On August 24, 2021, Taiwan-based network-attached storage device manufacturer, Synology, reported remote code execution (RCE) and denial of service (DoS) OpenSSL vulnerabilities that impacted its products. This news comes in the wake of eCh0raix ransomware attacks on QNAP NAS devices between April and June 2021 and on Synology devices since 2019.
Initially, it was unclear how many organizations and products would likely be affected by the flaws. However, soon after, tech giants including QNAP, Alpine Linux, Debian, Red Hat, SUSE, and Ubuntu issued security advisories to inform customers about the impact of the two vulnerabilities.
Tracked as CVE-2021-3711 and CVE-2021-3712, the OpenSSL vulnerabilities allow attackers to take over the flow of an application entirely by tricking it into thinking it has succeeded or failed to execute.
Recent Developments
New OpenSSL vulnerability
On March 15, 2022, OpenSSL shipped patches for a high severity Denial of Service vulnerability that affects its software library. Dubbed as CVE-2022-0778 with a CVSS v3 score of 7.5. The flaw affects OpenSSL versions 1.0.2, 1.1.1, and 3.0; was fixed in the released versions of 1.0.2zd (for premium support customers), 1.1.1n, and 3.0.2. Although OpenSSL 1.1.0 is vulnerable, it will not be patched since it is has reached the end of life. While this vulnerability can be definitely weaponized, NSA urges users to patch this vulnerability immediately.
Our Findings
CSW researchers studied the OpenSSL vulnerabilities and their impact. Here is our analysis:
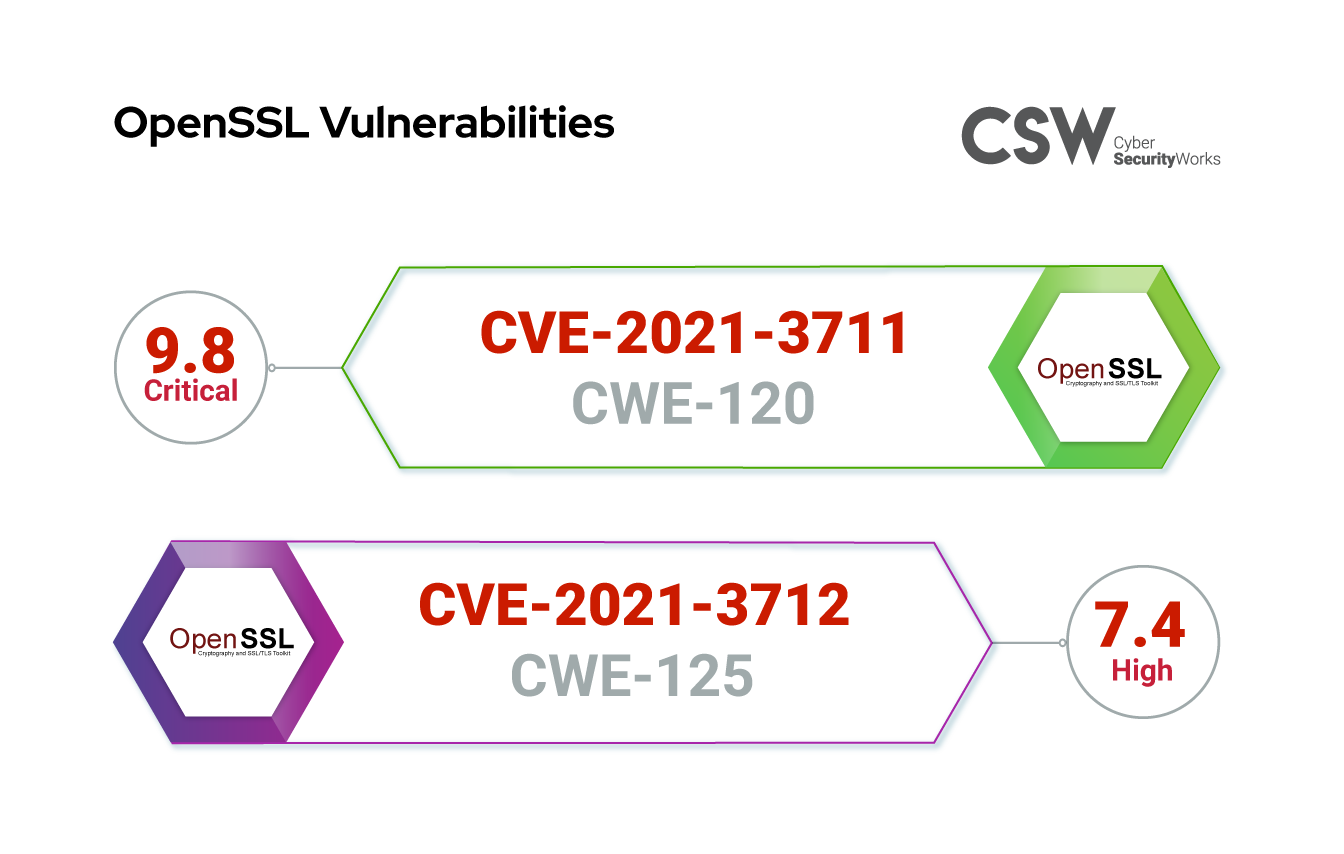
CVE-2021-3711
-
CVE-2021-3711 is a heap-based SM2 buffer overflow vulnerability that leads to crashes and also allows attackers to execute arbitrary code.
-
Categorized under the weakness enumeration, CWE-120 (Buffer Copy without Checking Size of Input (Classic Buffer Overflow)), the critical severity vulnerability has a CVSS v3 score of 9.8.
-
The vulnerability affects OpenSSL versions 1.1.1 and 1.1.1K. The flaw has been fixed in v1.1.1J.
CVE-2021-3712
-
CVE-2021-3712 is a read buffer overrun vulnerability that can be used by attackers to crash vulnerable apps in denial of service (DoS) attacks or gain access to memory contents or sensitive information using private keys.
-
Categorized under the weakness enumeration, CWE-125 (Out-of-bounds Read), the high severity vulnerability has a CVSS v3 score of 7.4.
-
The vulnerability affects OpenSSL versions 1.1.1 and 1.1.1K. The flaw has been fixed in v1.1.1J.
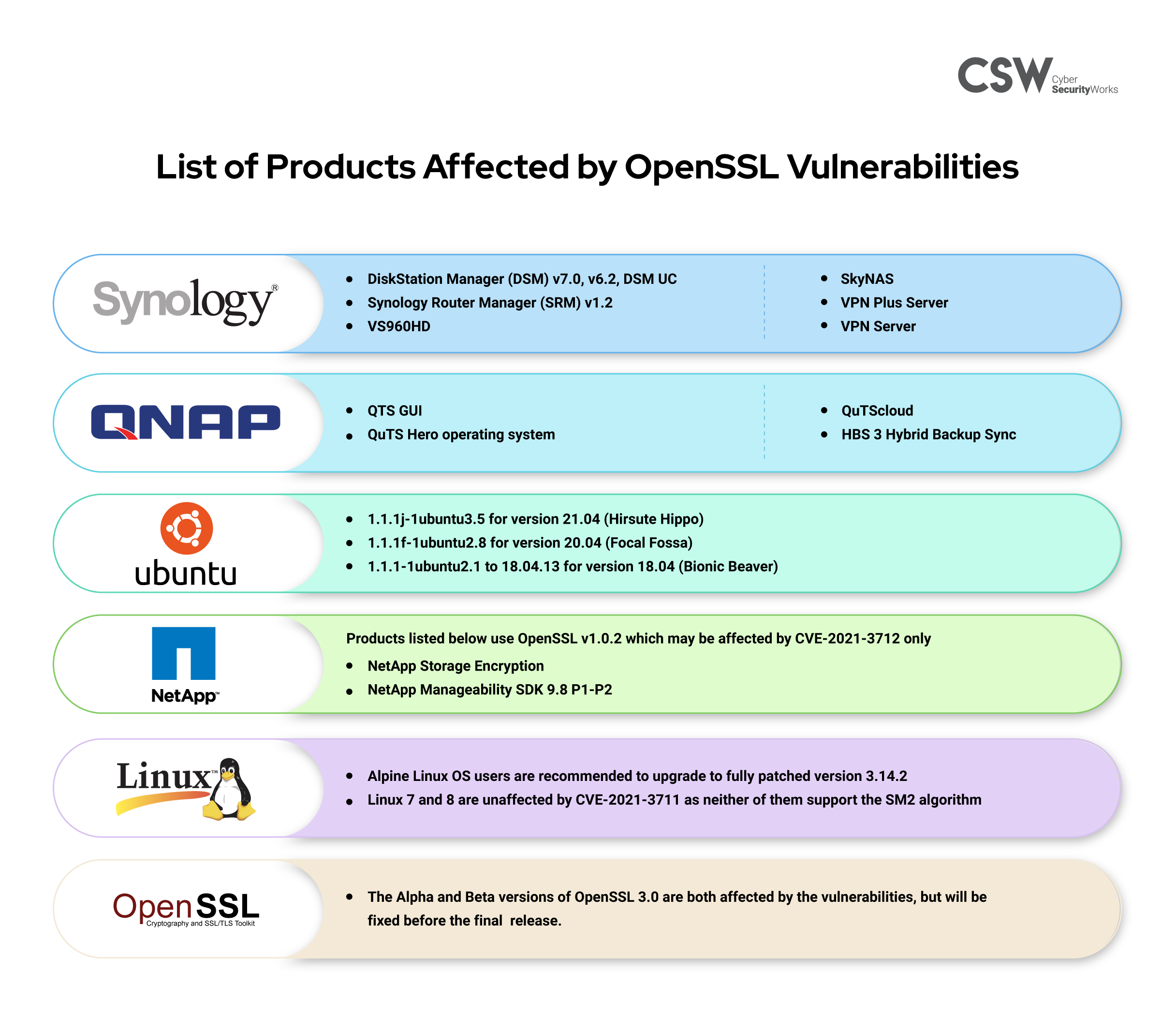
Products and Vendors Affected by the OpenSSL flaws
“If one is looking at NVD alone, which quotes OpenSSL, NetApp, and Debian products only, the real impact of such vulnerabilities is not provided. We should remember that since OpenSSL is a library used by multiple third-party products like Synology and QNAP, we may tend to miss out on reporting the complete list of impacted products.”
~ a CSW expert opinion
NAS device manufacturers, Synology and QNAP, reported that the vulnerabilities were impacting multiple products. Both companies are working on patches for the vulnerabilities. Here is a detailed list of the products affected:
Way Forward
“The impact that ransomware gangs may have by exploiting OpenSSL bugs will be, in most likelihood, huge, since NAS devices are widely used for data backups. Although there are no known exploits in the wild at the moment, we believe that all the chatter on underground forums about these vulnerabilities portends an imminent attack within the next few months.”
~ CSW Analyst’s viewpoint
CSW’s expertise and thought leadership regarding the spate of attacks targeting OpenSSL bugs and what it portends has been quoted recently.
With criminal gangs like eCh0raix ransomware and botnet malware like StealthBot knocking at the doors of NAS device manufacturers and Linux products, it is imperative that companies patch their systems or upgrade to the latest versions in order to prevent any ransomware groups which may leverage the OpenSSL vulnerabilities.
Attackers require one vulnerability to exploit and take advantage of an organization. Organizations, as a result, should adopt a risk-based approach and manage the vulnerabilities in their attack surfaces to boost their security posture.
To know more about CSW’s Vulnerability Management as a Service (VMaaS),
please click here.









