{Update September 2021}: The Conti group that started trending early this year, is still going strong. In a newly disclosed data breach from June 2021, SAC Wireless, a US-based Nokia subsidiary, reported 250 GB of data stolen and encrypted systems.
{Update August 2021}: In a recent development in early August 2021, a disgruntled Conti RaaS affiliate leaked some of the gang’s core training material, as he was unsatisfied with his cut for a ransomware attack. The publicly available data includes Cobalt Strike C2 IP addresses and ransomware attack tools and training details, all the more reason for organizations to watch out for all possible attack vectors weaponized by the Conti group.
The Conti group is associated with three vulnerabilities. If these had taken precedence in the CVE patching priority, the series of Conti attacks could have been avoided.
CVE-2020-0796 and CVE-2018-13379 were warned against in CSW’s Ransomware Reports published in February and May 2021.
Let us take a look at the different recent incidents in which the Conti group has been involved.
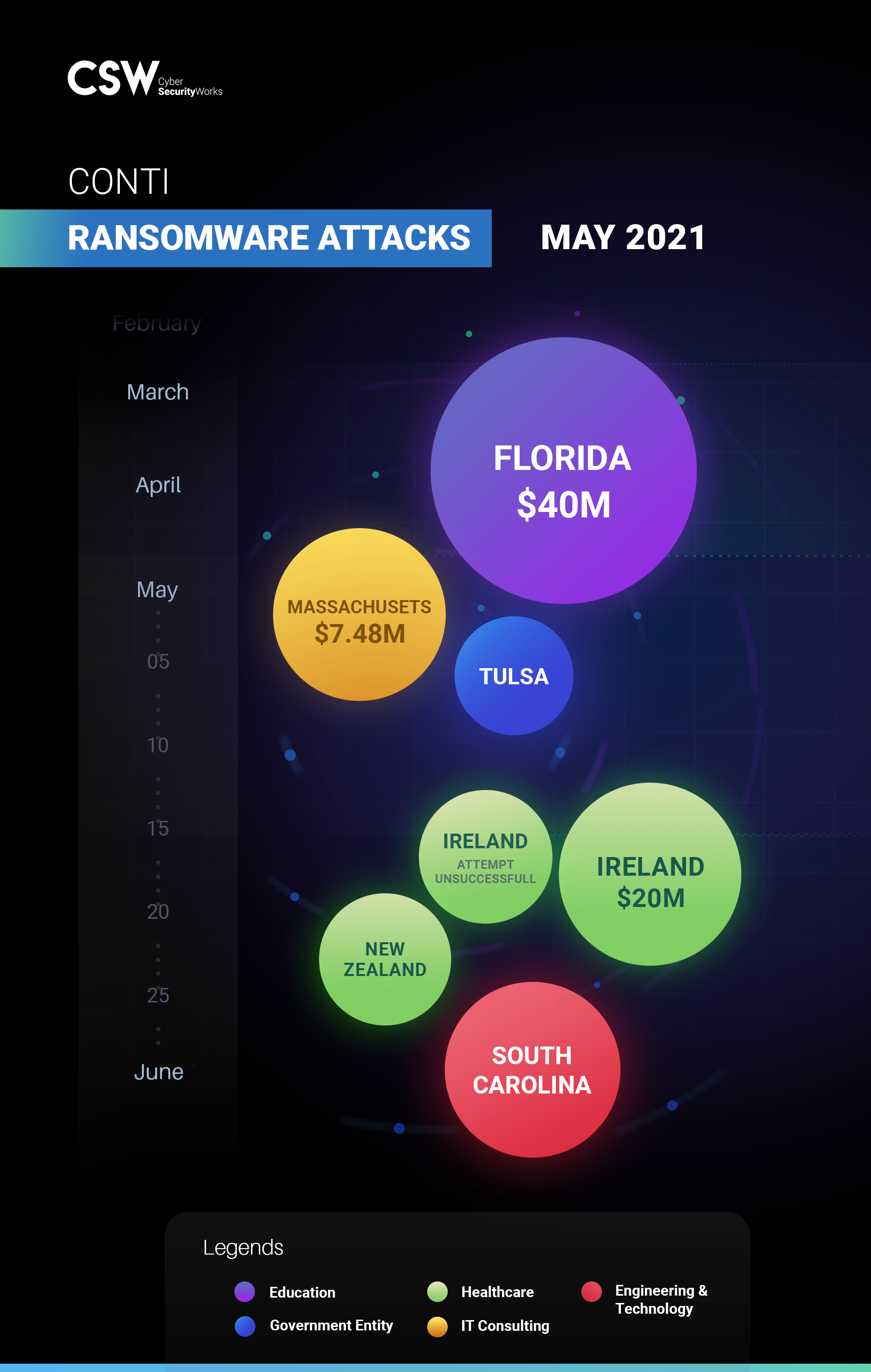
The Ireland HSE incident shook the health industry, closely following in the wake of the Oil industry’s Colonial Pipeline attack; IT systems had to be shut down, leading to chaos in rendering regular health services. Exagrid paid a $2.6M ransom in the form of 50.75 Bitcoins for a decryption tool and to prevent data from being leaked. In more recent updates in the last week of June 2021, Conti claimed responsibility for an attack on the city of Tulsa in early May, leaking over 18,000 city files on the Dark Web. Three Canadian companies – an Internet provider and an engineering firm, both from Ontario, and a Quebec-based insurance broker – have also fallen victim to the group, according to Conti’s website.
Conti – A Cheat Sheet We analyzed three CVEs being exploited by the Conti group – CVE-2020-0796,
|
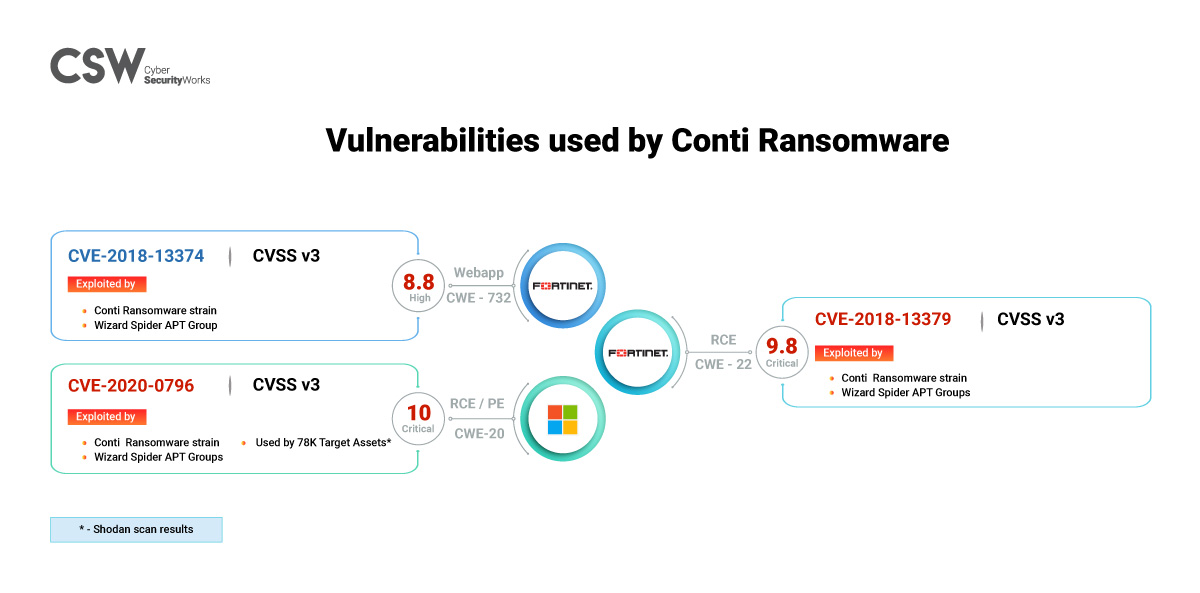
It is widely believed that Russia’s Wizard Spider Advanced Persistent Threat (APT) group uses the Conti ransomware in its attacks.
Global Exposure
A Shodan analysis of CVE-2020-0796 brings up over 75,000 deployments, mainly focused in Taiwan and Japan. Windows 10 Home is the most widely used OS susceptible to CVE-2020-0796 exploits.
There are over 60,000 deployments of FortiOS worldwide, according to Shodan, with the US ranking first on the list.
Attack Methodology
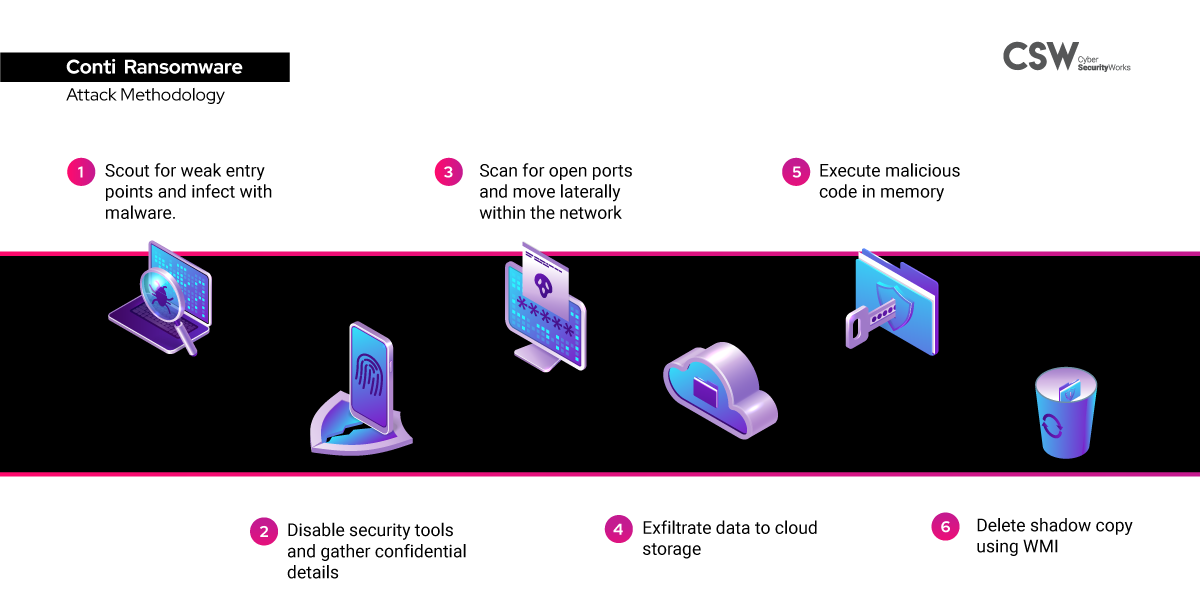
Looking at multiple attacks involving Conti ransomware, we have understood the following to be their overall attack methodology.
-
Scout for weak entry points in devices and infect them with IcedID payload, followed by BazarLoader malware.
-
Use batch files to disable security tools through the created backdoor.
-
Deploy Cobalt Strike beacon to gather confidential details
-
Scan to identify open ports
-
Utilize a combination of Remote Desktop Protocol (RDP), PsExec and Server Message Block (SMB) to worm its way laterally within the network
-
Exfiltrate data to cloud storage through command line tools like RClone
-
Stealthily deploy Cobalt Strike beacon to attached devices
-
Execute malicious code in memory across all active systems
-
Delete shadow copy using Windows Management Instrumentation (WMI)
-
Ransomware continues ploughing through until detected
Coincidentally, on June 1, 2021, the FBI sent out a warning regarding New Zealand based Mega cloud storage being used by ransomware groups like Conti, for data storage.
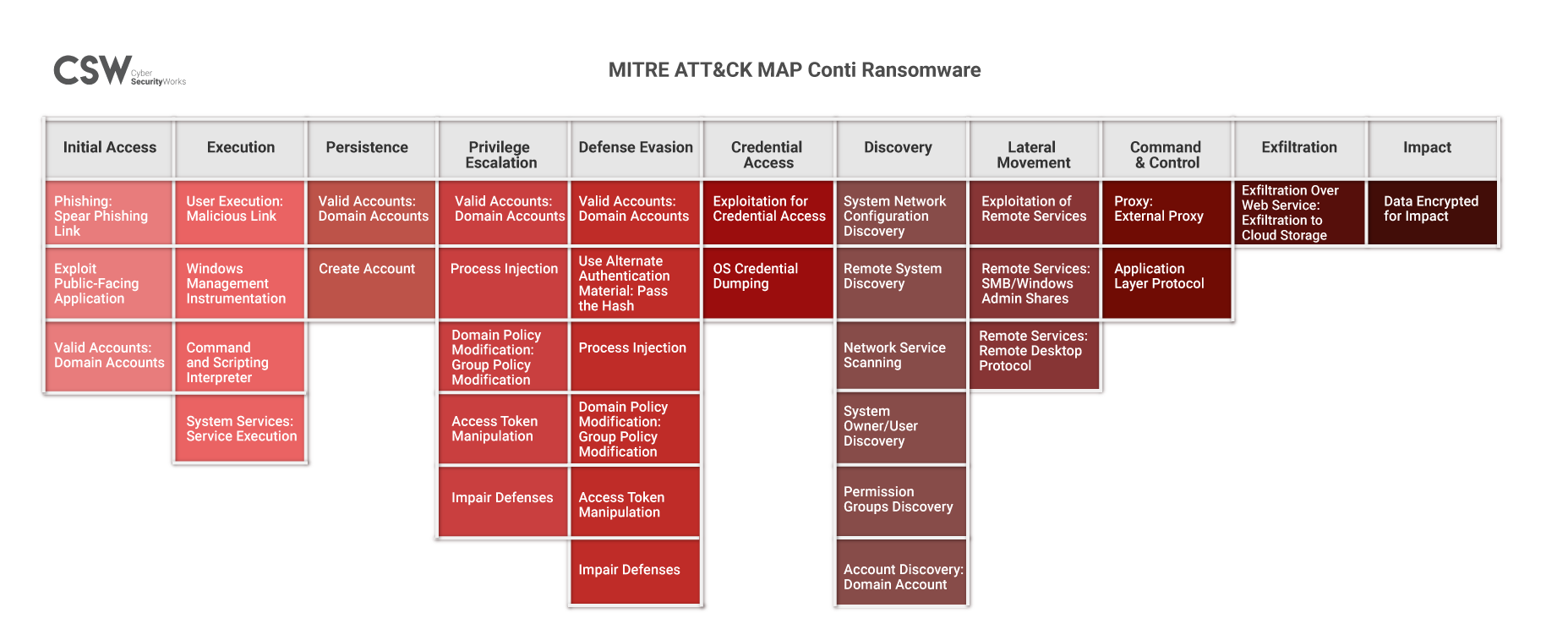
MITRE ATT&CK Mapping
| Indicators of Compromise |
|
SHA 256: d3c75c5bc4ae087d547bd722bd84478ee6baf8c3355b930f26cc19777cd39d4c f092b985b75a702c784f0936ce892595b91d025b26f3387a712b76dcc3a4bc81 e64e350861b86d4e05668bc25e6c952880f6b39ca921496ccce1487dbf6acab6 707b752f6bd89d4f97d08602d0546a56d27acfe00e6d5df2a2cb67c5e2eeee30 03b9c7a3b73f15dfc2dcb0b74f3e971fdda7d1d1e2010c6d1861043f90a2fecd b524ed1cc22253f09d56f54d8ded4566b63352ff739f58de961f8a5bebb0fad9 1ef1ff8b1e81815d13bdd293554ddf8b3e57490dd3ef4add7c2837ddc67f9c24 c14f8bc656284715516f26935afe487a1d584f56ffabbcb98f2974f6ca6cd3a4 e16fea1b8874cc6b26e7e2df9697f03f86efa82247bb3b2922f1d05052dbcbb4 5d8a701110d58ab7c1aa8bae6bc9d5358b8cd508115891320e6af6c68f3bbd74 ebeca2df24a55c629cf0ce0d4b703ed632819d8ac101b1b930ec666760036124 D236d64b7bf9510ea1746d10a4c164a2ef2c724cc62b2bca91d72bdf24821e40 2579148e5f020145007ac0dc1be478190137d7915e6fbca2c787b55dbec1d370 |
A thorough ransomware analysis is the need of the hour
The vulnerabilities CVE-2020-0796 and CVE-2018-13379 are currently trending, although they were discovered more than a year back. This is a clear indication of the importance of patching older vulnerabilities and not just the newly discovered high-severity ones. In fact, as highlighted in CSW’s Ransomware Report, vulnerabilities that were discovered in 2020 and earlier accounted for 97% of the total vulnerability count (260) as of March 2021.
The recent series of attacks is an example of how attackers might be taking it slow, waiting for bigger opportunities leading to crippling disruption. Adopting a risk-based approach and prioritizing critical vulnerabilities based on threat context is the need of the hour.
Reach out to CSW for assistance with vulnerability analysis and prioritization.









