Why Should Schools Prioritize Cybersecurity?
Posted on Jul 4, 2022 | Updated on Sep 21, 2022 | By Supriya Aluri
Of all the sectors that are under threat from cyber attacks, education has the most serious challenges to overcome. Lack of resources and funding, combined with the usage of legacy systems, is enabling cyber attackers to disrupt the day-to-day operations of schools while stealing valuable information from school networks to ransom them for amounts that the schools could ill afford.
Ransomware incidents cause significant damage in terms of finances, reputation, and data security. In 2021 US schools lost $3.56 billion due to ransomware attacks and in two cases it led to the shutting down of two educational institutions for good.
In the following blog, we provide a snapshot of how CSW is helping schools gain resilience against cyber attacks and evolving threats and what schools can do to stay safe from ransomware attacks.
How CSW is helping a US State School District improve its security posture
Here are the results of an assessment that CSW conducted for a US state’s educational department.
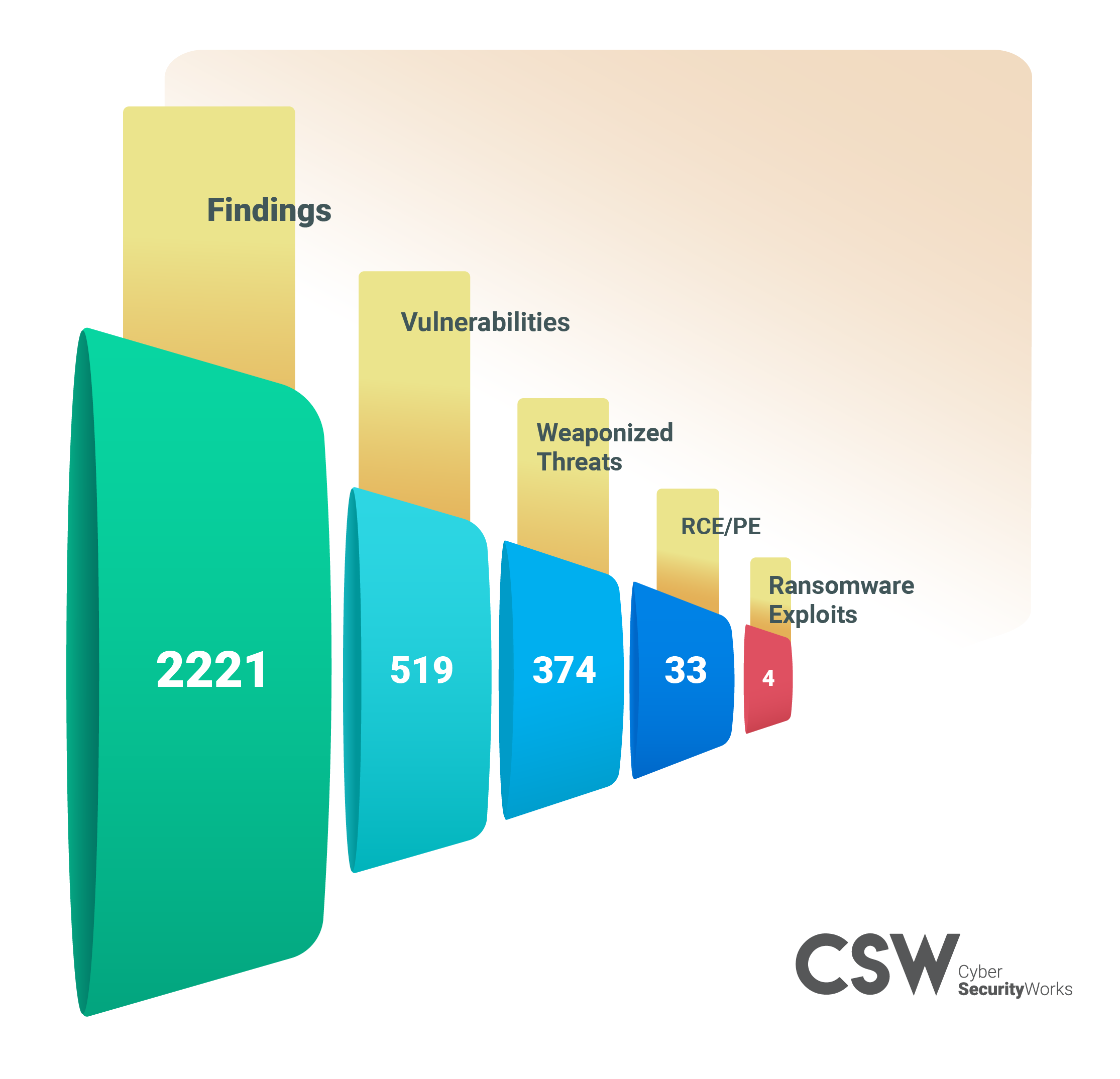
We investigated 188 district and charter schools for the state and scanned 1172 assets. Here is what we found: Among the 1172 assets discovered, there were 2221 findings with 519 unique vulnerabilities.
Weaponized Vulnerabilities: We also found that 374 vulnerabilities are weaponized and can be exploited by attackers to gain access to the school systems and steal data.
Based on our AI and ML-based predictive analysis, CSW researchers warn that 78 (17%) of the existing vulnerabilities are most likely to be exploited by malicious actors and need to be remediated immediately.
RCE/PE Vulnerabilities: We identified and prioritized 33 RCE/PE vulnerabilities that needs to be remediated immediately as they allow hackers to remotely execute malicious code. If left unchecked, data loss and access loss are imminent.
Ransomware-associated Vulnerabiltiies: Three of the district schools have vulnerabilities that have known ransomware exploitation instances:
-
CVE 2019-11043 associated with NextCry ransomware. This ransomware encrypts files on the NextCloud servers. This is a trending PHP CVE which has maximum possibility of exploitation in schools and NAS devices. Our recommendation to schools was to upgrade to PHP version 7.3.11 and to remediate the vulnerability immediately.
-
CVE-2021-34473 associated with Lockfile, BlackByte and Conti ransomware groups. Our research also shows that the Conti and Lockfile groups are actively being deployed by APT groups like Wizard Spider, Exotic Lily and DEV-0401 to attack prominent organizations.
-
CVE-2018-19943, a command injection vulnerability, and CVE-2018-19949 associated with eCh0raix Ransomware
Vulnerabilities on CISA KEV list: 374 of the discovered vulnerabilities are on the CISA-KEVs list which contains a list of vulnerabilities that have known instances of exploitation.
Vulnerability Aging: 22% of the vulnerabilities could potentially be present in systems since 2001 (based on the vulnerability age), which is extremely dangerous as there are many attack methodologies readily available and refined over the years. Interestingly, 45% of the exploits have cropped up in the last six years.
As a result of CSW’s asset scan and exposure prioritization, 30 out of 74 schools performed remediation on open weaponized vulnerabilities and improved their security posture.
Four overlooked exposures that schools should look for
A cyber attack can result from multiple different exposures introduced into organizational attack surfaces. These can easily be discovered, if you know what to look for.
Let’s look at some of the possible attack methods that have been utilized in recent years.
-
Unpatched Vulnerabilities: In the above section, we noticed how Pysa and Sabbath ransomware groups were among those that exploited unpatched vulnerabilities in school networks to seize their systems.
-
Connected Devices: Malicious actors take advantage of connected devices to deploy botnets and malware, and stealthily invade networks.
-
Exposures in Third-Party Software: This is probably one of the most overlooked dangers that can compromise school networks. A vulnerability in a third-party application used by schools can lead to educational institutions being caught unawares when exploited. Here are a few examples of how these can be used against you -
-
CVE-2022-1609, a critical vulnerability was observed in School Management Pro, a WordPress plugin with over 3,40,000 customers, exploitation of which could allow complete control of school websites
-
A breach of Illuminate’s eduCLIMBER, an academic progress monitoring tool, exposed personal data of 1700 students. Earlier, the New York City Department of Education was also impacted by the breach exposing data of 820,000 current and former students, and was touted to be the single largest data breach of student data.
-
Around 30,000 WordPress hosted university websites in Ukraine were hacked as part of the Russia-Ukraine war; nearly 100,000 attacks in 24 hours.
-
A ransomware attack on a leading school website services provider disrupted servers and the regular functioning of thousands of schools using the SaaS service.
-
Critical zero-day vulnerabilities were found in Fedena, a now-abandoned software used for school management.
-
Personal information of around 500,00 students and 60000 staff in Chicago Public Schools was stolen in a ransomware attack on the K-12 technology vendor Battelle for Kids.
-
-
Exposures introduced by misconfigurations: Mistakes while configuring assets or network-related parameters can be costly, as some schools found out when their databases were compromised.
-
Misconfigured certificates in Eduroam, a free Wi-Fi network used by many universities, exposed the credentials of multiple users.
-
-
Data leak due to incorrect access configuration allowed access to a Google Drive that contained the private information of 3000 students and 100 department employees across New York City.
While the above list is by no means complete, it gives us a good idea of the number of exposures that exist in school networks even as we write this.
Current State of Cybersecurity in US Schools
Even while we worked with the above-mentioned US state school, attacks on prominent public schools and colleges were happening.
|
Time Period |
School |
Region |
Incident |
Impact |
|---|---|---|---|---|
| September 2022 | LAUSD | Los Angeles | Ransomware Attack | Vice Society, a ransomware group claimed to have stolen files from compromised LAUSD systems before encrypting them with ransomware. |
| August 2022 | Whitworth University | Washington | Ransomware Attack | Whitworth University suffered a severe ransomware attack from the LockBit group. Students' and staff PII were stolen in this attack |
| July 2022 | Cedar Rapids Schools | Iowa | Ransomware Attack | Cedar Rapids had to pay a huge ransom to keep the personal data of staff and students from being exposed. |
|
June 2022 |
Tenafly Public Schools |
New Jersey |
NJ district public schools canceled all final exams after their systems were encrypted by malicious agents. |
|
|
December 2021 - May 2022 |
Lincoln College |
Illinois |
157 year old college had to shut down |
|
|
May 2022 |
North Orange County Community College District |
California |
19,000 students’ and staff’s data breached. |
|
|
December 2021 |
Chicago Public Schools |
Chicago |
Personal information of around 500,00 students and 60000 staff stolen |
|
|
October 2021 |
A US School district |
- |
Multi million dollar ransom demanded along with triple extortion. |
|
|
September 2021 |
Lufkin Independent School District |
Texas |
Several systems shut down disrupting services |
|
|
September 2021 |
Dallas Independent School District |
Texas |
Sensitive personal data of students were exposed |
|
|
August 2021 |
K-12 schools |
Eight schools hit |
||
|
July 2021 |
Public Schools |
Monroe |
- |
|
|
June 2021 |
Judson Independent School District |
Texas |
computer and communication systems were paralyzed |
A look at the attacks listed shows that over 50% of these incidents spiraled quickly into full-fledged ransomware attacks. Research shows that, in the US alone, over 1043 schools and colleges were subjected to 77 individual ransomware attacks in 2021. When a school is exposed to a ransomware attack, it has dire financial consequences, and data breaches that lead to exposing of confidential information about students can lead to identity theft. Check out the tweet given below, to see how disruptive it can be for students and the institution as well.
A student affected by the Sutherland cyber attack
Our research also notes two threat actors - APT 1 (China-based cyber-espionage group) and Tilted Temple are targeting the education sector, primarily in the US.
Five things that schools can do to safeguard themselves
Schools are an easy target for cyber criminals because of the following reasons:
-
An abundance of sensitive information (social security numbers, medical files, family information, and academic records) left open to the internet.
-
Not enough network defenses to safeguard data.
-
No periodic checks to discover vulnerabilities.
While many schools have been made examples with countless cyber attacks carried out against them, we do not see a proper response from the decision makers. It is high time authorities step up and take measures to curb the attacks, and the consequential impact to millions of students around the globe.
-
Keep up to date with the K-12 cybersecurity act and other advisories.
-
Implement CISA KEV and advisory patch recommendations sooner rather than later.
-
Deploy adequate resources to timely monitor the security situation of schools regularly.
-
Perform routine checks and apply remediation measures immediately. If possible, automate this process.
-
Have a contingency plan for when your systems are under attack
A penetration test helped the University of Kentucky discover a data breach that was the result of a vulnerability in a web-based portal developed by the university.
CSW provides various tools such as Attack Surface Management, VMaaS, pentesting as a Service, and Ransomware Assessment to help protect against various types of cyber attacks. You can reach out to us to understand the specific tools that would cater to your organization’s needs.
Sign up for a free trial for ASM
Never miss a patch or an update with CSW's Patch Watch Newsletter. Subscribe now!

