{Updated September 2021}: On September 8, 2021, a new Russian-speaking threat actor was identified actively exploiting the Fortinet VPN vulnerability, CVE-2018-13379. The threat actor called Orange is the administrator of the new RAMP hacking forum and was previously the operator of the Babuk Ransomware operation. They stole data from unpatched servers and put them up on a Groove Ransomware site. The perpetrator’s breach list reportedly contains the login credentials to multiple top organizations in 74 countries, including India, France, Israel, Italy, Taiwan, and the USA.
CVE-2018-13379 has been one of the most widely exploited vulnerabilities of 2020 and was called out by CSW researchers in the Ransomware Q2 report 2021.
We urge our readers and clients to patch their Fortinet VPN servers without further delay to stave off a major ransomware attack.
{Updated on August 18, 2021}: On 17 August 2021, researchers intimated Fortinet after discovering a zero-day command injection vulnerability, a variant of CVE-2021-22123, in the FortiWeb Web Application Firewall (WAF).
This high severity vulnerability, which still does not have a CVE number, is likely to be classified under the weakness enumeration CWE-78 (Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) with a CVSS v3 score of 8.8. The zero-day flaw allows authenticated attackers to execute arbitrary commands with root privileges on an underlying system via a SAML server configuration page.
The vulnerability can also be chained with another authentication bypass flaw, CVE-2020-29015, giving an attacker full control of all vulnerable servers.
The zero-day vulnerability impacts FortiWeb versions 6.3.11 and prior. A patch for the vulnerability is expected to be released with the version 6.4.1 upgrade coming up at the end August.
We urge organizations to keep themselves up-to-date about the latest patches and security upgrades to avoid any untoward events.
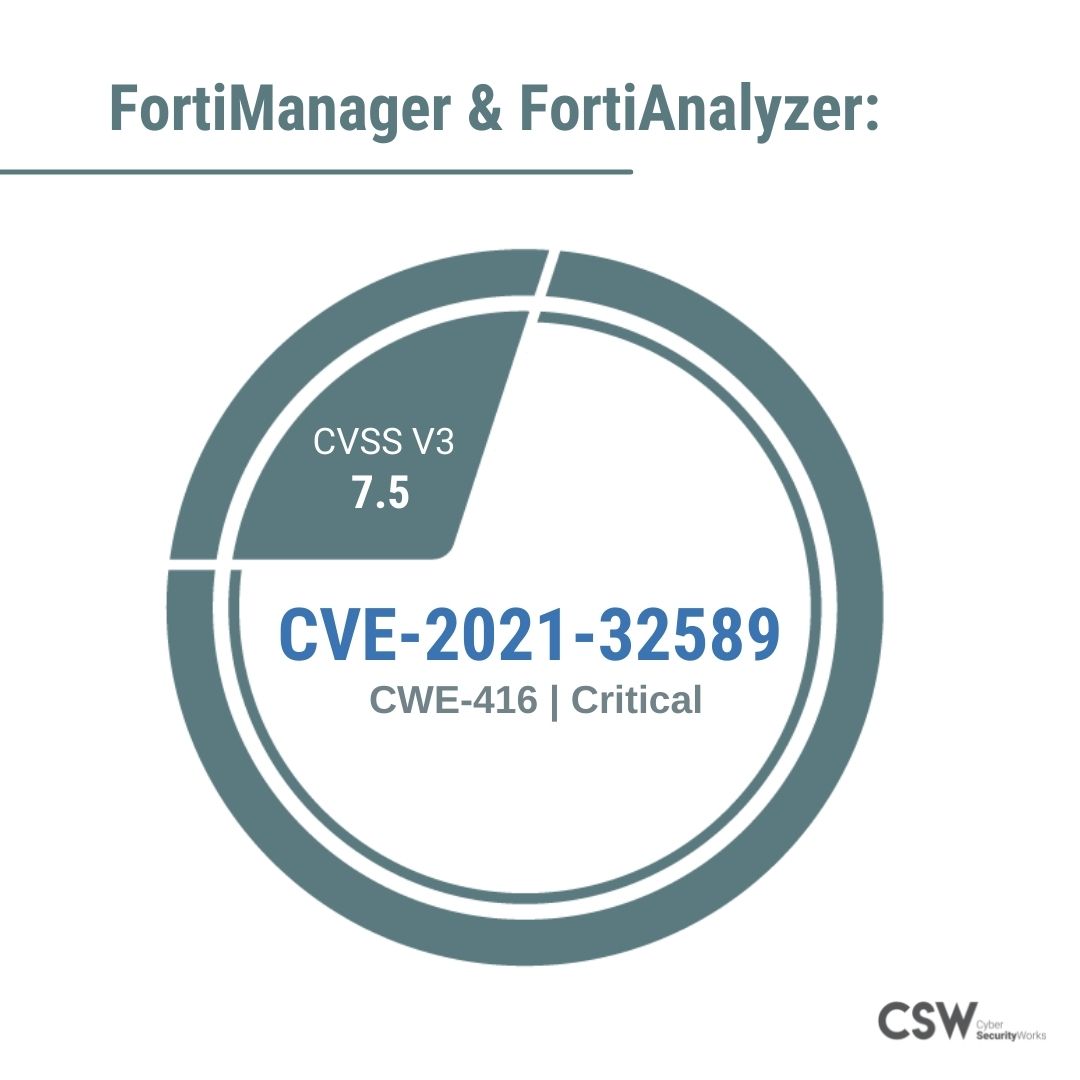
In a latest update on 19 July 2021, Fortinet released an advisory to all its clients, sharing patch details and workarounds for a Use-After-Free vulnerability, classified under CWE-416, in FortiManager and FortiAnalyzer. Our research analyzed the vulnerability may lead to remote code execution after unauthorized access to root. Our analysis of the vulnerability is detailed below.
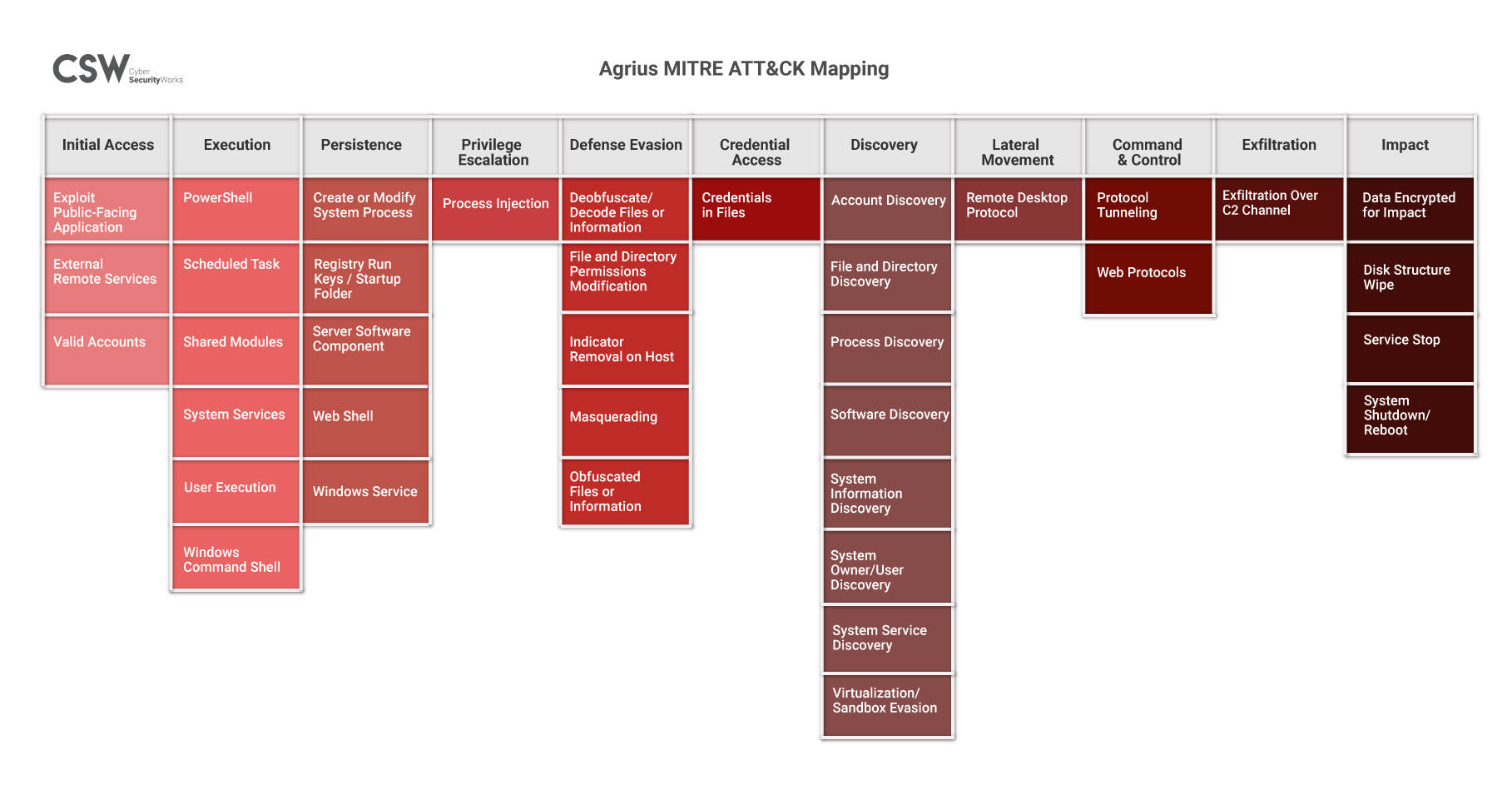
Three Virtual Private Network (VPN) vulnerabilities in FortiOS that have existed for over a year now have recently been exploited in an attack against a local US municipal government. The newly discovered threat group, Agrius, has been observed using a relatively new ransomware called Apostle to exploit these vulnerabilities.
CSW warned of the Fortinet VPN vulnerabilities
The possibility of a VPN vulnerability being exploited was called out by CyberSecurityWorks one year ago in a report published in July 2020, enumerating three possible vulnerabilities, which were already weaponized.
Further, in an article published in December 2020, titled ‘Fortinet’s 50,000 VPN Leak Highlights Lack of Cyber Hygiene’, our analysis pointed out a critical vulnerability, CVE-2018-13379, in the restricted directory titled ‘Path Traversal’ in Fortinet VPN versions 5.4.6 to 6.0.4, putting close to 50,000 IP addresses at risk.
Fortinet Vulnerabilities
FortiManager & FortiAnalyzer:
CVE-2021-32589
-
CVE-2021-32589 is a severe vulnerability with a CVSS v3 score of 7.5.
-
The CVE is categorized under CWE-416 (Use After Free) which is also listed in the 2021 CWE Top 10 Most Dangerous Software Weaknesses by MITRE.
-
A CISA advisory was also issued, urging organizations to patch this vulnerability on priority.
-
The vulnerability affects FortiManager and FortiAnalyzer versions 5.6.10, 6.0.10, 6.2.7, 6.4.5, 7.0.0 and 5.4.x and below.
-
Fortinet urges their customers to upgrade their versions of FortiManager and FortiAnalyzer as well as upgrade their FortiGate IPS definitions to v18.001 or above.
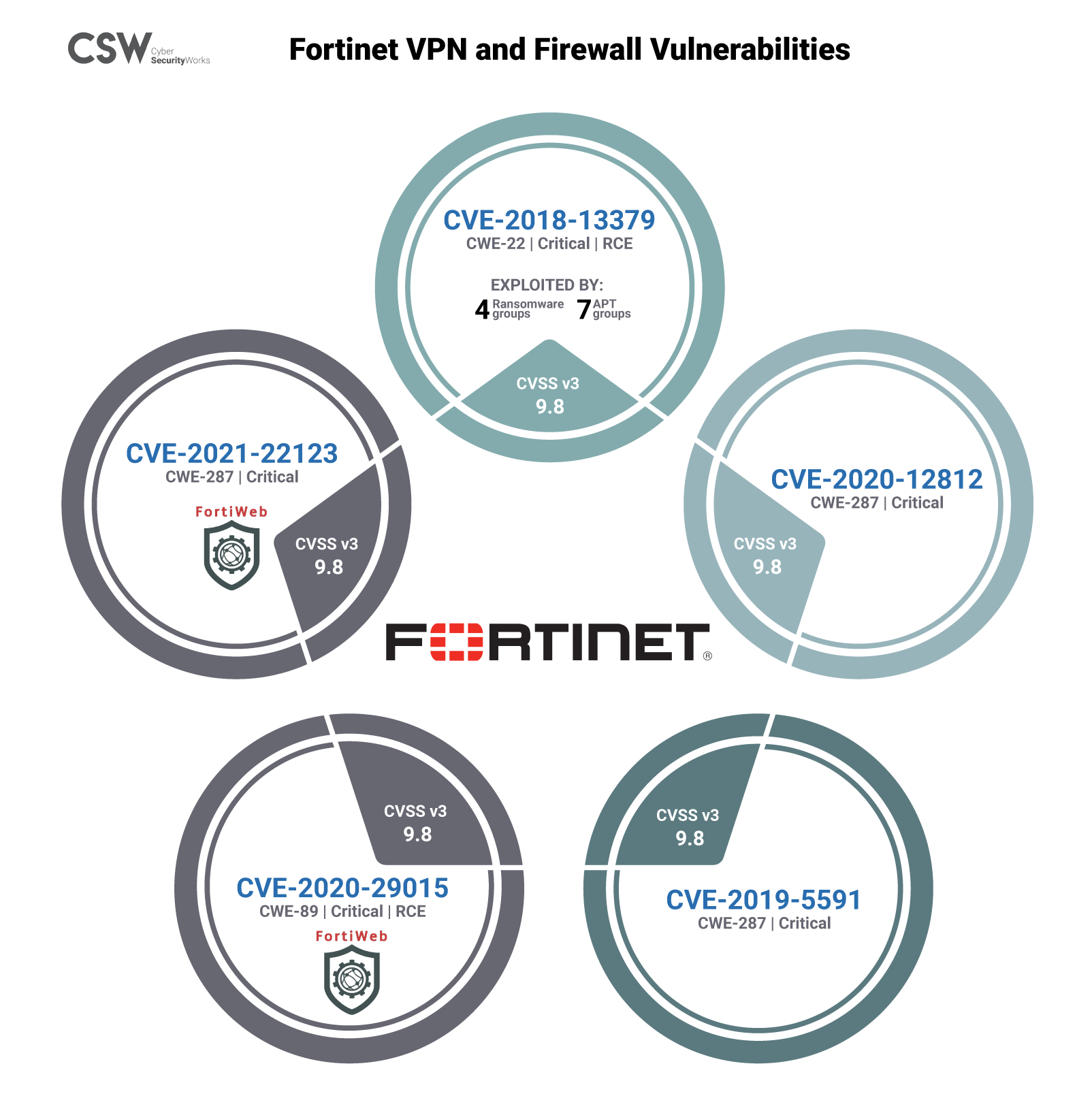
In the US municipal network attack, the threat actors accessed a web server hosting via a Fortigate vulnerability and created a username on a local network to allow for persistence attacks. Our research analyzed the vulnerabilities in Fortinet that could be potentially exploited to mount an attack. Here is our analysis of the vulnerabilities—
FortiGate SSL VPN:
CVE-2018-13379
-
CVE-2018-13379 is a pre-authorization arbitrary file reading vulnerability, according to the alert issued by the NSA.
-
Classified under the weakness enumeration CWE-22 (improper limitation in the path name to a restricted ‘Path Traversal’ directory), this critical vulnerability has a severity rating of 9.8 on the CVSS v3 score.
-
This CVE has been exploited by 7 Advanced Persistent Threat (APT) groups and has a Remote Code Execution (RCE) capability.
-
It allows an attacker on the same network to send malicious service location protocol (SLP) requests to take control of it.
-
Our research indicates that this vulnerability is trending in hacker channels and the dark web.
-
This CVE has also been associated with several ransomware attacks in the past, namely, Apostle (November 2020), Cring (January 2021), Pay2Key (2020) and Conti (December 2019).
CVE-2020-12812
-
CVE-2020-12812, leads to an improper authentication exploit (CWE-287) in the FortiOS system.
-
The FBI and CISA have issued alerts urging organizations to patch this vulnerability on priority.
-
Classified under CWE-287 (Improper Authentication), this critical vulnerability has a severity rating of 9.8 in CVSS v3 score.
CVE-2019-5591
-
CVE-2019-5591 is a medium severity vulnerability with a score of 6.5 from CVSS v3.
-
Categorized under CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor) the medium severity rating of this vulnerability allows it to fly past the radar of security teams.
-
This vulnerability is trending in the wild, therefore organizations need to patch it immediately.
Two high-severity vulnerabilities known to have remote access capabilities were also identified in the FortiWeb Firewall.
FortiWeb Firewall:
CVE-2021-22123
-
CVE-2021-22123 is a high severity vulnerability with a CvSS v3 score of 8.8.
-
The CVE is categorized under CWE-78 (Improper Neutralization of Special Elements used in an OS Command), which is also listed in the 2020 CWE Top 25 Most Dangerous Software Weaknesses by MITRE.
CVE-2020-29015
-
CVE-2020-29015 is a critical severity vulnerability with a CvSS v3 score of 9.8.
-
Categorized under CWE-89 (Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’)), the critical vulnerability is also part of the 2020 CWE Top 25 Most Dangerous Software Weaknesses by MITRE.
It is noted that the CVE-2021-22123 can have a more serious impact if chained with a misconfiguration and a separate vulnerability, CVE-2020-29015. When these two vulnerabilities are combined, threat actors can gain complete remote access to the internal network, bypassing the FortiWeb Firewall.
New APT group Agrius exploiting CVE-2018-13379
On 28 May 2021, a new Iranian APT hacking group, Agrius, exploited an unpatched vulnerability in the Fortinet VPN. Our research shows that Agrius group is targeting multiple sectors—Technology/IT, Banking/Financial/Wealth Management, Outsourcing & Hosting, Transportation & Shipping, Energy/Oil & Gas, Process Manufacturing, Discrete Manufacturing, and Industrial Insurance. Our recommendation to organizations would be to patch all these vulnerabilities on priority.
Table: Fortinet VPN Patches
Agrius Attack Methodology
The Agrius group uses a new ransomware, titled Apostle, in their exploits. The group encrypts files for ransom but eventually wipes the files clean using a strain of the dangerous Deadwood (also called Detbosit) destructive wiper malware.
The Joint Cybersecurity Advisory report identified the threat actors scanning Fortinet ports 4443, 8443 and 10443 to exploit any critical vulnerabilities in them. It is suspected that the APT group then conducts distributed denial-of-service (DDoS) attacks, ransomware attacks, structured query language (SQL) injection attacks, spear-phishing campaigns, website defacements, and disinformation campaigns.
Agrius MITRE ATT&CK Mapping
| IoCs for Agrius Group |
|
IOCs (SHA 256): 6FB07A9855EDC862E59145AED973DE9D459A6F45F17A8E779B95D4C55502DCCE E37BFAD12D44A247AC99FDF30F5AC40A0448A097E36F3DBBA532688B5678AD13 3E9C6F384B63EBEAA729B7C97A179D409CDD859315EE2F6372A2A550E567445F B30405D654C1BFCD5E2BD338CC16E971738CEB6BA069DA413195358B9CA3A2A2 6505ECD35E45E521F5E37FEBD01BE04166D725BA87552777C17517533AFC6329 FC949BD5AA0E704901F12624BADD591768EA5613560BD3D88C396479235DA095 96CC69242A7900810C4D2E9F3F55AAD8EDB89137959F4C370F80A6E574DDC201 40F329D0AABA0D55FC657802761C78BE74E19A553DE6FD2DF592BCCF3119EC16 7B525FE7117FFD8DF01588EFB874C1B87E4AD2CD7D1E1CEECB5BAF2E9C052A52 19DBED996B1A814658BEF433BAD62B03E5C59C2BF2351B793D1A5D4A5216D27E 5EB5922B467474DCCC7AB8780E32697F5AFD59E8108B0CDAFEFB627B02BBD9BA 18C92F23B646EB85D67A890296000212091F930B1FE9E92033F123BE3581A90F E889D4B2CFB48B6E8F972846538DFBC057DBFC35FA28F0515CAD4D60780A9872 4A50073F841A1BEAA5900241FCE76ED242659130E065DBD38BE318A650B1264A B5149C1AAE5C899A0F3A4BE162E24C08D284F67F6B9FB70439CE6D91353A540C DF94D32997E22BAE2E5745EB3120947B025F79A16CF4B710131F911B12D960CC 85F16DF007FC848731ED02E0C3D8DD3AB1F2F2BF8C1B6999F7D9FF98A1CAC1C7 F18DD50DDE8C1101EB3C892FC2BF04B7779C2C0DEF27DE1D6C1FD341F3ECDF6C 5F5EDAE2CAE4DB0EE988962CA2E7CCCD1892E4F4B512FBB780210595C7BA7088 BAC77143CB8829C802A6723A397277AA34BA2738103D78517B36C6CFB06724EF E4EA1728E19699612B5614CC0B8829A4BF749870648BE6EFC1B8A88C036F3607 CCFC0A2652916543E0CE972B38BA50815E8DF11387502519607C9FD4F91D635F |
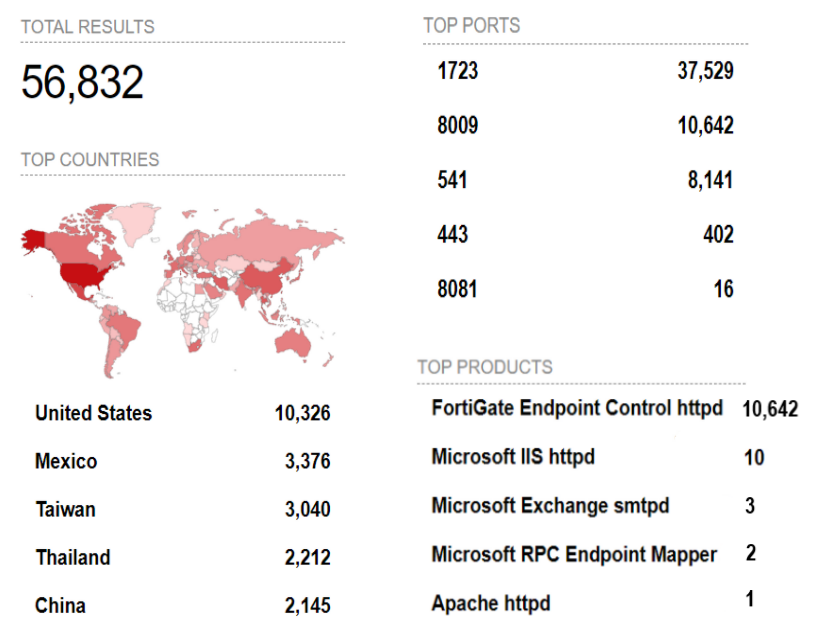
Fortinet Exposure Analysis
Our exposure analysis using Shodan indicates that there are several thousand networks that are vulnerable to these attacks if they are not patched immediately. The other ports at risk apart from the ones mentioned in the Joint Cybersecurity Advisory report are listed below.
How can we mitigate the threat?
On April 2, 2021, CISA and FBI published a joint warning to warn government, commercial and technology services enterprises about this vulnerability. On May 31, 2021, FBI published a second alert about hackers leveraging the FortiGate SSL VPN vulnerabilities.
Despite the repeated warnings and seven notifications over a span of 18 months, the vulnerability still remains unpatched in many cases. A Fortinet PSIRT Advisory mentions that the IP addresses to unpatched devices are being sold on the dark web, jeopardizing several thousands of users to a cyber attack. An upgrade from FortiOS 5.4 or 6.0 to the latest version (FortiOS 5.4.13, 5.6.8, 6.0.5 or 6.2.0 and above) will mitigate the threat.
Attackers need only one vulnerability to exploit and take down an organization. Organizations, therefore, need to adopt a risk-based approach and manage the vulnerabilities in their attack surfaces to boost their security posture.
To know more about CSW’s Vulnerability Management as a Service (VMaaS), please visit https://cybersecurityworks.com/services/vulnerability-management-as-a-service.









