An APT group is using CVE-2021-44077 and CVE-2021-44515 in Zoho ManageEngine ServiceDesk Plus and Desktop Central Servers to compromise businesses in a range of industries, including military and technology.
– Cyber Infrastructure Security Agency and FBI
{Updated on January 25, 2022}: Zoho fixed a new critical severity vulnerability (CVE-2021-44757) that affects the company’s unified endpoint management (UEM) solutions Desktop Central and Desktop Central MSP. Approximately 2,800 ManageEngine Desktop Central instances are exposed to the Internet. With a series of CISA alerts stating that APT groups are targeting ManageEngine, we recommend users to patch this vulnerability immediately.
On November 22, 2021, Zoho released an advisory alerting customers about the active exploitation of newly registered CVE-2021-44077 in ManageEngine ServiceDesk Plus. Zoho’s ManageEngine ServiceDesk Plus is an IT help desk and asset management software that provides a complete auditing trail of the service tickets associated with each asset.
APT Threat Groups Actively Seeking for Vulnerable ServiceDesk Systems
Over the three months since the disclosure of CVE-2021-40539, the threat actors have shifted their focus to a different Zoho product by leveraging the new vulnerability (CVE-2021-44077). Threat actors have been observed exploiting the CVE-2021-44077 unauthenticated, remote code execution issue affecting Zoho ServiceDesk Plus versions 11305 and older.
On September 16, 2021, the Federal Bureau of Investigation (FBI), the United States Coast Guard Cyber Command (CGCYBER), and the Cybersecurity and Infrastructure Security Agency (CISA) first alerted the public about activity targeting CVE-2021-40539, stating that it was most likely APT activity and emphasizing the high risk these attacks posed to critical infrastructure. Following the joint alerts, Palo Alto Networks has published that they found traces of attacks linked to the Chinese APT27 (Emissary Panda) group, which has previously used Godzilla webshell.
On December 17, FBI and CISA red-flagged another CVE identified as CVE-2021-44515 in Desktop Central servers that have been under active exploitation by Advanced Persistent Threats.
To add on, following the exploitation, attackers are downloading a dropper to target systems. This dropper delivers a Godzilla webshell, which allows the actor with additional access to and persistence on compromised devices, similar to prior techniques used against the ADSelfService software.
The Looming Threats
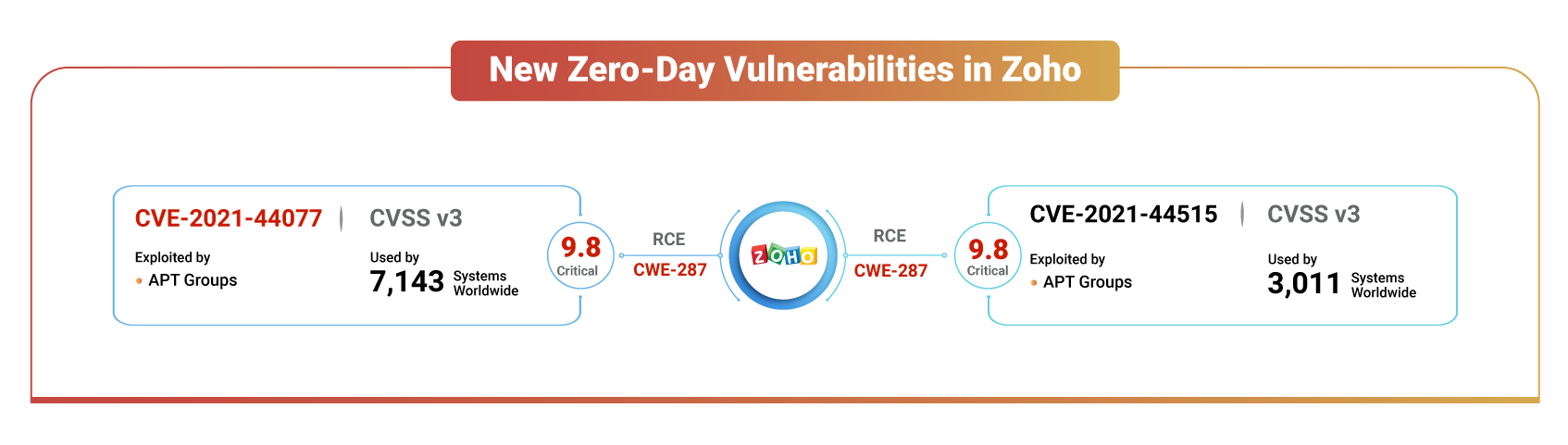
CVE-2021-44077
-
CVE-2021-44077 is a remote code execution vulnerability in ManageEngine ServiceDesk Plus that is triggered by a security misconfiguration.
-
This zero-day has been issued a CVSS v3 score of 9.8 (critical), impacting on-premises deployments up to version 11306.
-
Described as CWE-287 leading to Improper Authentication, which is the 14th most dangerous software weakness according to the 2021 CWE Top 15 Most Dangerous Software Weaknesses released by MITRE.
-
On December 02, 2021, CISA and FBI published an advisory to outline the cyber threat associated with active exploitation.
-
On December 15, 2021, a Proof-of-Concept was released on GitHub.
-
CISA had put up a list of Indicators of Compromise (IoCs), including tactics, techniques, and procedures.
-
Scanners such as Qualys, Tenable were able to detect this vulnerability.
|
Qualys |
Tenable |
Nexpose |
|---|---|---|
|
730291 376137 |
155864 |
N/A |
Global Exposure
A quick search on Shodan reveals that there are 7,143 instances on the Internet, providing a doorway to internal networks that are exposed to the world for anyone to try to break through.
Google search interest indicates that this critical vulnerability has been trending since its discovery in countries such as Japan, the United Kingdom, the United States, and India.
CVE-2021-44515
-
CVE-2021-44515 is a critical authentication bypass vulnerability attackers could exploit to execute arbitrary code on vulnerable Desktop Central servers.
-
Issued a CVSS v3 score of 9.8 (critical) and a manifestation of CWE-287 (Improper Authentication), demonstrating its seriousness.
-
According to the Shodan search engine, 3,011 instances of ManageEngine Desktop Central are exposed to the Internet, with around 41% of the instances being found in the United States alone.
It is recommended that organizations upgrade their ManageEngine Desktop Central installations as soon as possible in order to prevent potential threats.
Vulnerable Products
|
CVE ID |
Affected Products |
|---|---|
|
CVE-2021-44077 |
Zoho ManageEngine Service Desk version upto 11305, Service Desk Plus MSP version upto 10529, SUpportCenter Plus version up to 11013 |
|
CVE-2021-44515 |
Zoho ManageEngine Desktop Central version 10.1.2127.17 and below and 10.1.2128.0 to 10.1.2137.2, AssetExplorer versions upto 6952 |
Indicators of Compromise (IoCs)
|
Type |
Values |
|---|---|
|
Hashes |
Webshell: 67ee552d7c1d46885b91628c603f24b66a9755858e098748f7e7862a71baa015 068D1B3813489E41116867729504C40019FF2B1FE32AAB4716D429780E666324 759bd8bd7a71a903a26ac8d5914e5b0093b96de61bf5085592be6cc96880e088 262cf67af22d37b5af2dc71d07a00ef02dc74f71380c72875ae1b29a3a5aa23d a44a5e8e65266611d5845d88b43c9e4a9d84fe074fd18f48b50fb837fa6e429d ce310ab611895db1767877bd1f635ee3c4350d6e17ea28f8d100313f62b87382 75574959bbdad4b4ac7b16906cd8f1fd855d2a7df8e63905ab18540e2d6f1600 5475aec3b9837b514367c89d8362a9d524bfa02e75b85b401025588839a40bcb Dropper: ecd8c9967b0127a12d6db61964a82970ee5d38f82618d5db4d8eddbb3b5726b7 Implant: 009d23d85c1933715c3edcccb46438690a66eebbcccb690a7b27c9483ad9d0ac 083bdabbb87f01477f9cf61e78d19123b8099d04c93ef7ad4beb19f4a228589a 342e85a97212bb833803e06621170c67f6620f08cc220cf2d8d44dff7f4b1fa3 NGLite Backdoor: 805b92787ca7833eef5e61e2df1310e4b6544955e812e60b5f834f904623fd9f 3da8d1bfb8192f43cf5d9247035aa4445381d2d26bed981662e3db34824c71fd 5b8c307c424e777972c0fa1322844d4d04e9eb200fe9532644888c4b6386d755 3f868ac52916ebb6f6186ac20b20903f63bc8e9c460e2418f2b032a207d8f21d 342a6d21984559accbc54077db2abf61fd9c3939a4b09705f736231cbc7836ae 7e4038e18b5104683d2a33650d8c02a6a89badf30ca9174576bf0aff08c03e72 KDC Sponge: 3c90df0e02cc9b1cf1a86f9d7e6f777366c5748bd3cf4070b49460b48b4d4090 b4162f039172dcb85ca4b85c99dd77beb70743ffd2e6f9e0ba78531945577665 e391c2d3e8e4860e061f69b894cf2b1ba578a3e91de610410e7e9fa87c07304c Malicious IIS Module: bec067a0601a978229d291c82c35a41cd48c6fca1a3c650056521b01d15a72da Renamed WinRAR: d0c3d7003b7f5b4a3bd74a41709cfecfabea1f94b47e1162142de76aa7a063c7 Renamed csvde: 7d2780cd9acc516b6817e9a51b8e2889f2dec455295ac6e6d65a6191abadebff |
|
Domains |
seed.nkn[.]org |
|
Filepaths |
C:\ManageEngine\ServiceDesk\bin\msiexec.exe C:\ManageEngine\ServiceDesk\lib\tomcat\tomcat-postgres.jar C:\Windows\Temp\ScriptModule.dll C:\ManageEngine\ServiceDesk\bin\ScriptModule.dll C:\Windows\system32\ME_ADAudit.exe c:\Users\[username]\AppData\Roaming\ADManager\ME_ADManager.exe %ALLUSERPROFILE%\Microsoft\Windows\Caches\system.dat C:\ProgramData\Microsoft\Crypto\RSA\key.dat c:\windows\temp\ccc.exe |
CISA added CVE-2021-44515 and CVE-2021-44077 to its Known Exploited Vulnerabilities Catalog on December 10, encouraging federal agencies to patch it by December 25, 2021, under Binding Operational Directive 22-01. To discover any compromises in their system, Zoho has provided additional details and a downloadable exploit detection tool. We urge users to patch these Zoho vulnerabilities as soon as possible.









