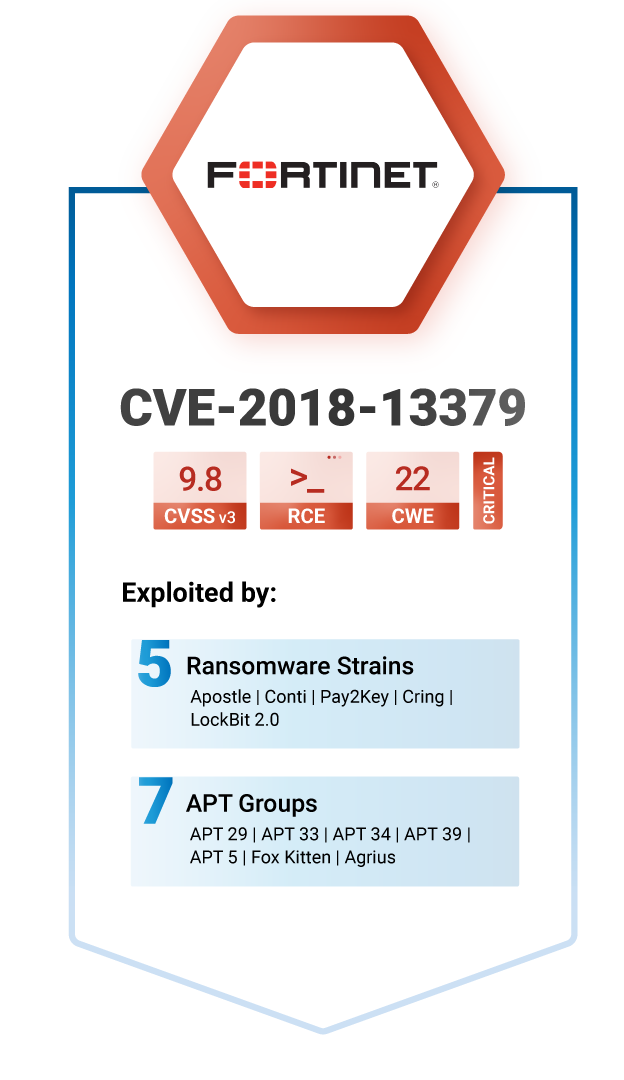
We investigated the vulnerabilities that LockBit exploits to mount attacks on their targets and found that they use CVE-2018-13379 – a critical vulnerability that exists in FortiOS SSL VPN and has previously known exploits. This weakness allows an attacker on the same network to send malicious service location protocol (SLP) requests to take control of it.
The vulnerability has a CVSS v3 score of 9.8. Although the vulnerability has no known RCE or PE exploits, it has been exploited by several ransomware in the past, namely, Apostle (November 2020), Cring (January 2021), Pay2Key (2020), and Conti (December 2019).
This vulnerability is also being exploited by seven Advanced Persistent Threat (APT) groups including the newly minted Iran-based APT group, Agrius. These findings were called out in our Ransomware Q2 index update.
We also warned about this vulnerability way back in December 2020 when a threat hacker group named ‘PumpedKicks’ leaked credentials for 50,000 Fortinet VPN devices used in over 140 countries. The group had also published exploits that could be used to compromise CVE-2018-13379.
Following the credential leak, CISA, NSA, and Fortinet had also warned users to mitigate this vulnerability at the earliest.
CVE-2018-13379 has been categorized under CWE-22 (Improper Limitation of a Pathname to a Restricted Directory)—a Path Traversal error category that belongs to the OWASP’s top 25 most dangerous software weaknesses. A patch was released in 2019 for the vulnerability.
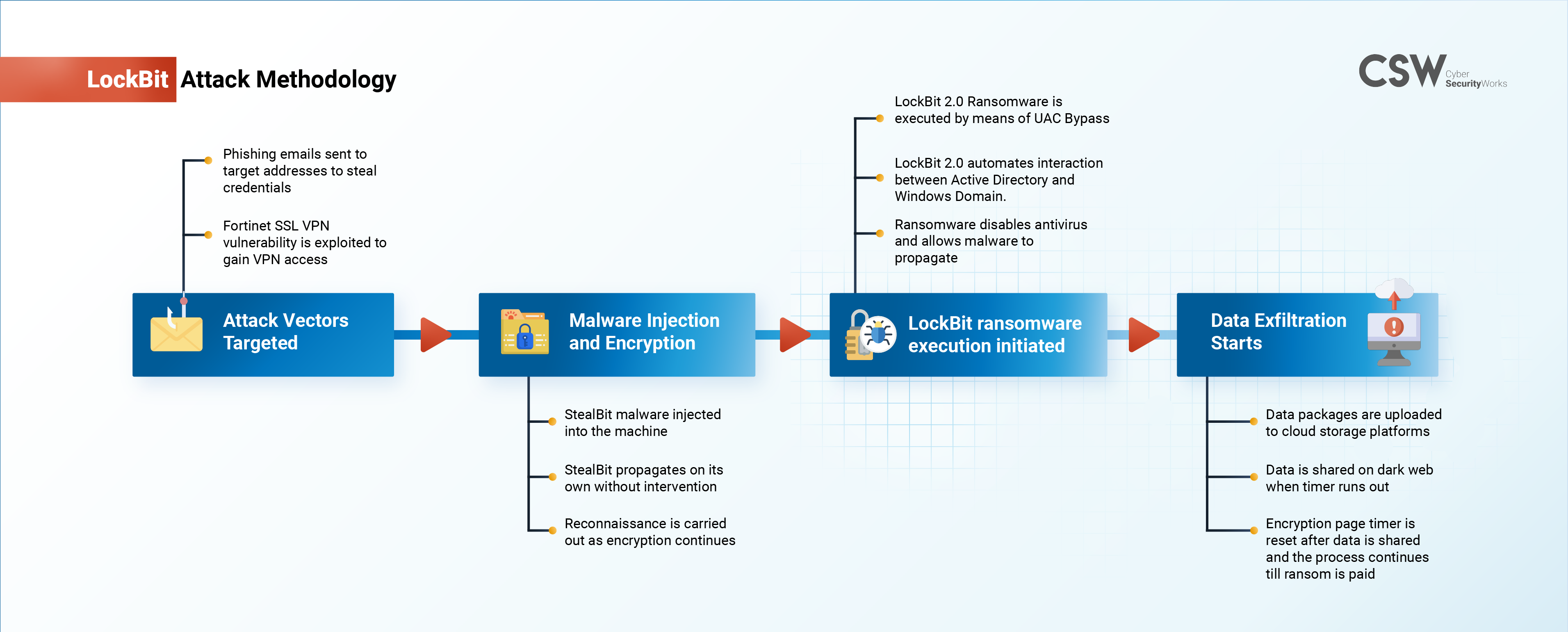
Lockbit Attack Methodology
The LockBit affiliates are well-known for their double extortion technique, where they upload stolen and sensitive victim information to their dark web site LockBit 2.0, while threatening to sell or release the stolen information if their ransom demands are not met. This double extortion method is used to coerce a victim into paying the ransom demanded. The second version of LockBit RaaS was released in June 2021 with an updated built-in information-stealing trojan known as StealBit.
Lockbit affiliates, as observed by researchers, identify devices that are mission-critical and often include NAS devices, backup servers, and domain controllers.
Here are details of a typical LockBit attack sequence:
Initial Access:
-
LockBit affiliates send phishing email addresses within the target company. Initial attack vectors are set when they are able to steal partner information.
-
LockBit affiliates exploit CVE-2018-13379 to obtain valid VPN accounts. They simply append the following code to the vulnerable URL:
/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession -
They also gain credential-based access to Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) by obtaining accounts from brokers.
Propagation:
-
After initial access, the StealBit trojan is injected into the system by a human after which it propagates through the system and infects other hosts on its own, without the need for human oversight.
-
The trojan performs reconnaissance and continues to spread during the encryption phase. This allows it to cause maximum damage faster than other manual approaches.
-
The new version of Lockbit 2.0 Ransomware is executed by means of a UAC bypass which runs in the background while the device is being encrypted. The ransomware automates the interaction and encryption of Windows domains with Active Directory group policies. It adds a unique approach to interact with the Active Directory to spread rogue malware to local domains by disabling antivirus, making it easier for new malware operators to engage in operations.
Exfiltration:
-
The Lockbit 2.0 actors then begin data exfiltration using publicly available web services. The data packages are usually uploaded to services, including MEGA’s cloud storage platform.
| IoCs |
|
SHA256: ffbb6c4d8d704a530bdd557890f367ad904c09c03f53fda5615a7208a0ea3e4d 286bffaa9c81abfb938fe65be198770c38115cdec95865a241f913769e9bfd3f |
Exposure Analysis
Our exposure analysis using Shodan indicates that, on 16 August 2021, there were more than 96,000 Internet-facing Fortinet VPN devices and networks that are potentially vulnerable to these attacks, if they are not patched immediately.
|
Internet-facing devices running |
Top ports and servers |
| |
|
Lockbit MITRE ATT&CK Mapping
Staying Alert
Our ransomware research has identified 266 vulnerabilities associated with ransomware that attackers use to infiltrate and attack their victims. These 266 vulnerabilities need to be at the top of every organization’s remediation plan and must be prioritized for patching. As of today, 134 vulnerabilities are actively trending in the dark web and while any vulnerability associated with ransomware needs to be considered as high-risk exposure, these trending vulnerabilities need to be addressed immediately.
The LockBit ransomware attacks have snowballed since the Accenture attack, with several attacks reported worldwide, in Chile, Italy, Taiwan, and the UK. With ransomware attacks escalating every day, global multi-national organizations such as Accenture need to rethink their cybersecurity strategy. They need to implement an approach where a continuous assessment of vulnerabilities and prioritization for remediation is undertaken to reduce their security debt and lack of cyber hygiene.









