On May 07, 2021, the Colonial Pipeline that supplies fuel to the US’s east coast area went offline after it fell victim to the DarkSide Ransomware. A ransom of 75 Bitcoins amounting to $5 M was reportedly paid to the hackers. This attack demonstrates again the determined efforts of ransomware attackers to create the maximum disruption by hitting critical sectors.
Vulnerabilities Exploited by DarkSide
DarkSide operates as Ransomware-as-a-Service (RaaS), providing an affiliate service to attackers who wish to purchase ransomware to target victims. Colonial Pipeline became a victim through two vulnerabilities, and here is our analysis:
- CVE-2019-5544 is an open-source vulnerability that exists in VMware ESXi 6.5.0 and Red Hat Linux.
- CVE-2020-3992 exists in VMware ESXi 6.7.0, a hypervisor solution that allows multiple virtual machines to share the same hard drive storage.
- Both vulnerabilities have Remote Code Execution (RCE) capabilities that allow an attacker on the same network to send malicious service location protocol (SLP) requests to an ESXi device and take control of it.
- These vulnerabilities are rated critical with a CVSS V3 score of 9.8.
- The Common Weakness Enumeration (CWE) that introduced these vulnerabilities into the product are CWE-787 and CWE-416.
- They also feature in MITRE’s Top 25 as the most dangerous weaknesses.
- These vulnerabilities were highlighted in our recent Ransomware Spotlight Report.
- Our research also shows that both vulnerabilities are used by another ransomware family, the RansomExx family.
-
It is now known that DarkSide is being used by three APT groups, UNC2628, UNC2659, and UNC2465, that are currently uncategorized. These uncategorized APT groups are still under research and are yet to be mapped to existing threat groups.
Patches for both the vulnerabilities (CVE-2019-5544 and CVE-2020-3992) have been available for months and yet they are not being remediated.
Global Exposure Analysis
Our exposure analysis using Shodan indicates there are still 23,095 and 30,998 instances of VMware ESXi exposed to the internet and may be vulnerable to these attacks if they are not patched.
.png)
DarkSide MITRE ATT&CK Mapping
| MITRE ATT&CK | IOC |
|
T1112 – Modify Registry T1012 – Query Registry T1082 – System Information Discovery T1120 – Peripheral Device Discovery T1005 – Data from Local System T1486 – Data Encrypted for Impact T1543.003 – Create or Modify System Process: Windows Service T1490 – Inhibit System Recovery T1553.004 – Subvert Trust Controls: Install Root Certificate T1078 – Valid Accounts |
MD5: 9d418ecc0f3bf45029263b0944236884 |
As of May 17, DarkSide ransomware has shut down its Ransomware-as-a-Service affiliate program, bowing down to political pressure. Its servers have been seized and cryptocurrency account drained by unknown sources.
Can We Prevent Another Disruptive Ransomware Attack?
Yes! Organizations need to take a risk-based vulnerability management approach and get a ransomware assessment for their attack surface and ransomware exposure.
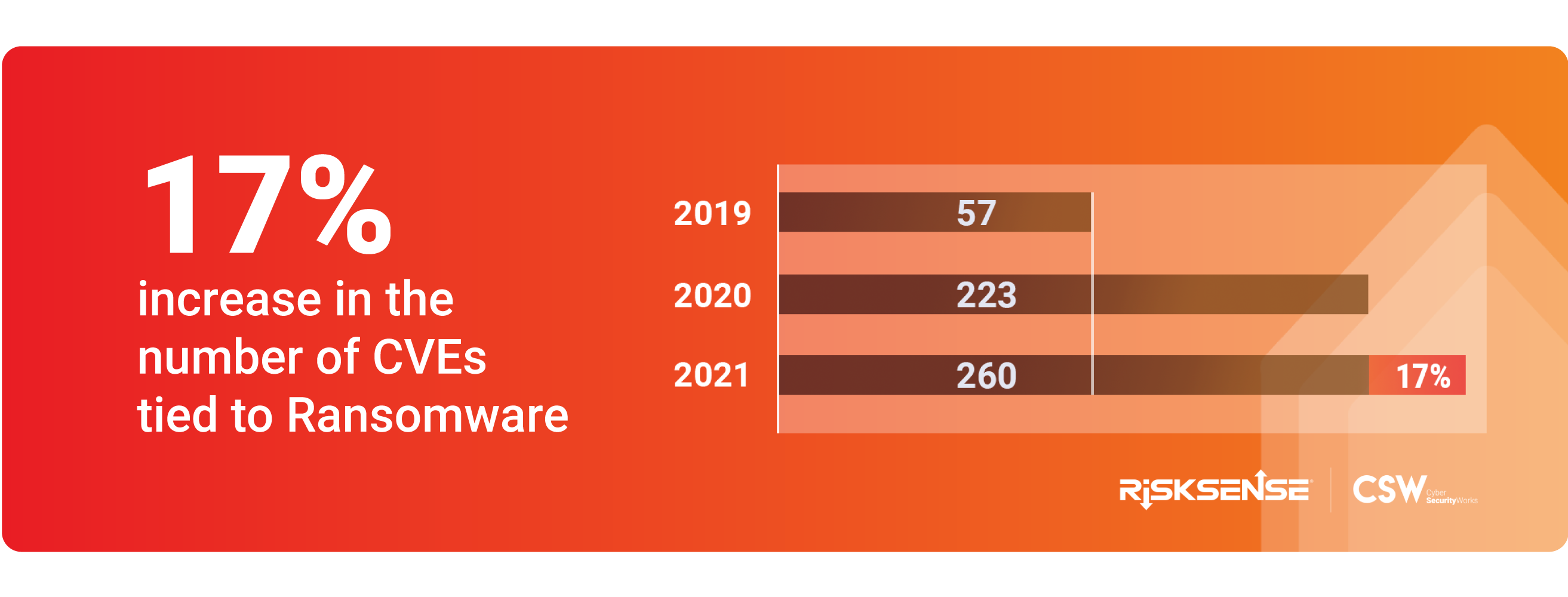
Our research shows that attackers are using 260 vulnerabilities, out of which 132 are active exploits trending right now, to deploy ransomware.
Securin’s path-breaking report Ransomware Spotlight 2021 is powered by Vulnerability Intelligence (VI), a knowledge base of vulnerabilities used by ransomware, APT groups, and nation-state actors. Enriched by Securin’s security researchers, this data is a single source of truth for ransomware, providing additional context and appropriate remediation information to fix vulnerabilities. This database also powers the Ransomware Assessment that we offer organizations to proactively identify vulnerabilities that attackers target to mount a ransomware attack!
.png)
Ransomware is evolving in new ways. Its use has become mainstream and now is offered as Ransomware as a Service. When we published our report in February 2021, the vulnerabilities associated with ransomware were 223. This number increased to 260 (17%) during the first quarter of 2021. We are seeing an overall increase in the number of active exploits, ransomware families, CWEs, new products, and vendors that are tied to ransomware.
 Our recommendation to sectors like energy, power, water, and healthcare would be to assess susceptibility to ransomware and take proactive measures to defend their attack surface from further crippling attacks.
Our recommendation to sectors like energy, power, water, and healthcare would be to assess susceptibility to ransomware and take proactive measures to defend their attack surface from further crippling attacks.
{Updated on October 18, 2021}: On October 06, 2021, researchers noticed an unnamed gang using a novel method to attack VMware ESXi servers, using an uber-fast Python script-based ransomware. The ransomware attack took less than three hours from initial access to encryption, something previously unheard of. Though the Python ransomware is just 6KB in size, it can do quite a lot of damage.
The use of a Linux variant ransomware on ESXi servers is nothing new. In July, REvil was noted for using a Linux variant to target the much-exploited ESXi vulnerabilities. That was quickly followed by HelloKitty and DarkSide ransomware. The BlackMatter ransomware group, an offspring of the DarkSide gang, was reportedly still using the Linux variant of the malware used by DarkSide to target ESXi servers.
We, therefore, urge organizations to harden the security on their ESXi servers or other hypervisors to secure and limit the attack surface.
As of today, our research has associated 260 vulnerabilities with ransomware. Remediating and patching these vulnerabilities on priority could have averted the Colonial Pipeline attack.
Get a Ransomware Assessment and avoid paying millions of dollars as ransom.










.png)