{Updated on November 11, 2021}: On November 4, 2021, a new threat actor called the Tortilla Gang was identified as actively hacking Exchange Servers and breaching corporate networks using the ProxyShell vulnerabilities, leading to device encryption by deployment of Babuk ransomware. The Tortilla gang was also noted using the China Chopper webshell on breached servers. It is still uncertain whether Tortilla is an affiliate of the original Babuk gang, or if they are using a strain of the source code that was released on hacker forums in September 2021. Most of the attacks targeted US-based companies although other attacks in Germany, Thailand, Brazil and the UK, were also attributed to the Tortilla gang.
On July 23, 2021, Microsoft published an advisory about a new NTLM relay attack called PetitPotam. The PetitPotam technique (tracked as CVE-2021-36942) performs a relay attack that does not rely on the Microsoft Print System Remote Protocol (MS-RPRN) API, but instead uses the Microsoft Encrypting File System Remote Protocol (MS-EFSRPC), which maintains and manages operations on encrypted data that is stored remotely and accessed over a network. This vulnerability can allow a remote attacker to take full control of a domain controller, and thus, an entire Windows domain.
Soon after the proof-of-concept (POC) of the attack was released on July 22, Microsoft issued a security advisory to mitigate the issue. CISA issued an alert to Microsoft customers to fix the NTLM issue, but unfortunately, the update was inefficient and PetitPotam was still open to active abuse.
It was not until August 23 that security researchers discovered that the new LockFile ransomware was actively abusing the faulty patch to the PetitPotam vulnerability, post-exploitation, to gain access to domain controllers and spread across the network. The LockFile ransomware had been exploiting the Microsoft ProxyShell since August 13 and most likely used the ProxyShell vulnerabilities to gain access to victims’ networks before abusing the PetitPotam flaw.
Microsoft Exchange servers were actively being exploited by the ProxyLogon vulnerabilities in early 2021. The Exchange instances are now back again, dubbed as ProxyShell. Tracked as CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207, the ProxyShell vulnerabilities can allow an attacker to execute arbitrary code on a victim’s system and be able to run code remotely without authentication, if the vulnerabilities are chained. The ProxyShell vulnerabilities are also being used to exploit networks and install backdoors which can later be used as access points for persistence attacks. After breaching unpatched Exchange servers, threat actors drop web shells that allow them to upload malicious tools and execute them.
Interestingly, CISA issued an alert to Microsoft on August 21 regarding these vulnerabilities in MS Exchange.
Our CVE Analysis
CSW researchers looked at ProxyShell and PetitPotam vulnerabilities. Here is their analysis:
-
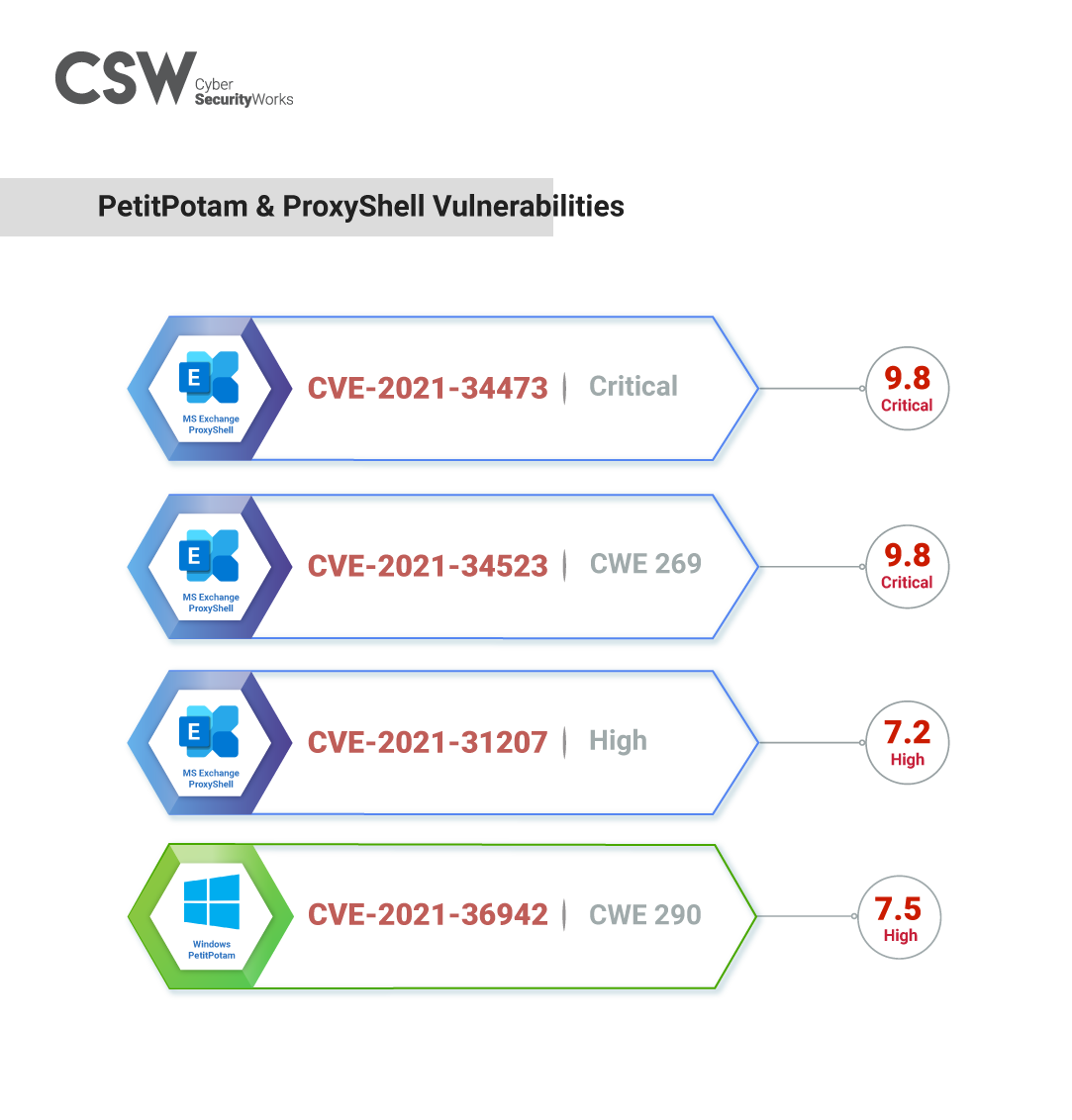
CVE-2021-34473 is a critical vulnerability (CVSS 9.8) that can be exploited to execute custom code remotely. This is a pre-authorization path confusion vulnerability that can result in ACL bypass, effectively giving access to backend URLs. A full working proof-of-concept exploit is available for the vulnerability as well.
-
CVE-2021-34523 is a critical remote code execution vulnerability with a CVSS v3 score of 9.8. The CVE targets open instances of the PowerShell Backend and has a full working exploit online.
-
CVE-2021-31207 is a high vulnerability with a CVSS v3 score of 7.2. This is a security feature bypass vulnerability that can cause post-authorization arbitrary file writes, the end result being remote code execution by attackers. An exploit is available online for the vulnerability.
Security patches for all the three ProxyShell vulnerabilities were released in April 2021.
-
CVE-2021-36942 is a high-impact vulnerability with a CVSS v3 score of 7.5. Researchers have also recently released a proof-of-concept exploit that can take advantage of the vulnerability to compromise Windows Servers. The PetitPotam vulnerability directly affects the Encrypting Files System Remote protocol (MS-EFSRPC).
Microsoft claimed that new micro-patches were released with the August 2021 Patch Tuesday update, to address the PetitPotam vulnerability and that installing Windows Update and patch would mitigate the issue. Though initially lauded for a quick resolution, it was soon discovered that the patches were incomplete, thereby allowing remote attacks.
Unlocking LockFile ransomware
Not much is known about the newly minted LockFile ransomware yet.
Our researchers did a deep dive to find out more about the new ransomware.
We noted that the email address disclosed to the target to negotiate the ransom (contact@contipauper.com) might point to a possible association with the Conti group, although it is still highly uncertain.
The color schemes of the ransom notes are similar to that of the Conti group, but the wording of the ransom message and the communication methods are very similar to the LockBit 2.0 ransomware operation.
The LockFile ransomware uses a unique intermittent encryption scheme to evade ransomware defenses. The novel file-encrypting malware scrambles only every 16 bytes of a file so that the file is partially readable and thereby tricks the defense mechanisms in place to block ransomware attacks. This technique of partially encrypting files has been a new trend observed by researchers and notably used by the BlackMatter, DarkSide, and Lockbit 2.0 ransomware in their exploits.
Vulnerable Products
With a new surge in attacks on Microsoft Exchange products, CSW researchers identified certain products that were more vulnerable to active exploits than others.
The ProxyShell vulnerabilities affect Microsoft Exchange Servers 2013, 2016, and 2019.
Individuals and organizations using Windows 7 Service Pack 1 or Windows Server 2008 R2 Service Pack 1 and later are encouraged to do a system backup and get an updated version to fix the PetitPotam vulnerability.
What is the Global Exposure?
Our researchers found direct CVE exposures for the ProxyShell vulnerabilities on Shodan on August 18. The exposure was the same for all three ProxyShell CVEs and points to more than 80,000 potentially vulnerable Internet-facing MS Exchange products.
No exposure for the PetitPotam vulnerability was found on Shodan at the time this blog was written.
Our analysts encourage you to update and patch your systems now.
Our analysts also encourage MS Exchange users to install the latest cumulative updates to patch the ProxyShell vulnerabilities and use the unofficial partial patch for the PetitPotam vulnerability to block the relay attack. PetitPotam attacks can also be blocked by applying a NETSH RPC filter that helps to block access to vulnerable functions in the Encrypting Files System Remote protocol API.
CSW analysts urge administrators to install the latest updates as well as create offline backups of their servers on priority.
CSW’s in-depth research helps organizations become more resilient against ransomware. We recommend organizations get a Ransomware Assessment done to know the gaps, understand the exposure, and become resilient to ransomware attacks in the future.









