The United States Cyber Command and Cybersecurity Infrastructure Security Agency (CISA) rang the warning bells for companies to patch a critical vulnerability (CVE-2021-26084) in the Atlassian Confluence Server and Data Center. Here is our analysis about this vulnerability.
{Updated on October 08, 2021}: Atom Silo, a new ransomware group, is found to be actively exploiting CVE-2021-26084 in the Atlassian Confluence Server and Data Center. According to Sophos researchers, Atom Silo is identical to LockFile, where the malicious dynamic-link libraries are side-loaded in order to disrupt endpoint security software. This instance serves as a perfect warning of the dangers when publicly known security flaws in internet-facing software are left unpatched, even for a short period of time.
{Updated on October 01, 2021}: Researchers at Trend Micro have discovered that Cryptominer z0Miner has been actively exploiting CVE-2021-26084. This leads Atlassian installations on Windows and Linux to create webshells that allow execution of cryptominers on vulnerable systems. In addition, Palo Alto Networks’ have also recognized multiple attacks that managed to upload customers’ password files that downloaded malware-laced scripts and dropped a miner. We urge users to update this critical vulnerability with the latest patches, before you get hit by threats like z0Miner.
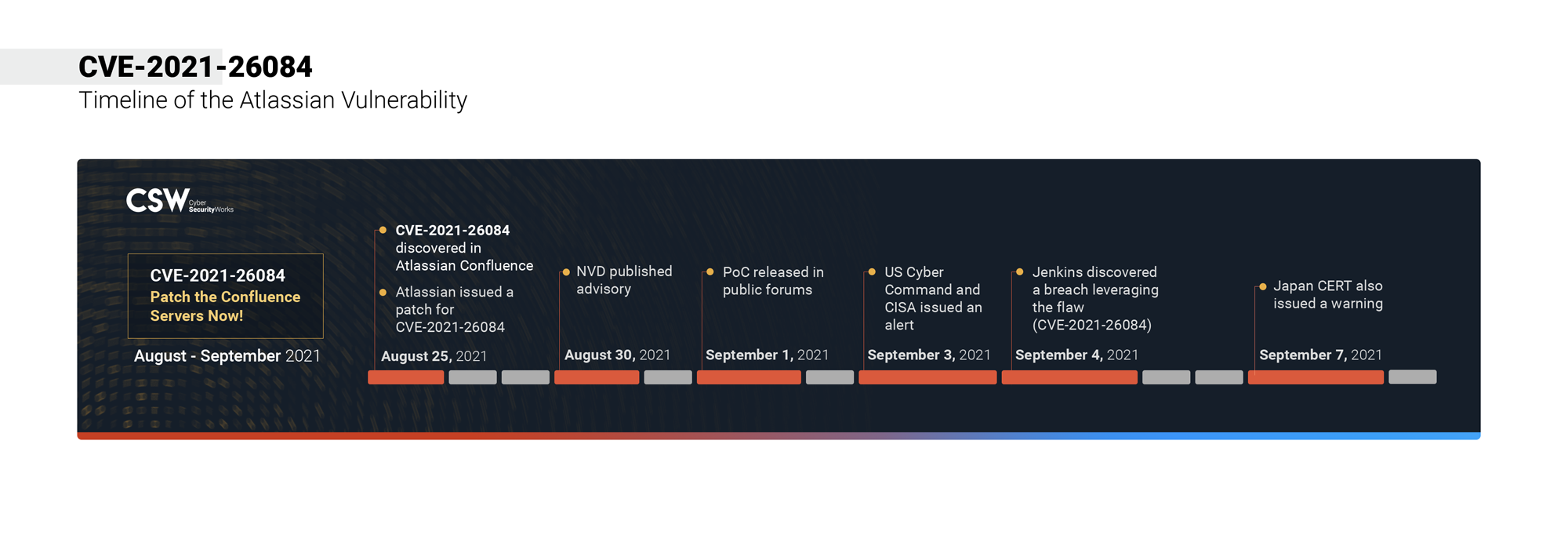
On August 25, 2021, Atlassian published a security advisory for a remote code execution (RCE) vulnerability in its Confluence Server, a popular team collaboration tool used by some of the world’s largest companies. Being a critical vulnerability, CVE-2021-26084 can have a powerful impact, and expecting more attacks in the following days, advisories have been issued by CISA and the United States Cyber Command (USCC).
This critical-rated Object-Graph Navigation Language (OGNL) injection vulnerability can allow an authenticated user, and in some instances, unauthenticated users, to execute arbitrary code on a Confluence Server Webwork or Data Center instance.
Widespread Availability of PoCs Worsening the Situation
With the extensive availability of RCE exploits, hackers are aggressively looking for and exploiting vulnerable Confluence servers to install cryptominers, further worsening the situation.
“According to a pentester perspective, this exploit is simple to implement and will execute a command on the targeted server, if successful. In the wild, attempts to hack servers running vulnerable software versions were also discovered.”
On September 4, 2021, Jenkins, a global open-source automation system, revealed that they had suffered a security breach in their internal servers. Soon after discovering the successful server hack, the Jenkins team was prompted to shutdown the Confluence server, which had remained unused since 2019. The developers of Jenkins have discovered that the Confluence (CVE-2021-26084) exploit was used to install a Monero miner in the container running the service.
With the PoC going public and threat actors jumping at the opportunity to actively exploit the vulnerability, Atlassian issued an advisory to its customers to upgrade to the latest long-term support release or run their script on Windows and Linux Operating Systems to mitigate the issue.
Reasons for the High-Impact
-
CVE-2021-26084 is a nasty vulnerability that could allow an unauthenticated attacker to execute commands on a susceptible server remotely.
-
The flaw carries a CVSS v3 score of 9.8 (critical) out of 10.
-
According to National Vulnerability Database (NVD), the vulnerability is classified under weakness CWE-74, which leads to the Improper Neutralization of Special Elements in Output Used by a Downstream Component (‘Injection’).
-
Atlassian asserts that Confluence is utilized by over 60,000 clients, including Audi, Hubspot, NASA, LinkedIn, Twilio, and Docker, on its website.
Vulnerable Products
Atlassian Confluence is a web-based team collaboration tool for managing workspaces and projects operated locally on a company’s server. Atlassian Data Center is a more feature-rich version of Confluence that includes team calendars, analytics, complex rights management, content delivery network integration, and more.
The vulnerability is seen in multiple software versions of the Confluence Server and Data Center. Here is a list of affected versions:
-
version < 6.13.23
-
6.14.0 ≤ version < 7.4.11
-
7.5.0 ≤ version < 7.11.5
-
7.12.0 ≤ version < 7.12.5
After addressing the issue, Atlassian published updated versions of each of the impacted products, as well as solutions.
Global Exposure
According to the Shodan search engine, there are 9,203 potential products that are accessible to the Internet, with around 21% of occurrences in Germany, followed closely by the United States and China with 20% and 18% instances.
Fortunately, popular scanners such as Nessus, Qualys, and Nexpose were able to detect this issue and are tagged with the following plugin ID.
| Nessus | Qualys | Nexpose |
| 152864 | 730172 | atlassian-confluence-cve-2021-26084 |
Timeline
Fix this Issue with a Patch
The successful discovery of data breaches and flaws requires a strong cybersecurity program and continuous scanning for signs of attack. However, monitoring zero-day attacks and determining if organizational systems were hacked prior to patching are complex tasks for any security team. It is always essential to pay attention to new flaws and do one’s best to patch them as quickly as possible.
We therefore recommend Atlassian users to upgrade immediately to versions 6.13.23, 7.4.11, 7.11.6, 7.12.5, 7.13.0, in order to limit the exposure of their attack surfaces.
Schedule a risk-free consultation to stay inside the security safety net.









