REvil ransomware uses six vulnerabilities to target its victims. If these had been remediated and patched on priority, JBS—the world’s largest meatpacker—could have escaped this attack.
Securin warned about these vulnerabilities in its Ransomware Spotlight Report published in February 2021.
On May 30, 2021, JBS, the world’s largest meat producer, fell victim to a REvil ransomware attack forcing the company to shut down its operations in the US, Canada, and Australia. This disruption to the food and meat industry halted cattle slaughter and resulted in increased meat prices during the Memorial Day weekend in the US. It also stopped beef production in Canada and Australia, and it took around a week to restore operations.
Sources indicate that an APT group named Pinchy Spider (from Russia) might be behind this attack.
We know that attackers are going after critical sectors such as food, manufacturing, energy, and oil & gas to create the maximum disruption and collect millions of dollars as ransom. Colonial Pipeline paid over $5 million to its attackers to restore the gasoline supply. CNA Financial paid a whopping $40 million— one of the largest ransomware payments to date. The FBI recovered $2.3 million—about half of the ransom paid by Colonial Pipeline—after gaining access to the bitcoin account where the money was deposited. Most recently, JBS paid an $11 million ransom to attackers to protect its customers and resume operations.
Most ransomware gangs like REvil are going after organizations whose supply chain, if affected, can cause widespread panic and chaos.
REvil has so far attacked the Telecom website of Sri Lanka, Fujifilm in Japan, and Sol Oriens, a nuclear weapons subcontractor to the US Department of Energy, just in the month of May 2021, and it will continue to go after critical entities that would not hesitate to pay the ransom. The latest in the spate of attacks by REvil is a cyberattack on Invenergy, a renewable energy company based in the US, and on Grupo Fleury, the largest medical diagnostics company in Brazil. A $5 million ransom has been supposedly demanded in the latter.
Securin’s analysts delved deep into the vulnerabilities the group goes after and provide actionable insights that would help organizations stay safe from these types of attacks.
All about REvil
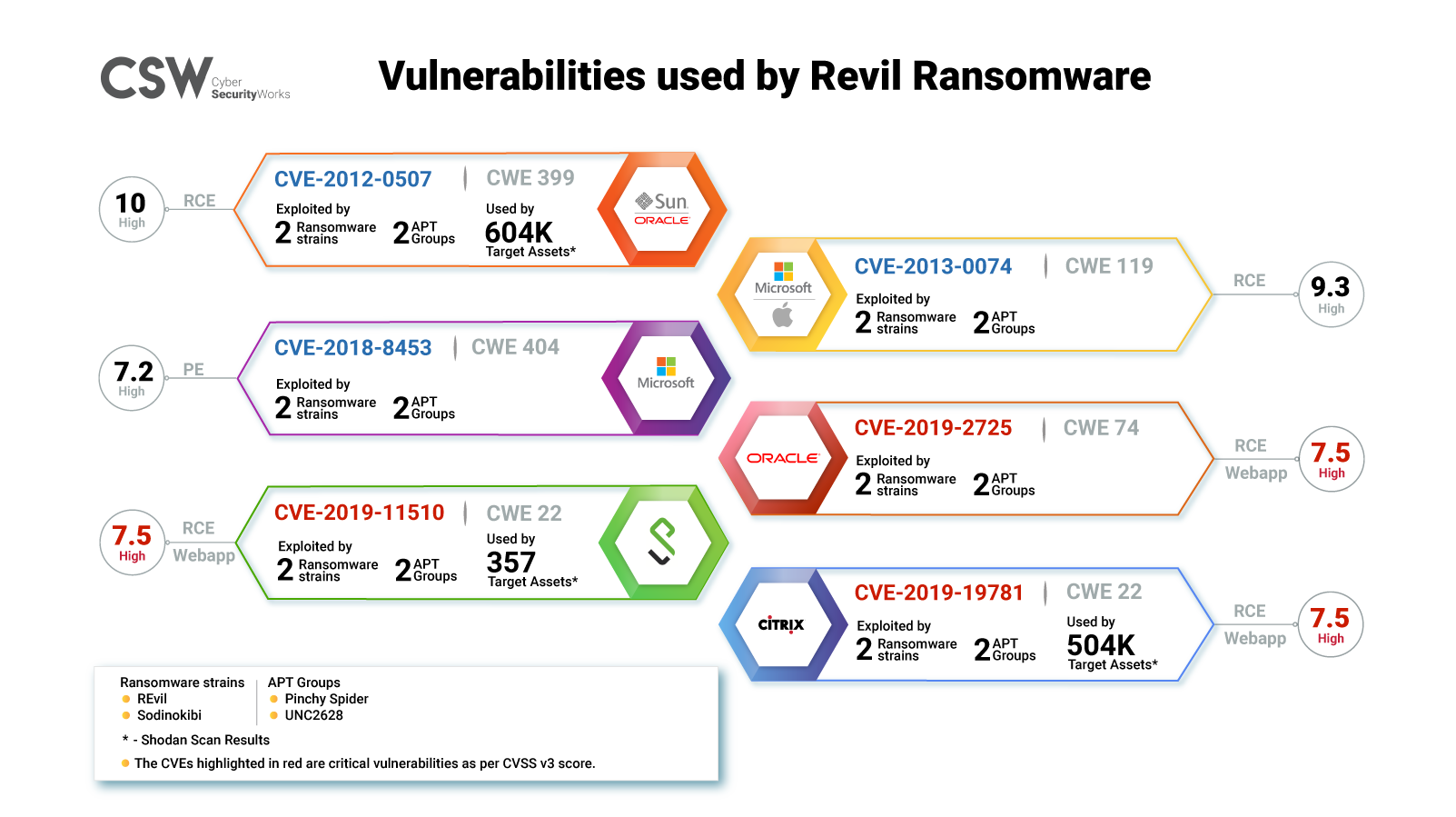
REvil ransomware gangs typically target six vulnerabilities, and incidentally, all of them are featured in Securin’s Ransomware report published in February 2021.
Securin also called out two of these vulnerabilities in 2020 as part of its reports on the Cyber Risk in Virtual Private Networks (VPNs) and Remote desktops.
REvil Cheat Sheet
Here are a few quick facts about these vulnerabilities:
-
REvil typically targets its victims through software vulnerabilities, Remote Desktop Protocol (RDP) sessions, and phishing.
-
Out of the six vulnerabilities in the list, five are Remote Code Execution (RCE), and the sixth CVE-2018-8453 enables Privilege Escalation (PE).
-
CVE-2012-0507, CVE-2013-0074, CVE-2018-8453, and CVE-2019-2725 are found in Microsoft and Oracle products such as Windows, JRE, etc.
-
CVE-2019-19781—a Citrix vulnerability—is a favorite of ransomware gangs and is exploited the most. To date, this vulnerability is found to be associated with at least ten ransomware families apart from REvil.
An excerpt from Securin’s Cyber Risk in Remote Desktop report published in June 2020
- CVE-2019-11510, a Pulse Secure vulnerability, is yet another favorite of ransomware gangs as it creates a pivot through the VPN endpoint, allowing for easy access to internal systems. This vulnerability is associated with five ransomware families.
An excerpt from Cyber Risk in VPNs published in May 2020
-
Our analysts have found that all six vulnerabilities have been trending in the past few months in hacker channels and the dark web.
-
The REvil ransomware is associated with a Russian APT group named Pinchy Spider and an uncategorized group called UNC2628.
-
Sectors and industries that REvil typically targets include manufacturing, telecommunications, information technology, law, computer hardware, tourism, pharmaceuticals and biotechnology, banking, insurance, agriculture, construction, education, healthcare, media and entertainment, finance, food and beverage, hospitals, and e-commerce.
-
CWEs that enabled these vulnerabilities are CWE-404, CWE-22, CWE-74, CWE-399, and CWE-119.
IOCs & MITRE ATT&CK
| MITRE ATT&CK | IOC |
|---|---|
|
T1027 – Obfuscated Files or Information T1036 – Masquerading T1054 – Indicator Blocking T1059 – Command and Scripting Interpreter T1076 – Remote Desktop Protocol T1133 – External Remote Services T1189 – Drive-by Compromise T1190 – Exploit Public-Facing Application T1193 – Spearphishing Attachment T1195 – Supply Chain Compromise T1486 – Data Encrypted for Impact T1490 – Inhibit System Recovery |
39e4eb1ab854c4a7929e8e77ca0dbca37049154d ef777a861ede95d3b02b0b135952d43a 246aea5a28ed117238ed0da8e6c96a9a9f1c627613d0f9f57da3e819f57231eb ccfde149220e87e97198c23fb8115d5a |
Global Exposure Analysis
The exposure to CVE-2012-0507 outnumbers the other two CVEs with over 600,000 products with the vulnerability being used around the world.
| CVE-2019-11510 (Pulse Secure Vulnerability) | |
| CVE-2019-19781 (Citrix Vulnerability) | |
| CVE-2012-0507 (SUN & Oracle) | |
The Way Forward
Our research shows that there has been a 17% increase in the number of vulnerabilities associated with ransomware and a 6.5% increase in the number of trending exploits. To date, 260 vulnerabilities have been associated with ransomware.
With ransomware targeting critical sectors and industries, organizations and governments should adopt a risk-based approach to prioritize vulnerabilities based on weaponization and threat associations.
Securin’s in-depth research has helped many organizations become resilient against ransomware. Our recommendation to organizations is to get a Ransomware Assessment to know the gaps, understand the exposure to ransomware, and become resilient.









