Securin’s expert has discovered a zero-day vulnerability with medium severity in Tenable’s Nessus Professional scanner. This bug has been identified as ‘Sensitive Information Disclosure,’ given the CVE identifier of CVE-2022-28291, and has a severity score of 6.5 in CVSS V3. This vulnerability has been mapped to the weakness enumeration CWE-522 (Insufficiently Protected Credentials).
How Could This Vulnerability Be Exploited?
CVE-2022-28291 allows an attacker to access credentials stored in Nessus Scanners, thus potentially compromising its customers’ network of assets. An authenticated user with debug privileges can retrieve Nessus policy credentials from the ‘nessusd’ process in cleartext through process dumping and access sensitive information. This vulnerability affects all versions of Nessus Essentials and Professional.
Proof of Concept
We tested the following vulnerability on Tenable’s Nessus Professional 10.1.1 (#61) Windows.
1. Install Nessus Essentials or Professional, log on to the scanner, and create a Nessus policy with credentials using any Credential Type (in our case, Windows).
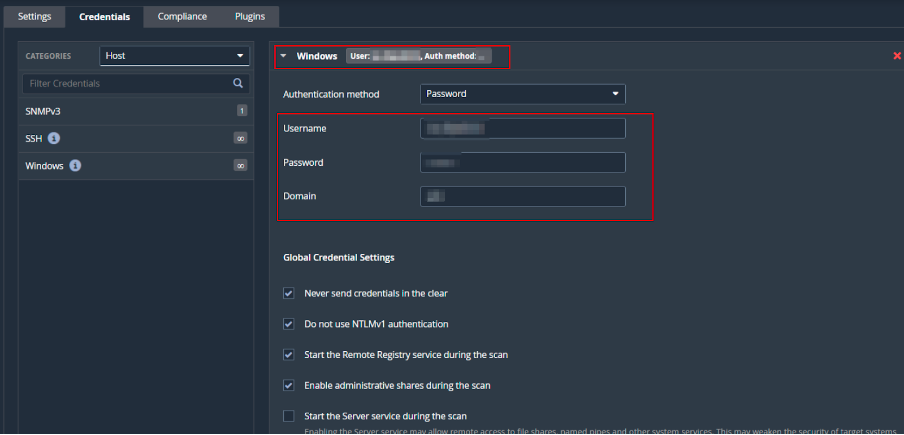
Figure 1: Creating the Nessus Policy with the Windows Credential Type
2. Run a credentialed scan using the created Nessus policy.
3. Create a process dump file of the process ‘nessusd’ from the Windows Task Manager.
.png)
Figure 2: Creating the Process Dump of the “nessusd” Process
.png)
Figure 3: Created the Process Dump of the “nessusd” Process
4. Parse the dump file (.DMP) using the Sysinternals tool “Strings” and extract information by extracting lines with the string “Login configurations.”
.png)
Figure 4: Parsing the DMP File Using Strings and Extracting Credentials
5. The Nessus policy’s Windows Domain Credentials have been retrieved in cleartext and viewed using a text editor application.
.png)
Figure 5: The Nessus Policy-Stored Windows Credentials Retrieved in Cleartext
Impact of the Vulnerability
- An attacker can retrieve stored credentials in Nessus Policies in cleartext from the “nessusd” process.
- An attacker can potentially compromise corresponding assets, internal domains, and networks with the retrieved credentials.
- With disclosed credentials, an attacker can potentially compromise an organization’s associated assets and networks, leading to infiltration and breach.
Timeline
- April 25, 2022: Securin’s expert discovered CVE-2022-28291 in Nessus Professional version 10.1.1 (#61)
- May 02, 2022: Reported to Tenable’s team
- June 02, 2022: Tenable proposed a potential fix in Nessus 10.4 or in a later release
- August 04, 2022: Tenable deemed the reported vulnerability as an acceptable risk
- August 31, 2022: Tenable performed additional reviews and acknowledged there would be no fix for this issue
- September 01, 2022: Tenable agreed to raise a CVE for this submission









