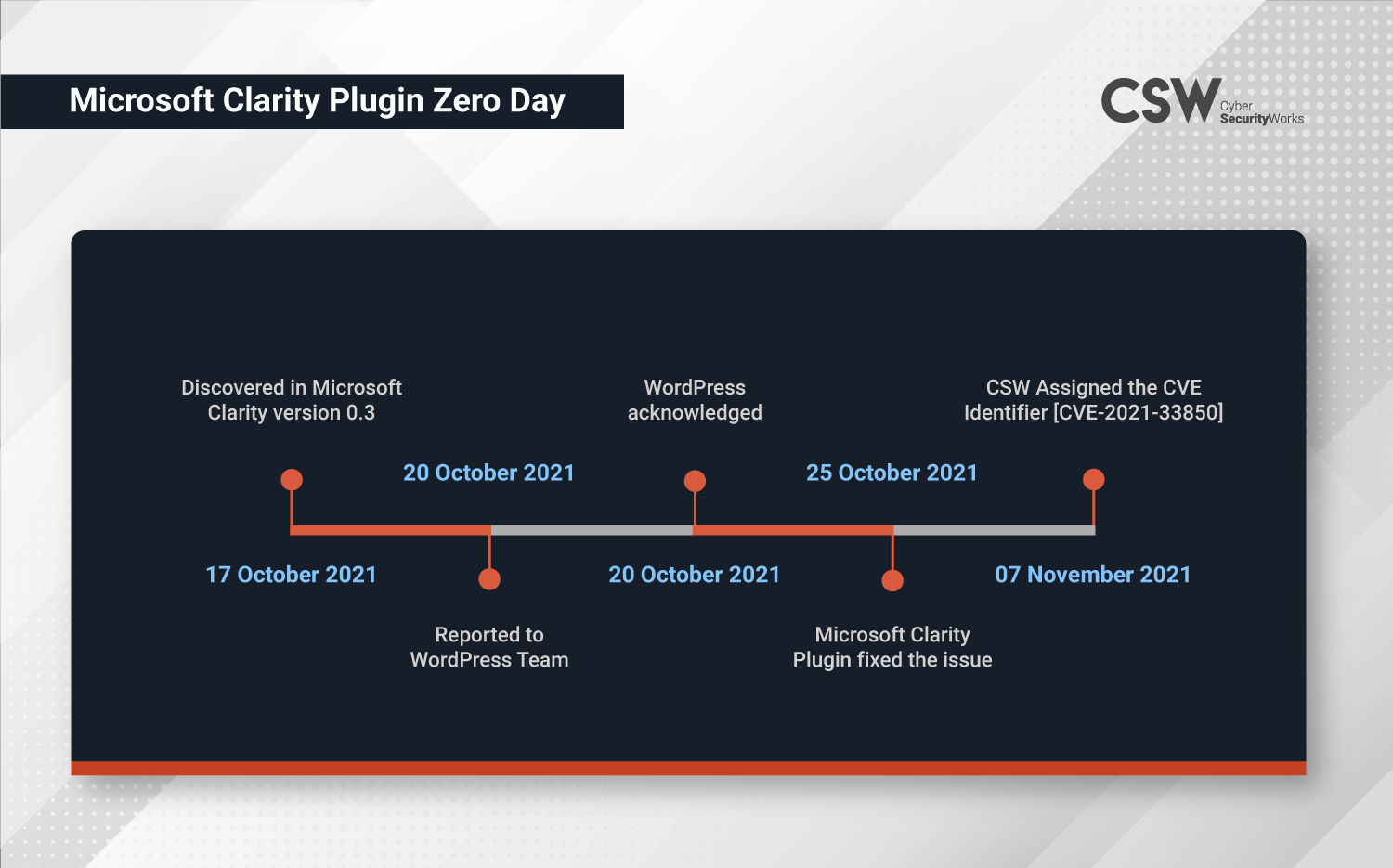
Cyber Security Works has discovered a new zero-day (Cross-Site Scripting) vulnerability, CVE-2021-33850 in WordPress Microsoft Clarity. Microsoft Clarity is an open source analytics tool for websites to track how users interact with your website and the most popular pages. This vulnerability was uncovered by CSW researchers on October 17, 2021.
60% of web applications are susceptible to XSS attacks, which ultimately account for more than 30% of all web application attacks.
This clearly demonstrates why cybersecurity professionals have high concern when it comes to Cross-Site Scripting (XSS) vulnerabilities. Therefore, CSW researchers were able to find one such vulnerability in Microsoft Clarity version 0.3.
Description
The Microsoft Clarity version 0.3 is vulnerable to a Cross-Site Scripting vulnerability which allows arbitrary code to run in a web browser while the browser is connected to a user’s trusted site. An XSS attack is carried out every time a user changes the clarity configuration in Microsoft Clarity version 0.3 stored on the configuring project ID page.
This vulnerability has been categorized with a CWE of CWE-79 leading to Improper Neutralization of Input During Web Page Generation. It is notable that CWE-79 has been listed in OWASP Top 10:2021 under A03:2021 – Injection and holds the second place in 2021 CWE Top 25 Most Dangerous Software Weaknesses.
Vulnerability at a Glance
|
CVE Number |
CVE-2021-33850 |
|
Product Name |
Microsoft Clarity version 0.3 WordPress Plugin |
|
Affected Version |
Version 0.3 |
|
Severity |
High |
|
Vendor |
Microsoft |
|
CWE |
CWE-79 (Improper Neutralization of Input During Web Page Generation) |
|
CVSS Vector |
CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:U/C:N/I:H/A:N |
|
CVSS V3 Score |
4.9 |
Timeline
Proof-of-Concept
The following vulnerability was detected in WordPress Microsoft Clarity Plugin version 0.3.
Issue: Cross-Site Scripting
Severity: Medium
-
Log in to the WordPress application.
-
Install Microsoft Clarity plugin to your WordPress application.
Figure 1: Microsoft Clarity Plugin Installation
-
Click on Settings, and the Clarity Setting page appears.
Figure 2: Microsoft Clarity Settings Page
-
In the Clarity Settings page, enter the payload in the ‘project ID’ section (clarity_project_id parameter).
Figure 3: Entering Encoded XSS Payload in the Project ID section
-
Injected XSS payload gets executed whenever the user changes the clarity configuration page.
Figure 4: Injected XSS Payload Executed and Displays an Alert Box
Impact
An attacker can control a script executed in the victim’s browser and fully compromise the targeted user. In addition, an XSS vulnerability enables attacks that are contained within the application itself. There is no need to find an external way of inducing the victim to make a request containing their exploit. Instead, the attacker places the exploit inside the application itself and simply waits for users to encounter it, thus, resulting in the following—
-
Stealing cookies,
-
End-user files disclosure,
-
Installation of Trojan horse programs,
-
Redirection of the user to some other page or site.
Remediation
-
Perform context-sensitive encoding of untrusted input before it is echoed back to a browser by using the encoding library.
-
Implement input validation for special characters on all the variables reflected in the browser and stored in the database.
-
Implement client-side validation.
Figure 5: Cross-Site Scripting Mitigation Setting in the wp.config File Prevents Cross-site Scripting Attacks
Discovered by
Cyber Security Works Pvt. Ltd.
Vendor Advisory
Security Advisory Published by WordPress
Contribution Credits: Praveen Thiyagarayam, Sathish Kumar, and Arjun Basnet









