Securing Critical Workloads on AWS
Posted on Mar 16, 2022 | By Phil Manfredi
The need for a continuous and holistic AWS security approach has significantly increased as more organizations modernize their critical workloads and take advantage of AWS capabilities and services. When assessing your overall AWS security posture, it is necessary to include your internal and external infrastructure and network, applications, and AWS environment configurations. Proven risk-based cybersecurity programs that traditionally included Penetration Testing and Vulnerability Scanning are now expanding to include services such as Attack Surface Management and Cloud Security Management.
AWS Shared Responsibility Model
When considering AWS security, it is crucial to understand whether you or AWS is responsible for security. The short answer is the responsibility falls on both you and AWS. AWS calls it the Shared Responsibility Model, in which AWS is responsible for the security OF the cloud, while the customer is responsible for the security IN the cloud.
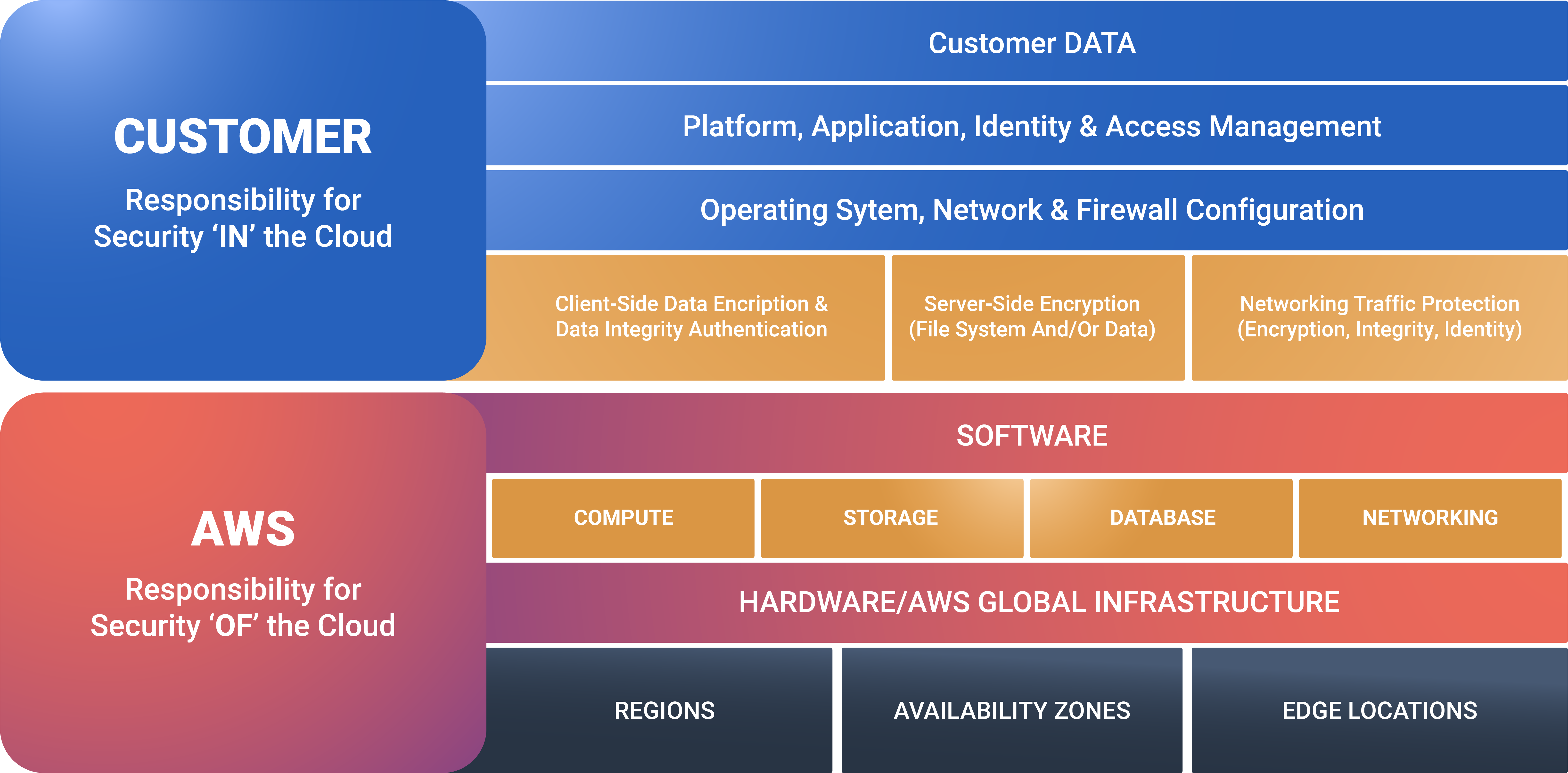
Figure 1: AWS Shared Security Model
Although AWS does a good job of ensuring that various parts of your environment are secure, there are plenty of opportunities for security gaps to occur if you do not know what you are doing. One issue we often notice when conducting an AWS Cloud Security Assessment is that an engineer has accidentally set an S3 bucket open to the public and exposed critical data without being aware of the vulnerability.
With this shared model in mind, let us break down the four critical areas that you need to assess to ensure that your critical workloads are secure on AWS.
-
External Infrastructure
When hardening your AWS security posture, it is most important to first assess your external infrastructure because it has the greatest exposure to the public. When assessing your external infrastructure, identify your known and unknown public-facing exposures, including networks, applications, databases, and cloud configurations.
Starting with an attack surface assessment, you can quickly discover all your public-facing digital assets, determine the location of known vulnerabilities and exposures, and then prioritize remediation based on the criticality of those vulnerabilities.
Organizations have massive attack surfaces, yet most continue to defend their attack surface using the same methods used a decade ago. Unlike traditional methods, modern attack surface assessments include known and unknown inventories, shadow IT resources, data leakage, APIs, integrations, supply chain or third-party risk assessments, code repositories, and more.
The next step is to perform an external Network Vulnerability Assessment and Penetration Test (VAPT) on your external infrastructure. Attackers are constantly trying to detect a vulnerability in your external network that can easily be used to gain privileged access to your systems. To stay ahead of attackers, organizations need to determine precisely how vulnerable their external networks and interfaces are. They also need to evaluate if their existing security policies can help them effectively uncover and fix any unknown vulnerabilities before a data breach occurs.
When it comes to a penetration test or pentesting, AWS has a support policy that allows you to test specific AWS services without prior approval. However, there are also specific terms and conditions that you must follow when performing security assessments. Therefore, it is critical that you, or your security partner, have a strong understanding of AWS and what’s Permitted vs. Prohibited when pentesting your AWS environment.
-
Hosted Applications
Companies around the world leverage AWS for hosting websites, mobile applications, and other critical workloads developed either internally or by a third party. As many of these applications are meant to be publicly available by design, vulnerabilities in these applications are ideal targets for hackers to attempt to exploit.
The best way to assess the security of your applications is to perform an Application Vulnerability and Penetration Test to evaluate how hackers could target your application’s development components, core functionalities, or features. A thorough test can discover multiple attack vectors by sending or inputting data to user interfaces, network interfaces, application programming interfaces (APIs), and other places where inputs are processed. To ensure that the deepest possible analysis is conducted, engage with security analysts to perform manual testing alongside whatever automated scanning tools are available.
-
Internal Infrastructure
The next layer to be assessed to ensure that your critical workloads are secure is your internal infrastructure. If attackers make it through your external controls, they will then try to detect a vulnerability in your internal attack surface, which can be utilized for malware propagation across your network. To stay ahead of attackers, evaluate the effectiveness of your internal security controls and interfaces. You will also need to determine whether your existing security policies are capable of uncovering unknown vulnerabilities while ensuring that you fix these gaps before a data breach occurs.
Although AWS provides tight network controls by default, you still might want to consider undergoing an internal Network VAPT, especially if you have a hybrid environment of AWS and on-premise. However, what may be more effective, is to have an AWS configuration assessment performed to ensure that you are following AWS security best practices.
-
AWS Security Assessment
The best way to ensure you are following AWS best practices is to have an independent third party perform a security assessment of your AWS environment, including an AWS Well-Architected Review. Although you can do a high-level review on your own, having an AWS partner with AWS-certified engineers do a manual check of your environment will give you a deeper level of assurance.
Be sure that any vendor you utilize to conduct an AWS security review focuses on these major areas: network and core infrastructure, identity and access management, incident response and management, and data protection and custom workloads.
Also, ensure that the vendor does not simply provide a generic report of their findings. The real value comes if they provide detailed reports of what they found, specifically calling out any critical issues and then including a recommended list of prioritized remediation items to help you fix the discovered vulnerabilities. This will help you know how and where to address the most critical security vulnerabilities in your AWS environment.
Conclusion
When securing your critical workloads on AWS, there are a multitude of factors that could potentially make you the victim of a cyberattack. However, using a structured approach and leveraging cybersecurity best practices can save you from future attacks and having to make expensive reparations. Keep in mind that the cloud systems you are building today are not going to be the same systems you will be running in the future. Therefore, to most effectively ensure that your organization is as secure as possible, you must continuously and systematically assess your core infrastructure, applications, and AWS environment.
Independent assessments of your information and critical infrastructures that focus on the malicious intent of adversaries will help to bolster your company’s security posture and mitigate potential damage. Attack Surface Management, Vulnerability Assessments, Pentesting, and AWS Security Assessments are all tools that will help identify and prioritize where you have the greatest risk.
Never miss a patch or an update with CSW’s Patch Watch Newsletter. Subscribe now!

