More than 3.2 million Hikvision security camera systems remain vulnerable to a critical vulnerability, CVE-2021-36260, which allows hackers to take control of devices remotely, without any user interaction.
The video surveillance giant Hikvision disclosed a zero-click vulnerability tracked as CVE-2021-36260, which has existed from at least 2016, according to researchers. The vulnerability that exists in Hikvision camera models is highly susceptible to remote hijacking without requiring a username or password.
This critical vulnerability carries a CVSS v3 score of 9.8 and allows hackers to bypass the protected shell, limiting the use of the system by their owners to a specific scope of commands. Therefore, Securin experts urge users to address this severe vulnerability on high priority before malicious actors launch attacks against organizations.
Recent Updates:
{Updated on Aug 23, 2022}: Despite a patch being made available in September 2021, CVE-2021-36260 has been trending heavily since October 2021. With the exploit codes being available in public domain, CISA considered this vulnerability dangerous and added it to the KEV catalog in January 2022. According to a latest report, over 80,000 instances of Hikvision cameras with the vulnerability are ripe for exploitation even today prompting us to ask the following question –
Why are enterprises not prioritizing this dangerous vulnerability?
“Hackers can exploit the Hikvision vulnerability to gain complete control over camera footage. Further, they can obtain credentials of users of the compromised cameras and use them to penetrate deeper into connected networks.”
Pentester’s Perspective
{Updated on Dec 10, 2021}: A Mirai-based botnet known as ‘Moobot’ is growing rapidly by exploiting a serious command injection issue in web servers of several Hikvision devices. According to Fortinet, ‘Moobot’ is using CVE-2021-36260 to infect unpatched devices and steal sensitive data from victims.
We recommend users to fix this serious vulnerability before criminal threat actors initiate attacks against organizations.
CVE Findings
CVE-2021-36260
-
CVE-2021-36260 is a remotely exploitable command injection vulnerability in some Internet of Things (IoT) cameras produced by Chinese Hikvision that use a web server service.
-
Researchers pointed out that the attacker just requires access to the http(s) server port (usually 80 and 443), making it simple to exploit the flaw.
A Critical Vulnerability, Why?
-
CISA issued an alert that urges users to patch this critical vulnerability.
-
Classified under the weakness enumeration, CWE-20 (Improper Input Validation), with a CVSS v3 score of 9.8.
-
CWE-20 holds third place in MITRE’s 2021 CWE Top 25 Most Dangerous Software Weaknesses.
-
Hikvision published several screenshots of the Proof of Concept from an attacker’s perspective.
“CWE -20 could affect the control flow or data flow of a program. When software fails to properly validate input, an attacker can design it in a way which is not intended by the rest of the application.”
This is a reminder of how important it is to patch security vulnerabilities, and to make sure the network is protected with an up-to-date security stack.
Data of Interest
-
Interestingly, 40% of the global surveillance camera market is owned by Hikvision, which includes a huge affected list.
-
The company provides surveillance products to the global market via more than 2,400 partners in 155 countries and regions.
-
Most concerning is that none of the popular scanners such as Qualys, Nessus and Nexpose were not able to detect this vulnerability that put unpatched cameras at danger.
Affected Products
The following is the list of affected products that are at risk.
Global Exposure
The Shodan analysis clearly demonstrates that a number of old firmware still remain vulnerable and are accessible on the Internet.
-
CVE-2021-36260 has around 3.2 million installations, with the majority of them in the United States and Vietnam.
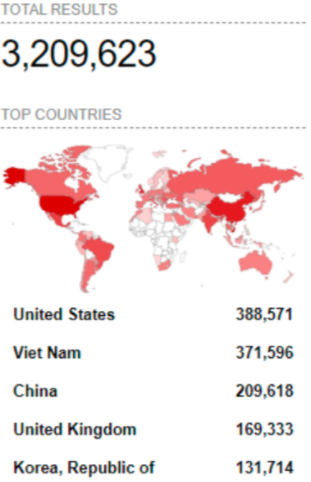
-
It’s not surprising that the list of affected is so long; 1.7 million instances of port 80 are prone to be exploited by attackers.
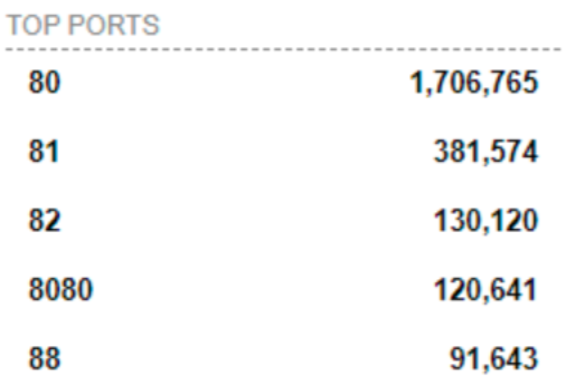
-
This vulnerability is found trending in China, based on Google search results. Could this be an indication that threat actors in China are exploiting this vulnerability or users remediating it?
Stave off an attack. Patch Immediately.
Hikvision described this vulnerability as “a highly critical vulnerability” because an attacker can completely take over an internet-connected camera, and potentially other internal networks, thereby posing a high risk to security management.
On September 18, 2021, Hikvision Security Response Center provided a patch to all vulnerable firmware. In addition to live testing, the code has been decrypted, reversed and confirmed if the deployed patch fixes the issue. Therefore, we recommend organizational security management teams to patch this vulnerability and remain ahead of ever-hungry attackers.
Securin can help organizations stay ahead of threats and prevent falling victim to attacks. Connect with us to know how.









