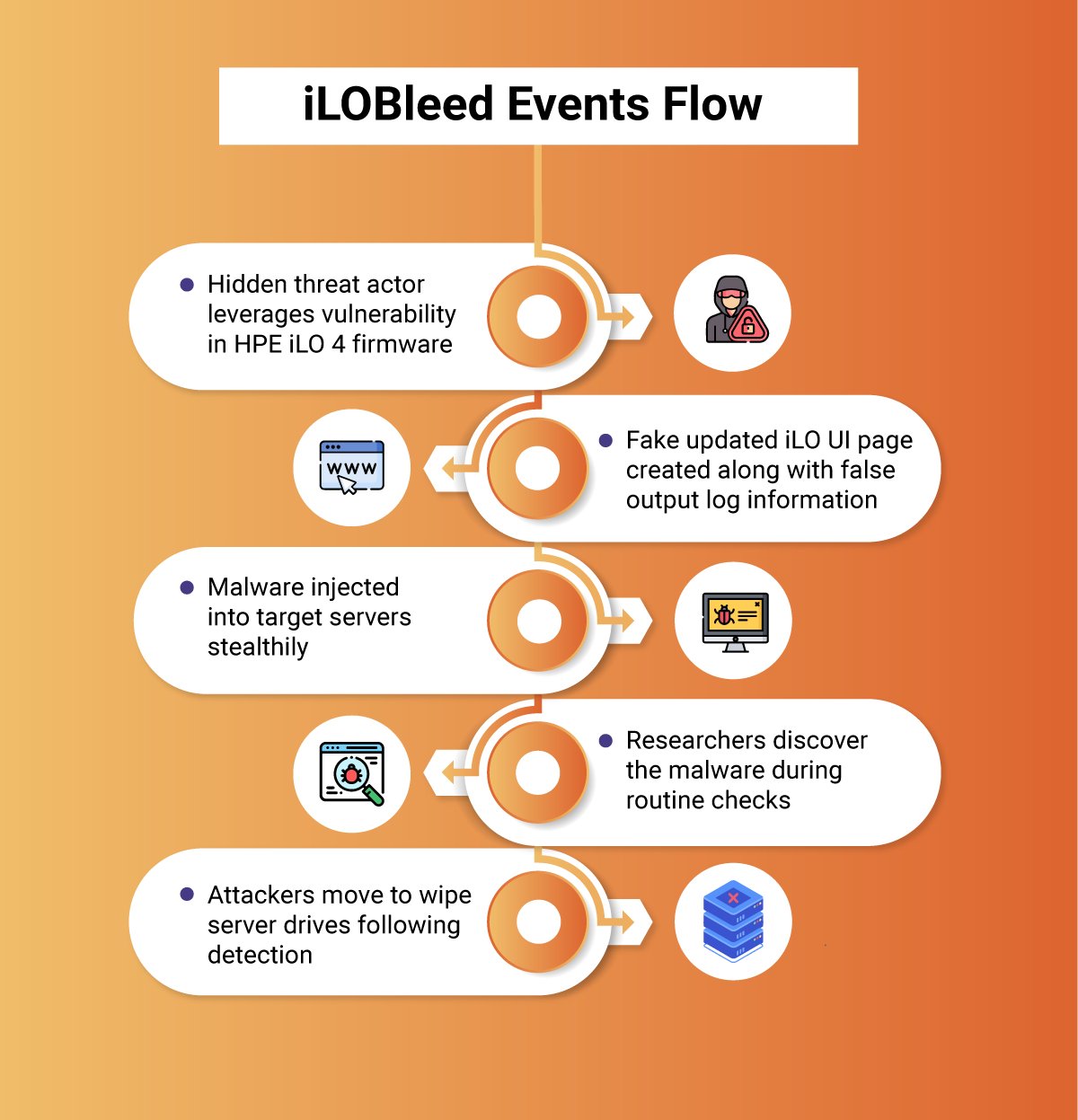
In early January 2022, a rootkit that had remained undetected in Hewlett-Packard products was discovered by an Iranian cybersecurity firm. The rootkit, dubbed iLOBleed, is an implant that targets HP Enterprise’s Integrated Lights-Out (iLO) embedded server management technology. The iLO is embedded on the motherboard of HP servers.
Although it is still uncertain which threat actor is behind the iLOBleed attacks, the sophistication it involves suggests it is most possibly an advanced persistent threat (APT) actor. That said, this attack is the first known incident of an iLO rootkit.
What is a rootkit?
A collection of malicious computer software, designed to enable access, and thereafter mask its existence, to a computer or a part of its software that is not otherwise allowed without administrator privileges.
What is the iLO firmware?
The iLO (short for Integrated Lights-Out) is a Hewlett-Packard Enterprise hardware device that can be added to servers or workstations as an add-on.
iLO devices have their own processors, storage units, RAM, as well as network cards to allow them to run separately from local operating systems.
The main role of the iLO is to provide a way for system administrators to connect to remote systems even when they are turned off, to perform maintenance tasks like upgrading firmware, installing security updates, and uninstalling or reinstalling systems.
iLOBleed-ing since 2020
The first attack leveraging the iLO firmware vulnerabilities was spotted in 2020 when an unknown threat actor compromised its targets, hid inside iLO to survive reinstalls, and maintained persistence inside the victim’s network. To avoid being detected, the attacker disguised the rootkit as an upgraded module for the iLO firmware itself and went to great lengths to craft a fake UI for the disguised module.
Fig 1: Comparison of the iLOBleed rootkit UI and the original iLO v2.55 UI
One interesting observation made by researchers was the extent to which the attackers went to wipe the data from the server on their way out of the network, as well as overwrite the iLO firmware to prevent updates that can remove the Trojan.
A Stealthy Module
Although the flaws may have been fixed in recent versions of HP firmware, it appears that an attacker can downgrade the firmware to an exploitable version. Since users cannot completely disable iLO, attackers have access to most versions, barring the Gen10 series servers which have a user-enabled non-default setting to prevent firmware downgrades.
The iLOBleed Rootkit can be delivered to target devices through a dedicated iLO network port or through a server’s operating system by a user with administrator privileges or having root access, thereby making such attacks very stealthy and highly persistent.
Fig 2: Modules affected by the malware
The Stupid-Simple Exploit
The iLO 4 firmware vulnerability is often referred to as a ‘stupid-simple exploit’ because of how easy it is to attack it. According to researchers, the vulnerability can be remotely exploited by simply raising a cURL request and typing twenty-nine “A” characters.
curl -H “Connection: AAAAAAAAAAAAAAAAAAAAAAAAAAAAA”
Vulnerability Analysis
The vulnerability that allows the iLOBleed rootkit to compromise systems is detailed below:
-
CVE-2017-12542 is a remote authentication bypass and code execution vulnerability that exists in the HPE Integrated Lights-out 4 firmware.
-
Here are the versions that the vulnerability affects:
|
cpe:2.3:o:hp:integrated_lights-out_4_firmware:*:*:*:*:*:*:*:*:2.53 |
|
cpe:2.3:h:hp:integrated_lights-out_4:-:*:*:*:*:*:*:* |
- The vulnerability has insufficient information to have a weakness enumeration associated with it, but carries a CVSS v3 score of 10 (critical).
-
The vulnerability was patched by HP in 2017. The latest advisory was shared by HPE in April 2021.
-
The proof-of-concept script for the exploit is available publicly.

Upgrade your iLO firmware now!
Several recommendations have been put out for administrators since 2017, including trying to isolate the iLO network connection from the rest of the network, maintaining regular firmware updates and iLO security scans as well as disabling firmware downgrades to older versions.
Since the iLO firmware upgrades are available, we recommend all organizations change their admin passwords, secure their iLO network, and periodically monitor their iLO firmware for infections.
CSW’s Vulnerability Management as a Service (VMaaS) offers full coverage encompassing your entire IT landscape and detects, prioritizes, fixes vulnerabilities on your organizational infrastructure and provides access to the award-winning Risk-Based Vulnerability Management platform to view all your desired results in real-time.
To know more about CSW’s Vulnerability Management as a Service (VMaaS),
please click here.