On June 8, 2022, the CISA, the FBI, and the NSA have issued a joint advisory to warn organizations about Chinese cyber-espionage attacks. The advisory reveals a list of 16 CVEs exploited by Chinese threat actors. It also stated that the attacks are primarily aimed at telecommunications companies and are conducted by exploiting vulnerabilities. It has also suggested that organizations should take additional mitigation steps to remove such attacks in the initial stage.
The National Security Agency listed 25 vulnerabilities that are being targeted by Chinese state sponsored cyber attackers popularly known as APT41. Know more about these vulnerabilities and patch them before you fall prey to a breach.
We examined 25 vulnerabilities listed in the security advisory and analyzed them for interesting correlations.
Here are our findings –
- 12 CVEs with RCE capabilities
- 3 CVEs with Privilege Execution
- 6 CVEs are associated with APT Groups
- 1 CVE is associated with Lazarus Malware
- 4 CVEs are associated with Ransomware
- 2 CVE’s were called out in our Cyber Risk Series
.png)
Among these 25 weaponized, 21 CVEs rank under Top 25 Common Weakness Enumeration (CWE) making them easy to exploit and the rest four CVEs are ranking under Top 30.
.png)
Out of 25 vulnerabilities, 18 CVEs have known exploits. Given below are the details.
Table 1: Known Exploits
Our threat researchers analyzed the constant cybercriminal activity related to exploit kits and found two CVEs CVE-2019-19781 and CVE-2019-11510 associated with four exploit kits. We also noticed that older exploit kits such as the RIG exploit kit, Fallout exploits kit are getting upgraded with the newer elements and capabilities.
| CVE Number | Exploit Kits |
| CVE-2019-19781 | RIG exploit kit, Fallout exploit kit |
| CVE-2019-11510 | Fallout, Spelvo |
CVE’s Associated with Ransomware
We also found that four CVEs out of 25 are associated with 21 Ransomware families. Interestingly, these old vulnerabilities range from the year 2019.
| S.No | CVE Number | Ransomware |
| 1 | CVE-2019-19781 | CLOP NOTROBIN Ragnarok Sodinokibi Vatet loader REVIL Golang RansomwareMEGA CORTEX SNAKE DoppelPaymer Bitpaymer Dridex 2.0 Neifilm Nemty |
| 2 | CVE-2019-11510 | Black Kingdom Sodinokibi Maze |
| 3 | CVE-2019-3396 | GandCrab Lockergoga Mega cortex |
| 4 | CVE-2019-18935 | Netwalker |
Table 2: Associated Ransomware
We called out vulnerabilities CVE-2019-19781 and CVE-2019-11510 associated with REvil and Sodinokibi Ransomware in Cyber Risk in Remote Desktop and Cyber Risk in VPN. We red flagged these vulnerabilities as potential gateways for ransomware attacks and we have been proved right.
CWE Analysis of 25 Vulnerabilities
We also analyzed CWE ids and found that CWE-502 was highly targeted by the threat actors followed by CWE-22. CWE-502 categorizes vulnerabilities where the application deserializes untrusted data without verifying the resulting data as valid.
CWE-22 categorizes weaknesses that result in improper limitation of a pathname resulting in a location outside the restricted directory. Both these CWEs find a place in the Top 25 dangerous programming errors.
| CWE ID | Count | CWE Ranking |
| CWE-22 | 3 | Top 25 |
| CWE-94 | 1 | Top 25 |
| CWE-20 | 2 | Top 25 |
| CWE-502 | 4 | Top 25 |
| CWE-862 | 2 | Top 25 |
| CWE-119 | 2 | Top 25 |
| CWE-269 | 1 | Top 25 |
| CWE-77 | 1 | 31 |
| CWE-295 | 1 | 28 |
| CWE-416 | 1 | Top 25 |
| CWE-134 | 1 | NA |
| CWE-74 | 1 | Top 25 |
Table 3: CWE Ranking
Vendors Analysis
Notably, Microsoft tops the most affected vendor list exploited by the Chinese hackers. It is followed by Citrix in the second place.
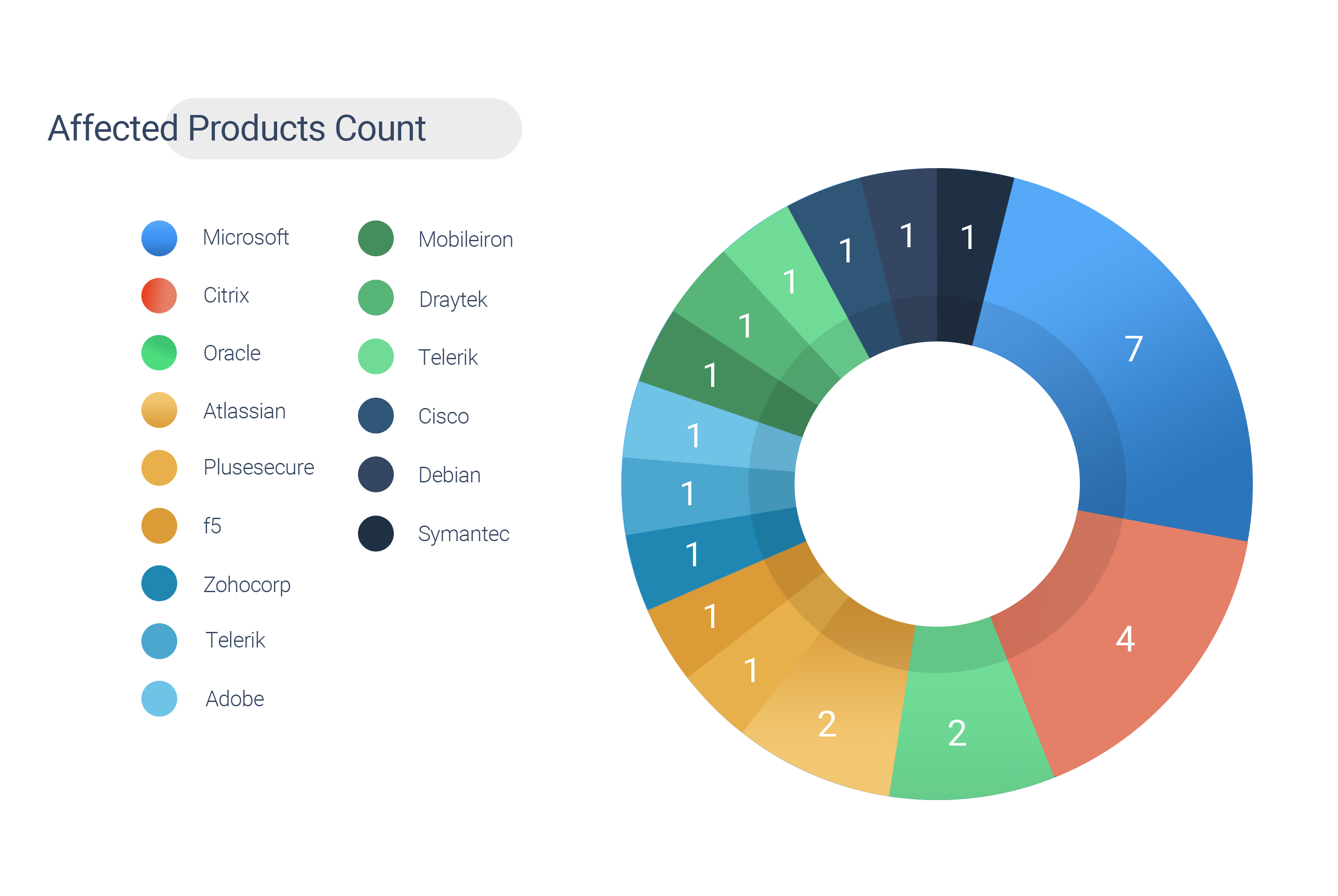
| Vendor | Count |
| Microsoft | 7 |
| Citrix | 4 |
| Oracle | 2 |
| Atlassian | 2 |
| Pulse Secure | 1 |
| F5 | 1 |
| Zohocorp | 1 |
| Telerik | 1 |
| Adobe | 1 |
| Mobileiron | 1 |
| Draytek | 1 |
| Cisco | 1 |
| Debian | 1 |
| Symantec | 1 |
Table 4: Affected Vendors
Most targeted Vulnerability by Threat Actors
Over half of the vulnerabilities are RCE – the most targeted bug. The attacker executes the code remotely by running malware and gains full access to data, and also carries out a full distributed denial of service.
.png)
These products need to be prioritized for immediate patching. The following CVEs have low severity rating CVE-2020-8193, CVE-2020-8195, CVE-2020-8196, and CVE-2019-1040 with a CVSS Score of below 5.0. Their severity scores make them low priority for security teams which is why these vulnerabilities are routinely weaponized and targeted by malicious groups.
Patches are available for all 25 vulnerabilities. We urge you to patch these immediately and secure your environment.
25 Vulnerabilities & Patches
Table 5: Patches for Exploited Vulnerabilities









